Every organisation depends on web applications. They support customers, teams and partners and they also handle sensitive data every day. In recent times, businesses are face constant security threats, snowballing from web apps. This is because attackers look for small cracks and a simple thing like a coding mistake is enough for a major breach.
This is where web app VAPT plays a vital role. It helps teams uncover weaknesses before attackers find them and gives clarity on real risks. Plus, it allows leaders to plan improvements with confidence. We have seen the impact of VAPT across industries. When teams understand how attackers think, they strengthen defences faster.
What is web application VAPT?
Business leaders often know about VAPT, and how it is used to find and fix system vulnerabilities before they go out of hand. But many get confused when it comes to the subsets of VAPT like web application VAPT.
Basically, this VAPT engagement also combines two approaches. The first is vulnerability assessment, which checks for known issues. The second is penetration testing, which attempts to exploit those issues to understand real impact.
Together, they give a sharper view of application security. They help teams prioritise what matters and avoid noise.
The only difference really is that it is fixated on web applications. These tests work across all types of web apps, from customer portals to internal tools and complex cloud-native systems.
Why VAPT is your web application’s lifeline
Modern applications are dynamic. New features roll out often where integrations change and attack surfaces grow. This makes it hard for teams to keep every corner secure.
Web app VAPT supports that journey. It highlights blind spots early, gives developers practical guidance and strengthens the protection of data and user trust.
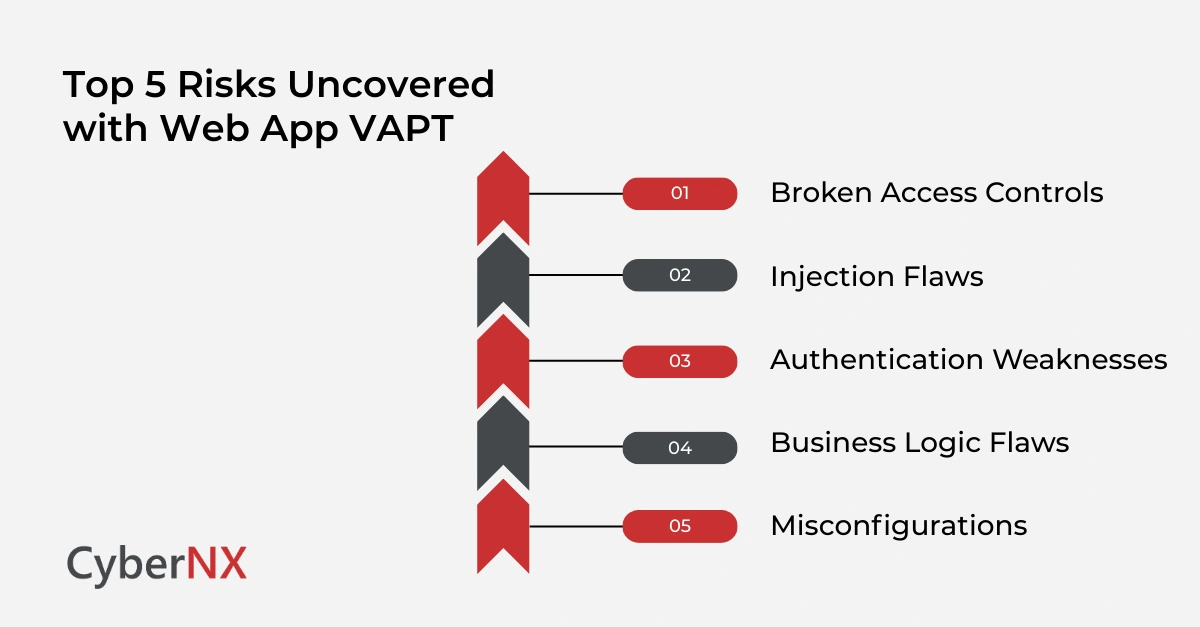
Key risks uncovered through web app VAPT
Before testing begins, teams usually expect coding flaws. But our work shows the risk surface is much wider. VAPT often reveals gaps created through design, configuration and access controls.
Here are some common areas exposed during assessments.
1. Broken access controls
Attackers exploit weak role checks to access restricted areas. This often leads to data exposure or full account takeover.
2. Injection flaws
SQL injection, command injection and template injection still appear in real environments. Even small mistakes allow attackers to manipulate backend systems.
3. Authentication weaknesses
Weak login flows, missing rate limits and token mismanagement create dangerous entry points. These issues often remain unnoticed until a VAPT exercise spots them.
4. Business logic flaws
Attackers target logic gaps rather than technical issues. They exploit predictable workflows or bypass important steps.
5. Misconfigurations
Default settings, exposed admin panels or improper cloud permissions show up frequently. They are easy to miss. But they are easy to fix once identified.
OWASP research shows broken access control remains the most exploited web application risk worldwide. This shows that even mature teams face logic and permission issues. Continuous testing helps catch these gaps early.
Deconstructing the web app VAPT process
A structured process keeps the assessment predictable. It ensures the test covers both common and complex attack paths.
- Scoping: Teams define features, modules and integrations that fall within the assessment. Clear scope avoids blind spots.
- Reconnaissance: Testers gather information about the app, server and API behaviour. This helps craft realistic attacks.
- Vulnerability scanning: Automated tools highlight known issues across the application.
- Manual penetration testing: Experts dig deeper. They chain vulnerabilities. They test logic. They attempt to replicate real attacker behaviour.
- Reporting and remediation: The final report highlights impact, explains risks and provides practical fixes. Our experience shows that clear remediation steps significantly improve developer response time.
- Retesting: Teams validate that fixes work. This step ensures long-term improvement rather than temporary patches.
Unlocking business value of web app VAPT
Web app VAPT supports more than technical resilience. It helps build trust, streamline audits and strengthen security culture. Here are some core advantages.
- Early visibility: Teams see issues before they reach production or affect end users.
- Stronger customer trust: Secure applications protect brand reputation and reduce breach risk.
- Better compliance: Standards like PCI DSS, ISO 27001 and SOC 2 expect regular security testing for web applications.
- Developer awareness: Actionable reports help developers understand the weaknesses behind their code. This leads to safer future releases.
- Resilience against real attacks: Web app VAPT provides insight into how attackers chain issues together. Teams learn to think ahead, not just patch quickly.
A Forrester report found that organisations using regular web app VAPT reduce breach likelihood by up to 30 percent. This shows that consistency matters more than frequency. Small, regular tests drive long-term resilience.
How often should you run VAPT?
Most organisations test applications annually. Apps with frequent updates need quarterly or release-based testing. High-risk applications benefit from continuous VAPT cycles integrated into DevSecOps processes. Frequency should match business impact and change velocity.
Vetting the right partner for web application security
A strong partner improves both accuracy and value. Teams should look for CERT-In empanelled VAPT auditors in India. The government recognized firms combine automated tools with expert manual testing and follow the best practices. Clear reporting, realistic attack simulation and collaborative remediation support make a major difference.
Conclusion
Web app VAPT gives teams a clear view of how secure their applications truly are. It uncovers issues early. It helps avoid costly breaches. And it supports confident, secure growth.
If you want to secure your applications with a focused and practical VAPT approach, we can help. We are a CERT-In empanelled firm, and we have the experience of working closely with teams to create predictable, outcome-focused VAPT exercises. The goal of providing VAPT services is simple: to help you fix what matters and strengthen your applications safely.
Web App VAPT FAQs
How long does a web app VAPT assessment take?
Most tests take a few days to a few weeks, depending on complexity, integrations and authentication flows. Smaller apps complete faster. Larger systems require more manual testing.
Does web app VAPT include API testing?
Yes. APIs often form the core of modern applications, so they are included. Testing covers authentication, authorisation, input validation and business logic.
Can VAPT be done on staging environments?
Yes. Many teams prefer staging for safety. But production testing gives the most accurate results. The choice depends on risk and business needs.
Is web app VAPT suitable for cloud-hosted applications?
Absolutely. Cloud-native apps, serverless components and managed services also face risks. VAPT checks configurations, permissions and identity flows.