Make best use of Your Elastic Investments with
Elastic Stack (ELK) Consulting Services
Leverage our expertise as an Elastic Empanelled Consulting Delivery Partner offering Elastic consulting services in Security, SIEM, Search, Observability and more.
Talk to our Experts Today
INTRODUCTION
CyberNX - Your Reliable Elastic Stack Services Partner
Our Elastic Stack consulting services empower organizations to maximize their Elastic Stack (ELK) investments. We skillfully integrate and manage solutions in complex environments tailored to your needs. Our experienced team ensures quick implementation following best practices, optimizing the capabilities of the Elastic Stack to help you achieve a better return on investment.

Our Elastic Stack Consulting helps you with:
Strategically deploy Elastic Security for comprehensive security monitoring, ransomware protection, malware protection, and other critical capabilities.
Design and implement Elastic SIEM according to best practices on Elastic Cloud, on-premises, or public cloud to meet your business requirements.
Powerful search capabilities deliver fast, relevant & scalable search experiences across websites, apps, documents or enterprise data platforms.
Implement Elastic Observability to monitor infrastructure, application, and end-user performance, improving overall performance.
Design and implement Elastic components on Elastic Cloud, ensuring adherence to best practices and scalability requirements.
Helps centralize, parse and visualize logs from multiple sources, enabling real-time insights, faster troubleshooting & improved transparency.
Enables real time tracking of app performance, helping to detect bottlenecks, trace errors & optimize user experience across environments.
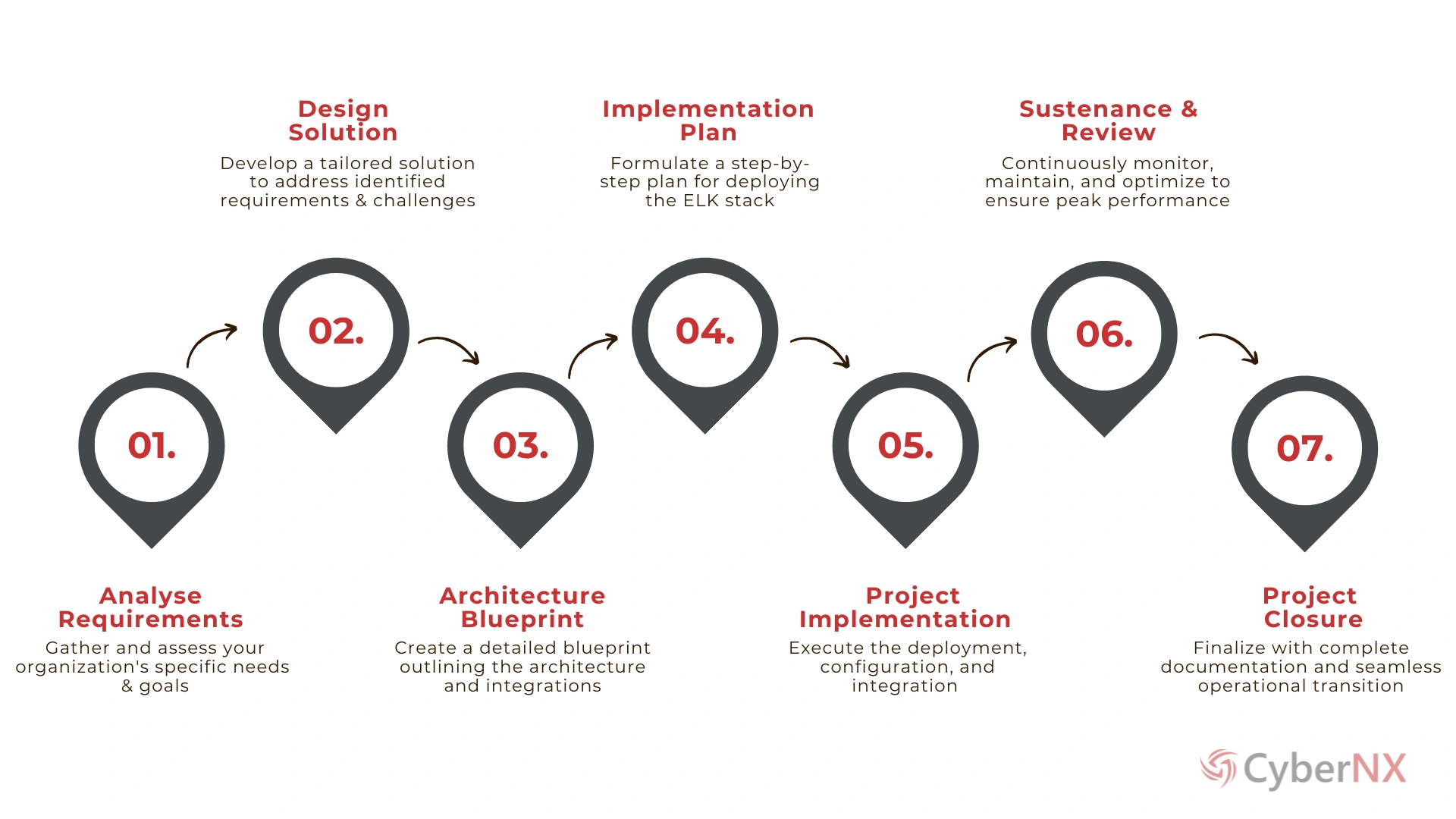
PROCESS
How It Works?
Looking for Comprehensive Elastic Stack (ELK) Consulting Services?
APPROACH
Why Choose CyberNX for Elastic Stack (ELK) Consulting?
CyberNX stands at the forefront of Elastic Stack services, empowering organizations to optimize their digital environments with precision and expertise. We ensure your Elastic Stack implementation is robust, efficient, and aligned with your business objectives.
Initial Consultation
Environment Assessment
Thorough assessments of digital environments to identify opportunities for Elastic Stack services and their implementation.
Elastic Deployment
Deploy Elastic Stack components – Elastic SIEM, Security, Search & Observability – to meet client needs.
Performance Optimization
Continuous Monitoring
Comprehensive Documentation
Customer first Approach is our guiding principle.
BENEFITS
Elastic Stack (ELK) Services Under One Roof
Tailored Solutions
We start with a consultation to understand your business and challenges, delivering customized Elastic Stack solutions.
Comprehensive Assessment
We thoroughly assess your digital environment, identifying opportunities and risks for optimal Elastic Stack implementation.
Strategic Deployment
We deploy Elastic Stack components like SIEM, Security, Search, and Observability, customized to fit your needs.
Performance Optimization
We fine-tune configurations to optimize performance, scalability, and cost-effectiveness, maximizing your ROI.
Proactive Monitoring
We continuously monitor system health, performance, and security events, enabling proactive threat detection and mitigation.
Knowledge Transfer
We document the implementation process and best practices, ensuring transparency and empowering informed decision-making.
Ongoing Support
We provide continuous support and maintenance, addressing evolving requirements to keep your environment optimized and secure.
For Customized Plans tailored to Your Needs,
Get in Touch Today!
FAQ
Frequently Asked Questions
RESOURCES

