Why Perform A Vulnerability Assessment?

2 Minutes 56 Seconds | 3136 views
Listen This Blog Now!
What Is Vulnerability Assessment?
A vulnerability assessment is a thorough evaluation of the security weaknesses in an information system. It determines whether the system is vulnerable to any known vulnerabilities, assigns severity levels to those vulnerabilities, and provides remedy or mitigation if and when necessary.
Other error or weakness in the system's security procedures, design, implementation, or any internal control that could lead to a violation of the system's security policy is referred to as a vulnerability.
Why Perform a Vulnerability Assessment?
There are various advantages to conducting a vulnerability assessment, including:
- Detecting flaws before they are exploited by hackers. Vulnerability assessment examines all network components to see if they have any flaws that cybercriminals could exploit to attack the company.
- Evaluating third-party IT service providers' performance. An independent Vulnerability assessment can assist you in cross-checking the performance of third-party suppliers for IT products such as email, backup, and system administration if you rely on them.
- Following the industry and regulatory guidelines. A diligent Vulnerability assessment can help you stay compliant if you work in a regulated industry. is also necessary for obtaining and maintaining security certifications like ISO 27001.
- Time and money are saved. Security breaches can harm a business in a variety of ways, resulting in costly limitations and liabilities. Vulnerability assessment reduces such risks, letting the company save time and money by avoiding costly data breach lawsuits.
Three Key Steps Of The Vulnerability Testing Process That Must Follow
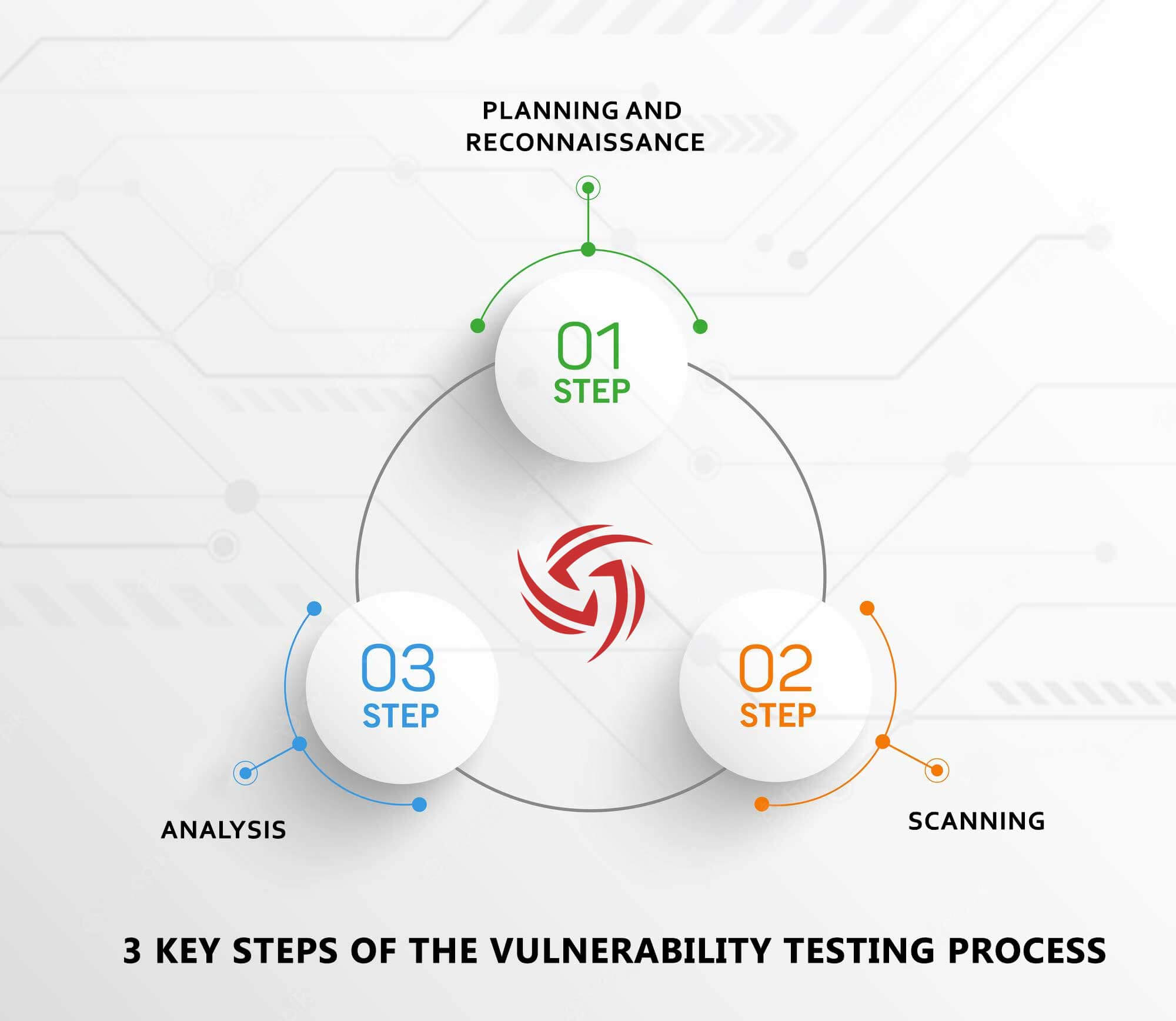
#1. Planning and Reconnaissance
The vulnerability testing method’s planning and reconnaissance step is like the preparation stage. The main goal of this step is to define the test's scope and objectives. In addition, the testing methods and systems that will be handled are highlighted. Critical online applications, significant IT infrastructure, and other critical systems should all be prioritized. It's worth noting that the laid-out design must include all the major systems and networks. It should also ensure that all vital company data is protected.
#2. Scanning
Scanning the system or network is the next phase in the procedure. It can be accomplished using either manual or automated tools. Identification of open FTP portals, operating services, open shared drives, and other tasks are conducted during this stage.
#3. Analysis
The analysis step appears later in the vulnerability testing procedure. The causes of vulnerabilities, their impact, and treatments are described in length here. Vulnerabilities can also be ranked according to their severity and the potential damage they could create in the event of a breach. Key discoveries are routinely provided later in the process in order to start an appropriate follow-up plan.
Types of a Vulnerability Scanners

Host-Based
- Identifies problems with the host or system.
- The process is completed by using host-based scanners to identify and diagnose vulnerabilities.
- The host-based tools will install a mediator programmed on the target machine, which will track the occurrence and alert the security analyst.
Database-Base
- It will use tools and techniques to uncover security vulnerabilities in database systems and prevent SQL Injections. (SQL Injections: - Malicious users inject SQL statements into a database, allowing them to read sensitive data from the database and edit the data in the database.)
Network-Based
- It will discover open ports and identify any unfamiliar services that are using them. It will then reveal any potential vulnerabilities linked with these services.
- Network-based Scanners are used in this process.
Wireless scanners
- Wireless vulnerability scanners are used to identify rogue access points and guarantee that a company's network is properly configured.
Application scanners
- Websites are scanned for known software vulnerabilities and incorrect setups in-network or online applications using application vulnerability scanners.
Why CyberNX?
Our Vulnerability Assessment services employ modern tools to identify threats to your company's infrastructure, as well as new internal and external vulnerabilities, and to prevent unauthorized access. . We detect false positives and remove them and also provide an actionable report. Our trained security testing specialists examine the vulnerability findings and write a report that includes crucial suggestions and threat guidance to organizations. To know more Visit our Vulnerability Assessment page.
Table Of Content
- What Is Vulnerability Assessment?
- Why Perform A Vulnerability Assessment?
- Three Key Steps Of The Vulnerability Testing Process
- Planning and Reconnaissance
- Scanning
- Analysis
- Types of a Vulnerability Scanners
- Host-Based
- Database-Base
- Network-Based
- Wireless Scanners
- Application Scanners
- Why CyberNX?
What Is Vulnerability Assessment?
A vulnerability assessment is a thorough evaluation of the security weaknesses in an information system. It determines whether the system is vulnerable to any known vulnerabilities, assigns severity levels to those vulnerabilities, and provides remedy or mitigation if and when necessary.
Other error or weakness in the system's security procedures, design, implementation, or any internal control that could lead to a violation of the system's security policy is referred to as a vulnerability.
Why Perform a Vulnerability Assessment?
There are various advantages to conducting a vulnerability assessment, including:
- Detecting flaws before they are exploited by hackers. Vulnerability assessment examines all network components to see if they have any flaws that cybercriminals could exploit to attack the company.
- Evaluating third-party IT service providers' performance. An independent Vulnerability assessment can assist you in cross-checking the performance of third-party suppliers for IT products such as email, backup, and system administration if you rely on them.
- Following the industry and regulatory guidelines. A diligent Vulnerability assessment can help you stay compliant if you work in a regulated industry. is also necessary for obtaining and maintaining security certifications like ISO 27001.
- Time and money are saved. Security breaches can harm a business in a variety of ways, resulting in costly limitations and liabilities. Vulnerability assessment reduces such risks, letting the company save time and money by avoiding costly data breach lawsuits.
Three Key Steps Of The Vulnerability Testing Process That Must Follow

#1. Planning and Reconnaissance
The vulnerability testing method’s planning and reconnaissance step is like the preparation stage. The main goal of this step is to define the test's scope and objectives. In addition, the testing methods and systems that will be handled are highlighted. Critical online applications, significant IT infrastructure, and other critical systems should all be prioritized. It's worth noting that the laid-out design must include all the major systems and networks. It should also ensure that all vital company data is protected.
#2. Scanning
Scanning the system or network is the next phase in the procedure. It can be accomplished using either manual or automated tools. Identification of open FTP portals, operating services, open shared drives, and other tasks are conducted during this stage.
#3. Analysis
The analysis step appears later in the vulnerability testing procedure. The causes of vulnerabilities, their impact, and treatments are described in length here. Vulnerabilities can also be ranked according to their severity and the potential damage they could create in the event of a breach. Key discoveries are routinely provided later in the process in order to start an appropriate follow-up plan.
Types of a Vulnerability Scanners

Host-Based
- Identifies problems with the host or system.
- The process is completed by using host-based scanners to identify and diagnose vulnerabilities.
- The host-based tools will install a mediator programmed on the target machine, which will track the occurrence and alert the security analyst.
Database-Base
- It will use tools and techniques to uncover security vulnerabilities in database systems and prevent SQL Injections. (SQL Injections: - Malicious users inject SQL statements into a database, allowing them to read sensitive data from the database and edit the data in the database.)
Network-Based
- It will discover open ports and identify any unfamiliar services that are using them. It will then reveal any potential vulnerabilities linked with these services.
- Network-based Scanners are used in this process.
Wireless scanners
- Wireless vulnerability scanners are used to identify rogue access points and guarantee that a company's network is properly configured.
Application scanners
- Websites are scanned for known software vulnerabilities and incorrect setups in-network or online applications using application vulnerability scanners.
Why CyberNX?
Our Vulnerability Assessment services employ modern tools to identify threats to your company's infrastructure, as well as new internal and external vulnerabilities, and to prevent unauthorized access. . We detect false positives and remove them and also provide an actionable report. Our trained security testing specialists examine the vulnerability findings and write a report that includes crucial suggestions and threat guidance to organizations. To know more Visit our Vulnerability Assessment page.
Share this on: