Information Systems Management Consulting Services
Request a Free Consultation
INTRODUCTION
CyberNX - Your Trusted ISO 27001 Consulting Partner

We address your key challenges:
How It Works?
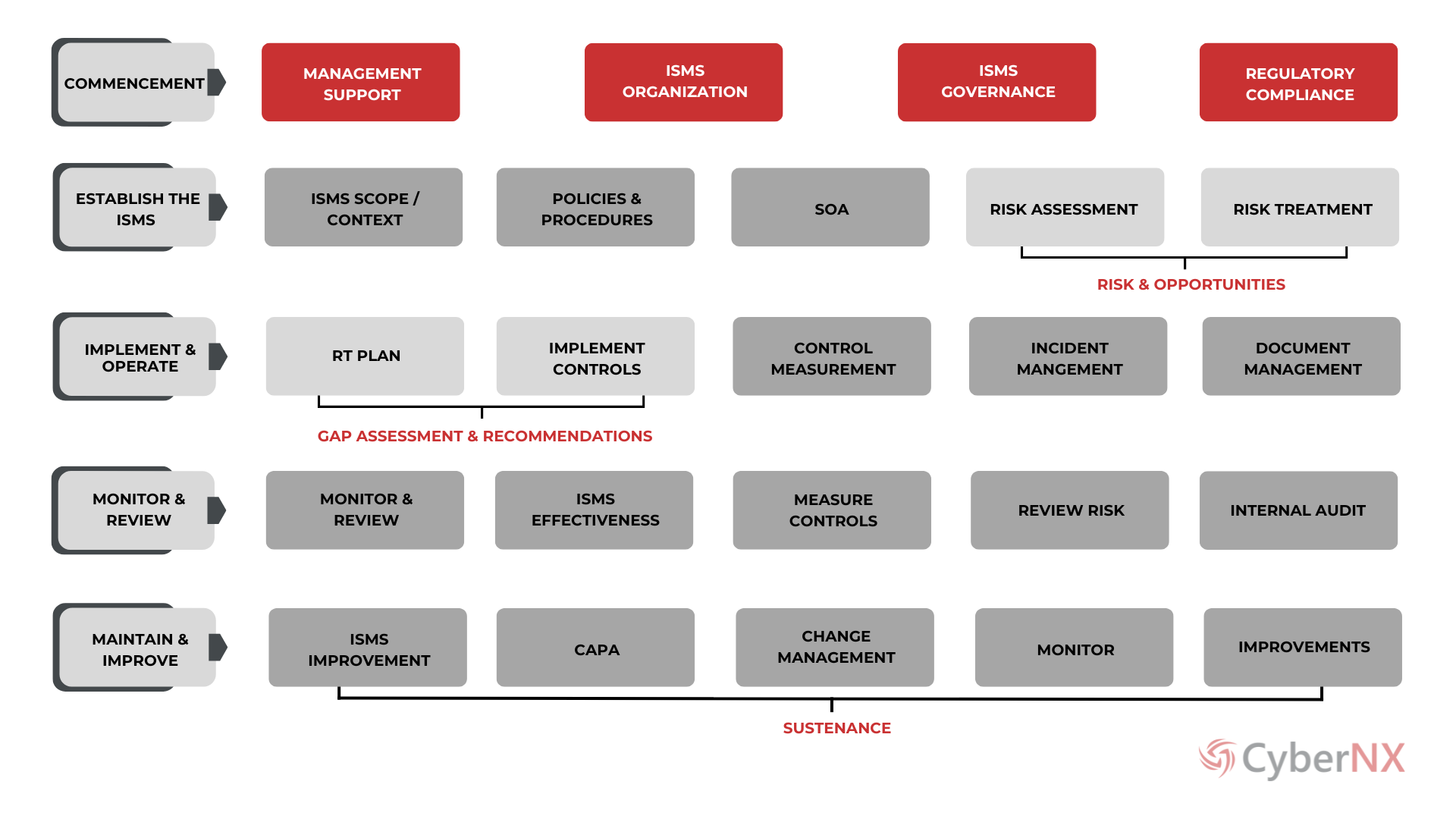
APPROACH
Why Choose us for Security Training?
Expert Guidance
Regulatory Compliance
Tools & Automation
Training & Awareness
Audit & Certification
Monitoring & Support
Looking for ISO 27001 Standard Implementation or Sustenance Services?
BENEFITS
Implementation and Sustenance of ISO 27001
Expert Leadership
Gain from seasoned security professionals who guide your ISO 27001 implementation and maintenance, ensuring a strategic approach tailored to your needs.
Business Alignment
Develop an ISO 27001 Compliance Framework that aligns with your business objectives, ensuring security measures support your overall strategy.
Integrated Security Strategy
Align ISO 27001 compliance with your overall security strategy, including policy development, tool recommendations, and budgeting, to enhance your security posture.
Risk Management
Ensure compliance with relevant regulations and industry standards, reducing legal risks and enhancing credibility.
Regulatory Compliance
Ensure compliance with relevant regulations and industry standards, reducing legal risks and enhancing credibility.
Enhanced Incident Response
Develop robust incident response plans aligned with ISO 27001 standards for effective breach response.
Stakeholder Confidence
Enhance stakeholder confidence by demonstrating a strong commitment to information security through ISO 27001 compliance.
Customer first Approach is our guiding principle.
For Customized Plans tailored to Your Needs,
Get in Touch Today!
RESOURCES
Cyber Security Knowledge Hub
FAQ
Frequently Asked Questions
ISO 27001 is an internationally recognized standard for information security management systems. This standard outlines requirements for establishing, implementing, maintaining, and continually improving an information security management system to ensure robust compliance and risk management.
CyberNX’s ISO 27001 Implementation and Sustenance Services help organizations implement compliance strategies tailored to their specific needs. Through thorough assessments, we identify compliance gaps and implement proactive measures to ensure adherence during audits.
Yes, our ISO 27001 Compliance Services employ a range of tools and automation frameworks to enhance compliance governance implementation. These tools streamline processes, improve efficiency, and expedite the implementation and management of compliance frameworks.
CyberNX stands out in ISO 27001 compliance services by leveraging experienced leadership, a trained team, a robust technology framework, and advanced automation tools. In addition to compliance specialists, CyberNX employs a dedicated team of professionals to execute various activities such as implementation and reviews, ensuring comprehensive and effective ISO 27001 Standard Implementation.


