4 Best Practices for Vulnerability Assessment and Penetration Testing (VAPT)

2 Minutes 8 Seconds | 4476views
Listen This Article Now!
Cyber criminals took advantage of the pandemic's unique and unprecedented circumstances to wreak havoc on the internet, exposing vast amounts of personal data, launching ransomware attacks, and developing increasingly nefarious malware.
So, how do companies prioritise cybersecurity today? - By implementing robust Vulnerability Assessment and Penetration Testing (VAPT) procedures.
Defining the VAPT's Scope
Depending on the needs of the business and any additional industry regulations, the scope of VAPT can vary greatly. To put it in other words, determining VAPT scope isn't a one-size-fits-all situation. When selecting a third-party company to conduct the VAPT, it's critical to select one that knows the industry and takes the time to learn about the client's operations.
Not only is it easier to spot and mitigate critical vulnerabilities across software and platforms with VAPT, but it also allows businesses to find misconfigurations and loopholes in different applications. Companies risk missing critical vulnerabilities that attackers can exploit in the future if the scope of VAPT is too narrow.
Testing and Vulnerability Reporting
A detailed VAPT should be performed on a regular basis to ensure that security measures are robust and adequate, and that they scale with the business. Regular testing and vulnerability reporting have distinct advantages:
-
It demonstrates to clients and companies that the company is trustworthy and takes security seriously, allowing for faster business growth.
-
It demonstrates to clients and companies that the company is reliable and takes security seriously.
VAPT Technical Report Writing Best Practices
The VAPT report is a crucial component of the entire procedure. Testers and engineers must follow best practises for technical report writing to properly convey the VAPT results.
A table of contents and an introduction should be included in the VAPT report. VAPT scope, project details, a timeline of tests, methodology, summary, results, and, of course, conclusion are all important details to include.
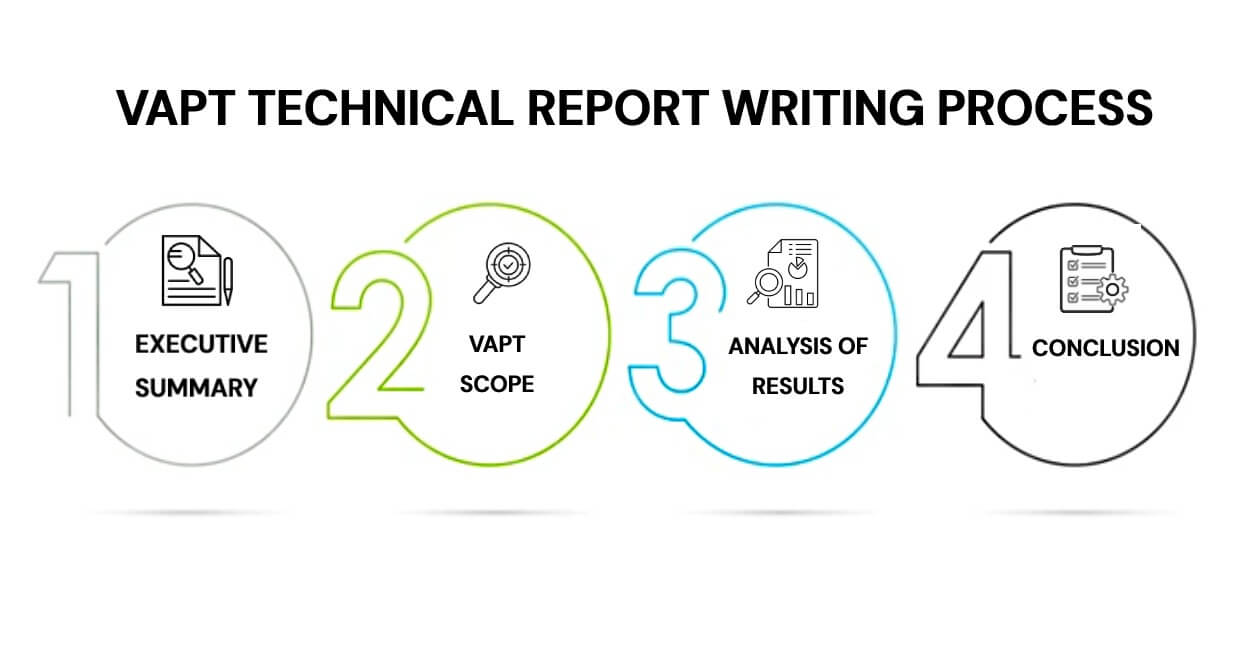
Executive Summary - ?With decision-makers in mind, this section lightens technical information and serves as a brief test overview. It includes the business case, impact, and conclusions, as well as any recommendations and graphics that may be useful in bringing the information to life.
VAPT Scope - The Vulnerability assessment includes which applications, systems, and platforms. It should also include information such as IP addresses and the type of attack (for example, social engineering, wireless network attack, Trojan, etc.). Any limitations to attacks should be mentioned here as well. Finally, the methodology must be stated clearly (white, black, gray box).
Analysis of Results - A comprehensive evaluation of all identified vulnerabilities, their severity, and any recommended next steps.
Conclusion - This section serves as a technical wrap-up for the entire exercise, targeting a technical audience and highlighting all critical security flaws.
VAPT best practises and guidelines will evolve as cybercriminals refine their tools and evolve their tactics. As a result, we must always be on the lookout for security threats and use best practises to safeguard our systems. Contact us for any VAPT Requirement
Table Of Content
Cyber criminals took advantage of the pandemic's unique and unprecedented circumstances to wreak havoc on the internet, exposing vast amounts of personal data, launching ransomware attacks, and developing increasingly nefarious malware.
So, how do companies prioritise cybersecurity today? - By implementing robust Vulnerability Assessment and Penetration Testing (VAPT) procedures.
Defining the VAPT's Scope
Depending on the needs of the business and any additional industry regulations, the scope of VAPT can vary greatly. To put it in other words, determining VAPT scope isn't a one-size-fits-all situation. When selecting a third-party company to conduct the VAPT, it's critical to select one that knows the industry and takes the time to learn about the client's operations.
Not only is it easier to spot and mitigate critical vulnerabilities across software and platforms with VAPT, but it also allows businesses to find misconfigurations and loopholes in different applications. Companies risk missing critical vulnerabilities that attackers can exploit in the future if the scope of VAPT is too narrow.
Testing and Vulnerability Reporting
A detailed VAPT should be performed on a regular basis to ensure that security measures are robust and adequate, and that they scale with the business. Regular testing and vulnerability reporting have distinct advantages:
-
It demonstrates to clients and companies that the company is trustworthy and takes security seriously, allowing for faster business growth.
-
It demonstrates to clients and companies that the company is reliable and takes security seriously.
VAPT Technical Report Writing Best Practices
The VAPT report is a crucial component of the entire procedure. Testers and engineers must follow best practises for technical report writing to properly convey the VAPT results.
A table of contents and an introduction should be included in the VAPT report. VAPT scope, project details, a timeline of tests, methodology, summary, results, and, of course, conclusion are all important details to include.

Executive Summary - ?With decision-makers in mind, this section lightens technical information and serves as a brief test overview. It includes the business case, impact, and conclusions, as well as any recommendations and graphics that may be useful in bringing the information to life.
VAPT Scope - The Vulnerability assessment includes which applications, systems, and platforms. It should also include information such as IP addresses and the type of attack (for example, social engineering, wireless network attack, Trojan, etc.). Any limitations to attacks should be mentioned here as well. Finally, the methodology must be stated clearly (white, black, gray box).
Analysis of Results - A comprehensive evaluation of all identified vulnerabilities, their severity, and any recommended next steps.
Conclusion - This section serves as a technical wrap-up for the entire exercise, targeting a technical audience and highlighting all critical security flaws.
VAPT best practises and guidelines will evolve as cybercriminals refine their tools and evolve their tactics. As a result, we must always be on the lookout for security threats and use best practises to safeguard our systems. Contact us for any VAPT Requirement
Share this on: