CERT-IN Empanelled VAPT Services
Talk to our Experts Today
INTRODUCTION
Hacker-Style VAPT Services from CyberNX

Our Security Testing services:
How It Works?
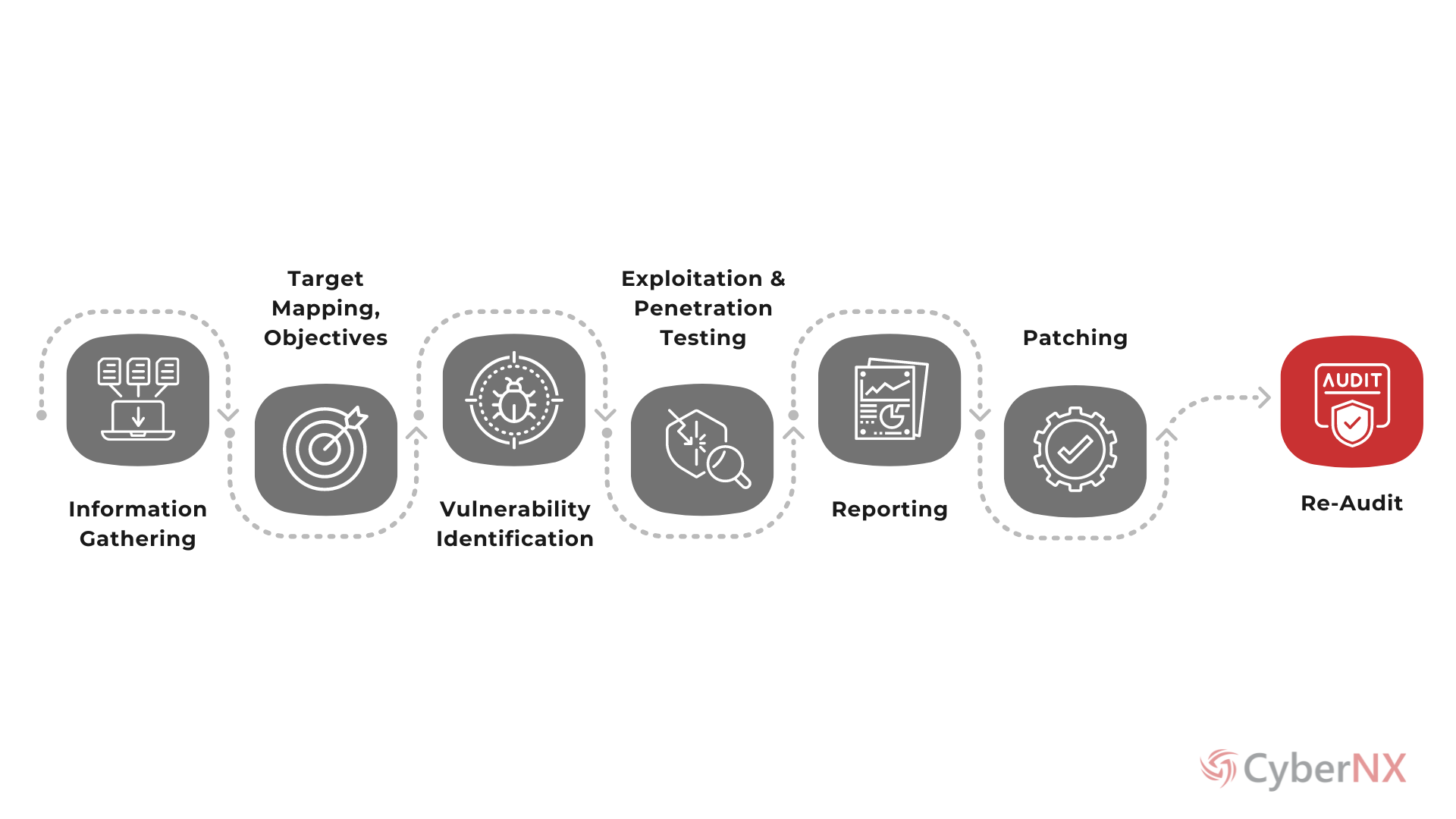
APPROACH
What Does CyberNX Do Differently?
Cutting-Edge Tools
We use the newest VAPT (Vulnerability Assessment & Penetration Testing) tools and technologies for testing.
Risk Mitigation
Highly Skilled Team
Regulatory Compliance
Looking for VAPT Services? Connect with our Team of Expert Penetration Testers!
BENEFITS
Deep Visibility into your Security Posture with VAPT
Identify Vulnerabilities
Find security holes before bad people take advantage of them. This way, you can be proactive about finding and fixing problems.
Compliance and Regulation
Follow strict rules set by regulators by using regular VAPT services to keep private data safe and meet compliance standards.
Prevent Financial Loss
Lower the chance of expensive cyberattacks and data breaches, so you don't lose as much money on fines, court fees, and brand damage.
Improve your Security Posture
Find out how well the current security measures are working and make the general security stronger.
Attack Simulation in the Real World
You can find out how secure your digital assets really are by simulating real-life attacks.
Customer first Approach is our guiding principle.
For Customized Plans tailored to Your Needs,
Get in Touch Today!
RESOURCES
Cyber Security Knowledge Hub
FAQ
Frequently Asked Questions
Vulnerability Assessment and Penetration Testing (VAPT) is a comprehensive evaluation of your digital assets’ security, identifying vulnerabilities and weaknesses to ensure robust protection against cyber threats.
VAPT is crucial for proactively assessing the security of your digital assets. It helps minimize the risk of data breaches and reputational damage by addressing vulnerabilities promptly.
Yes, CyberNX is a CERT-IN Empanelled VAPT Vendor, adhering to all the requirements and best practices for testing and reporting as mandated by CERT-IN.
Our VAPT Services include Application, API, Mobile, Infrastructure, Cloud, and IoT testing.
