Elastic Stack (ELK) Consulting Services
Request a Free Consultation
INTRODUCTION
CyberNX - Your Elastic Stack (ELK) Consulting Partner

Our Elastic Consulting helps you with:
How It Works?
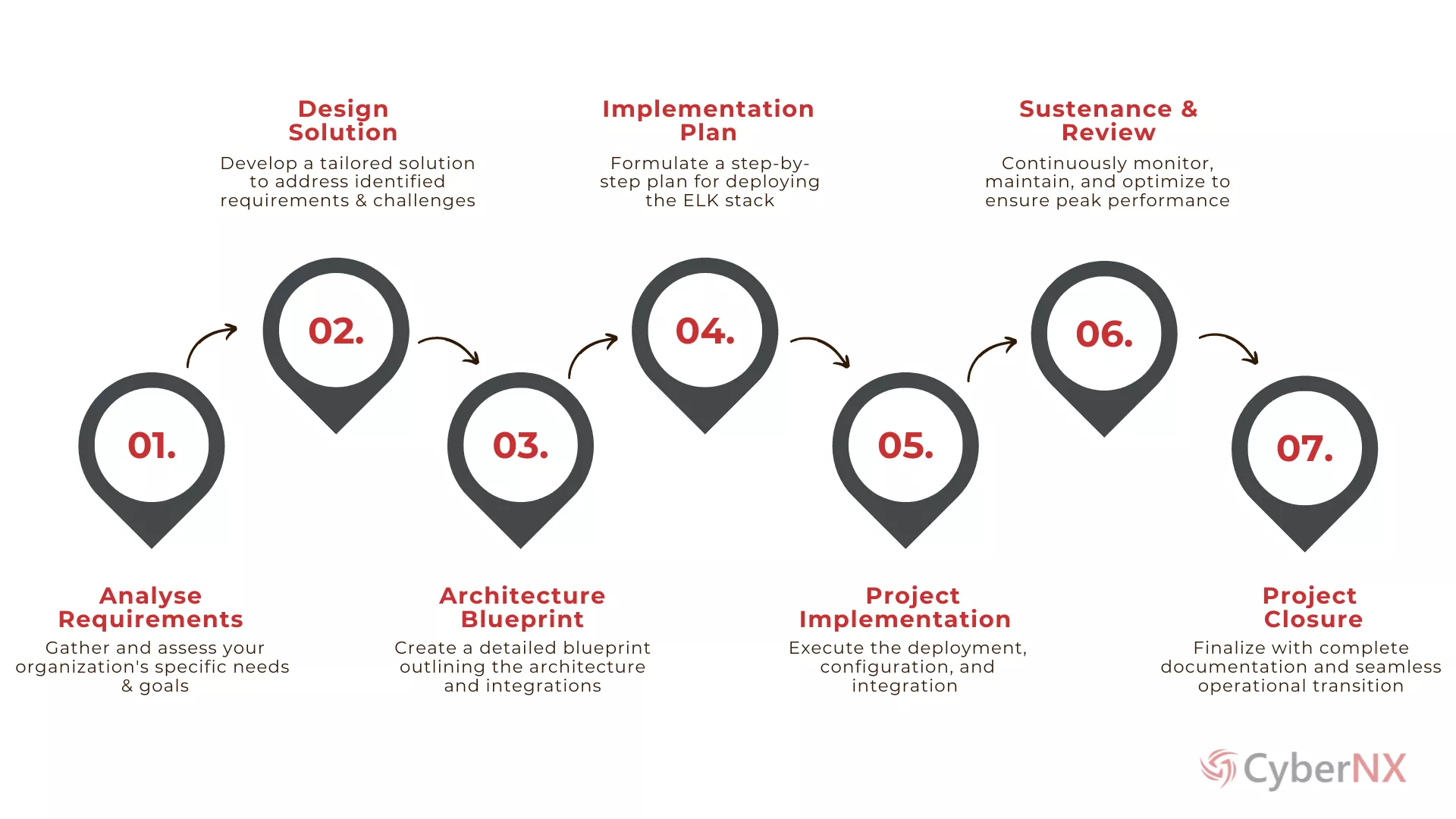
APPROACH
Why Choose CyberNX for Elastic Stack (ELK) Consulting?
01
Initial Consultation
02
Environment Assessment
03
Elastic Stack Deployment
04
Performance Optimization
05
Continuous Monitoring
06
Comprehensive Documentation
Looking for Comprehensive Elastic Stack (ELK) Consulting Services?
BENEFITS
Elastic Stack (ELK) Services Under One Roof
Tailored Solutions
We start with a consultation to understand your business and challenges, delivering customized Elastic Stack solutions.
Comprehensive Assessment
We thoroughly assess your digital environment, identifying opportunities and risks for optimal Elastic Stack implementation.
Strategic Deployment
We deploy Elastic Stack components like SIEM, Security, Search, and Observability, customized to fit your needs.
Performance Optimization
We fine-tune configurations to optimize performance, scalability, and cost-effectiveness, maximizing your ROI.
Proactive Monitoring
We continuously monitor system health, performance, and security events, enabling proactive threat detection and mitigation.
Knowledge Transfer
We document the implementation process and best practices, ensuring transparency and empowering informed decision-making.
Ongoing Support
We provide continuous support and maintenance, addressing evolving requirements to keep your environment optimized and secure.
Customer first Approach is our guiding principle.
For Customized Plans tailored to Your Needs,
Get in Touch Today!
RESOURCES
Cyber Security Knowledge Hub
FAQ
