Improve your Cyber Defense Capabilities with
Brand Risk Monitoring and Dark Web Monitoring Services
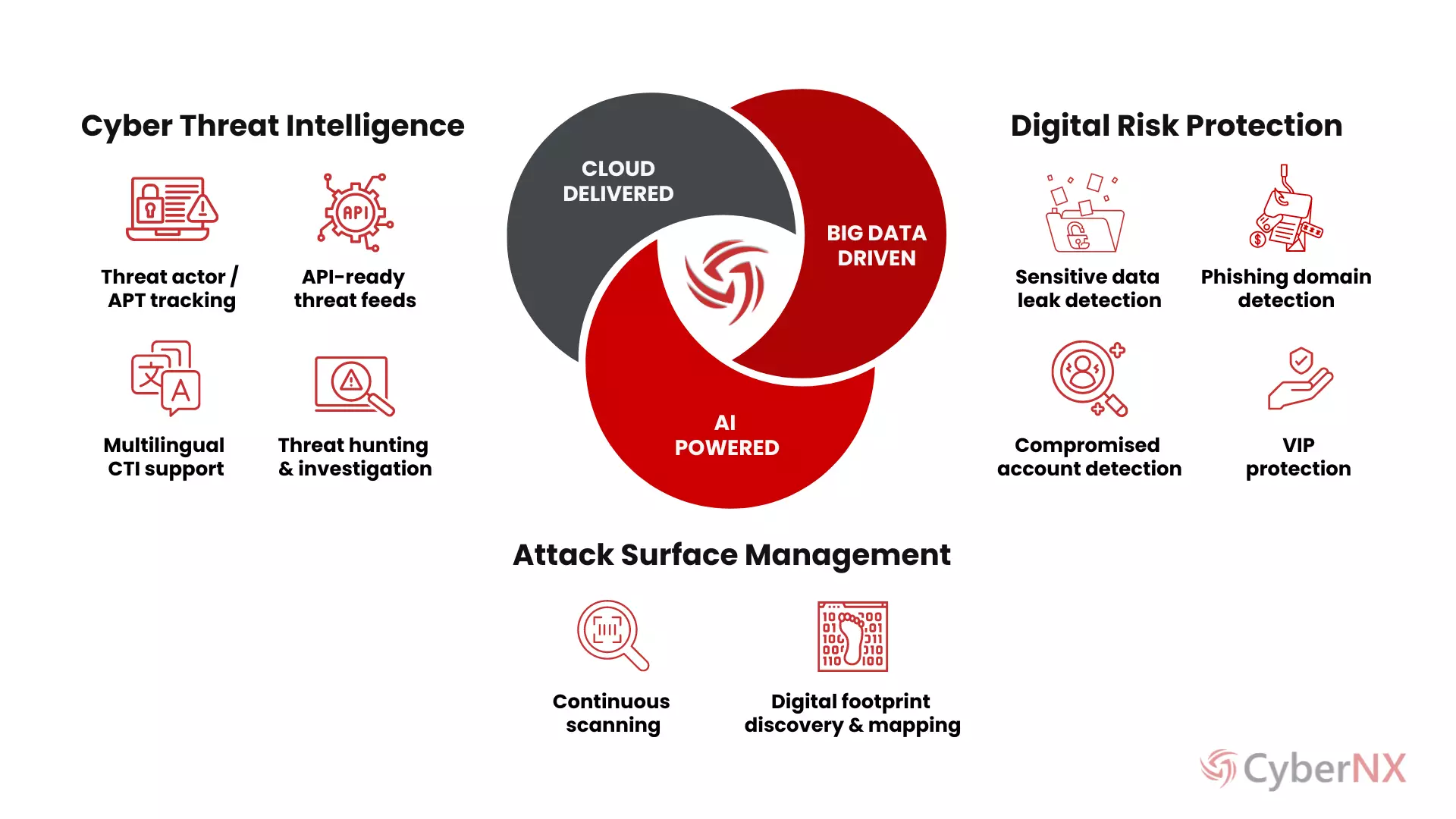
Identify breaches, stolen credentials, infected devices, and third-party data exposures with CyberNX.





















INTRODUCTION
Detect Brand Risks and Data Leaks before they happen
The number of cyber dangers is growing, which puts operations at serious risk as more businesses adopt digital technologies. When companies combine our Brand Risk Monitoring (BRM) and Dark Web Monitoring (DWM) services, they can improve their cybersecurity and be ready for new cyber risks.
We address your key challenges:
PROCESS
How It Works?
Protect your brand with our advanced BRM and DWM solutions!
APPROACH
Why Should You Use CyberNX for Brand Risk Monitoring and Dark Web Monitoring?
Advanced Technology
Real-Time Alerts
Global Coverage
Our thorough tracking covers large areas of the world and keeps an eye out for threats.
Expert Analysis
Our skilled experts give you insightful reports and information that will help you improve your cybersecurity.
Proactive Approach
Compliance Support
Customer first Approach is our guiding principle.
BENEFITS
Protecting the Brand Integity with Brand Risk Monitoring (BRM) and Dark Web Monitoring (DWM)
Expertise That Matters
Our team is made up of experienced professionals who know how to handle cyber threats, find them, and respond to incidents.
Advanced Technology
We use cutting edge software, global threat data, machine learning, and generative AI to give you the best view of possible threats.
Quick Action
We act right away on alerts, reducing the effect of possible problems and quickly dealing with security incidents to keep operations running smoothly.
Cost-Effectiveness
Our services are highly economical, so you can quickly set up brand risk tracking and dark web monitoring at a competitive cost.
Better Visibility
We give you a full picture of your security, including any vulnerabilities, dark web behaviors, and the risks that come with them.
PLANS
Choose a Plan for BRM & DWM Services
Features |
Silver For MSMEsSelect Plan |
Gold For Mid-size EnterprisesSelect Plan |
Platinum For Large EnterprisesSelect Plan |
Dark web Monitoring (DWM) |
|||
Attack Surface Monitoring (ASM) |
|
|
|
Brand Reputation Monitoring (BRM) |
|
|
|
Online Access |
|
|
|
Monitoring & Dashboards |
Self-Monitoring > |
8X6 Monitoring |
24X7 Monitoring |
Custom Dashboards |
|
|
|
Commercial Threat Intelligence |
|
|
|
Automated Reports |
Automated Monthly Reports |
Automated Weekly & Monthly Reports |
Automated Daily, Weekly and Monthly Reports |
Governance |
Quarterly Governance Calls |
Monthly Governance Calls |
Weekly Governance Calls |
Defend your brand's identity using our
Brand Risk Monitoring & Elevate Your Privacy with Dark Web Monitoring!
FAQ
Frequently Asked Questions
RESOURCES

