Evaluate Your Team’s Phishing Defenses with
Phishing Simulation Services
Strengthen your defence against real-world phishing techniques with our comprehensive Phishing Simulation Services.
Talk to our Experts Today
INTRODUCTION
Human Firewall Against Phishing Attacks
Employees are the human firewall of an organization.So assessing their ability to defend against phishing attempts is crucial. Email remains a primary threat vector for malicious actors seeking to steal data, gain financial access, or deploy ransomware. With one-third of ransomware attacks arriving via email, untrained employees can create significant risk when a malicious email gets through.

We address your key challenges:
Employees' Response to Phishing
Organizations need to understand how employees respond to sophisticated phishing attacks as they face these threats continuously.
Continuously Assess and Train
To combat sustained and targeted attacks, organizations must identify susceptible employees and provide targeted training to protect them from such threats.
Identify Repeat Offenders
It is essential to pinpoint employees who repeatedly fall victim to phishing attempts and take corrective actions.
Identify Areas for Improvement
Organizations must identify areas for enhancing their overall security strategy and posture.
PROCESS
How It Works?
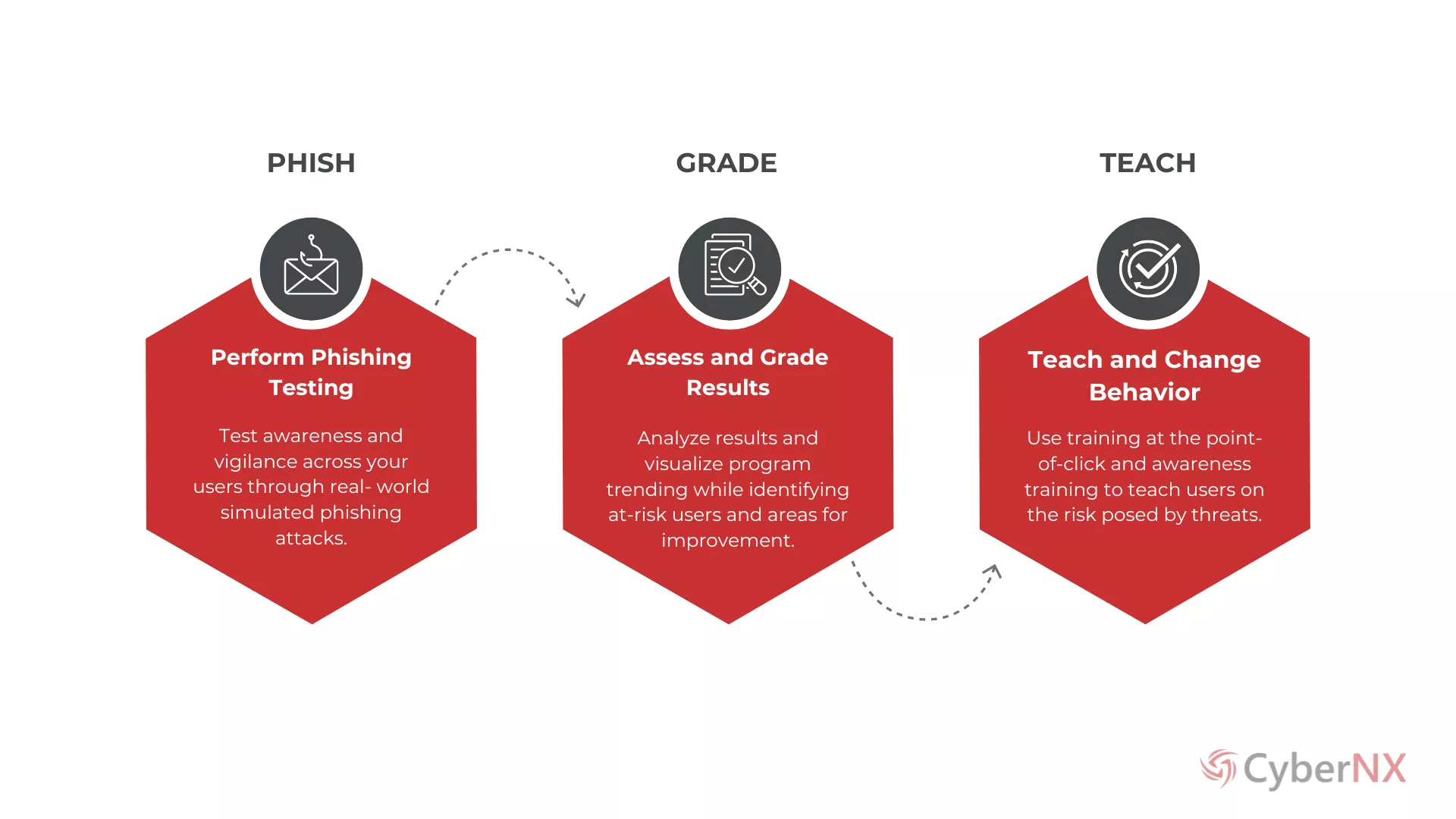
APPROACH
Phishing Simulation Services:
What Sets CyberNX Apart?
CyberNX’s Phishing Simulation Services are designed to strengthen your organization’s defense against sophisticated phishing attacks.
01
Customized Simulations
Tailored phishing simulations to meet specific needs and schedules and improve employee readiness.
02
Extensive Reporting
Detailed reports tailored to organizational requirements for comprehensive analysis & actionable insights.
03
Skilled Professionals
Benefit from the professionals who have conducted numerous phishing exercises for a variety of clients.
04
Realistic Simulations
Realistic phishing scenarios – deceptive emails, spoofed websites & other techniques used by cybercriminals.
05
Ongoing Support
Access ongoing support to implement recommended security measures and enhance training programs.
Looking for Phishing Simulation Services? Connect with our Team of Security Specialists!
BENEFITS
Customized Phishing Simulation Services
Multichannel Phishing Simulations
Test and track user responses using various channels. Our customized simulations help identify your workforce's training needs instantly.
Advanced Phishing Simulations
Simulate email, spear phishing, and ransomware attacks using our extensive phishing template repository for tailored campaigns.
Statistics and Reporting
Get detailed, actionable reports on employee behavior towards phishing attempts. Monitor responses to identify and improve weak areas.
Security Awareness Programs
Customize our information security training programs based on simulation insights to target specific threats and employee groups.
SaaS-Delivered
Benefit from our expertise in phishing techniques and threat patterns delivered through a convenient SaaS platform.
Testimonials
Customer first Approach is our guiding principle.
We listen, adapt, and deliver solutions that empower your success.
The leadership and team are committed to delivering exceptional quality and top-notch
customer service.
CIO of One of India’s Top Fund House
Top-notch MDR service with exceptional alert quality and brilliant response.
CISO, One of India’s biggest Law Firms
Peregrine MDR provides thorough, 24/7 monitoring of our environment, ensuring constant
vigilance and response.
CIO, Leading Fintech Company
We are highly impressed with CyberNX's PinPoint Red Teaming Services for their precision and
effectiveness in identifying security vulnerabilities.
CISO of a Leading Pharma
The MSP247 Team's commendable multi-cloud skills enable them to manage complex cloud
environments with expertise and efficiency.
Head Infrastructure of a Leading NBFC
CyberNX's nCompass GRC team stands out as one of the most experienced and skilled
teams I've had the opportunity to work with.
CISO, India’s Largest cash management company RESOURCES
Cyber Security Knowledge Hub
Explore our resources section for insightful blogs, articles, infographics and case studies, covering everything in Cyber Security.
For Customized Plans tailored to Your Needs,
Get in Touch Today!
FAQ
Frequently Asked Questions
01What is a Phishing Exercise?
A Phishing Exercise simulates phishing attacks to evaluate and improve an organization’s ability to detect and respond to phishing attempts. Mock phishing emails are sent to employees to see if they recognize and report them, identifying vulnerabilities in security awareness and email filtering systems.
02Why are Phishing Exercises Important?
These exercises help assess and enhance security awareness and training programs. By simulating real phishing attacks, organizations can identify weaknesses in employees’ ability to recognize and respond to phishing attempts, preventing potential data breaches and reducing the risk of malicious phishing campaigns.
03How Frequently Should Phishing Exercises Be Conducted?
Phishing Exercises should be conducted regularly, typically on a quarterly or bi-annual basis. Regular exercises ensure that employees remain vigilant and up-to-date with the latest phishing tactics.
04How Are CyberNX’s Phishing Simulations Different?
CyberNX’s Phishing Simulations stand out due to their realistic and customized approach. These simulations are tailored to mimic current phishing tactics based on the organization’s specific threat landscape. CyberNX uses advanced techniques to craft convincing phishing scenarios, providing detailed analysis and actionable insights to improve the organization’s security posture and employee awareness.
