We are just halfway through 2025, and more than 23,000 software vulnerabilities have been disclosed already. At this pace, experts opine that the final tally could well exceed 33,000 Common Vulnerabilities and Exposures (CVEs) by the end of the year. Now that is five new vulnerabilities every minute, every day and an increase from what was found last year.
A single unpatched server, a misconfigured cloud bucket or a forgotten API endpoint. All of these could be the root cause of tomorrow’s breach story. Cyberattacks, more often, start with overlooked flaws or loopholes in the system. Vulnerability testing is the disciplined process of finding those cracks before hackers does.
What is Vulnerability Testing?
Vulnerability testing or assessment is aimed at finding vulnerabilities in your IT system components. This can be a mobile app, a cloud system, APIs or even IoT devices. The vulnerability testing experts use tools to scan systems, services and software to find weaknesses. Some of the vulnerabilities include missing patches, exposed endpoints or risky defaults. The focus is to produce a prioritized list of issues closely related to business priorities. This helps decision-makers fix what matters most.
This practice sits between continuous monitoring and a full red-team engagement: faster than an adversary simulation but deeper than routine observability.
This is just the tip of the iceberg. Find deeper insights about this cybersecurity service with our blog Vulnerability Assessment Guide. Read now!
Benefits of Vulnerability Testing
For leaders, the practical wins are clear:
1. Risk Prioritization with Business Context
Basically, cybersecurity vulnerability testing finds and generate a list of flaws present in your systems. But that’s not it. The vulnerability assessment process ranks the vulnerabilities by severity and how each of them can impact your business. This prioritization gives executives as well as technical leaders clarity. The issues that could disrupt revenue streams, regulatory obligations and customer trust are handled first.
2. Cost Avoidance and Incident Reduction
If you catch a high-risk bug early, cost incurred is less. However, cleaning up after a breach is costly. This difference is massive and must be discussed in the boardrooms. Addressing exposures proactively has plenty of benefits for your organizations. Like saving on breach response, regulatory penalties, legal fees and reputational damage.
3. Compliance and Regulatory Confidence
There are standards like PCI DSS, HIPAA and GDPR. In India, RBI, SEBI and CERT-In also mandates vulnerability compliance. Therefore, public and private organizations, especially regulated entities are expected to follow ongoing vulnerability management. Regular vulnerability testing ensures your company can demonstrate real, evidence-based diligence when auditors or regulators ask for proof.
4. Board-Level Reporting and Executive Visibility
In our experience, many vulnerability assessments vendors end up providing only scanned findings to leaders and decision makers. This doesn’t add any value to your organization. The focus should be on digestible insights which are clearly tied to risk and business operations. This paves the way for smarter decisions in boardrooms and strategy meetings.
What else are must-haves in a report? Read our guide on Vulnerability Assessment Report to know.
5. Stronger Customer and Partner Trust
When you run regular testing, you are signalling maturity to clients and partners. Customers also trust that you are constantly addressing weaknesses and resolving them proactively. What it does is to build long-term confidence, making cybersecurity a business differentiator. A strong selling point for your sales team.
When done well, vulnerability testing in cybersecurity becomes a strategic capability: it informs product roadmaps, vendor decisions and insurance conversations.
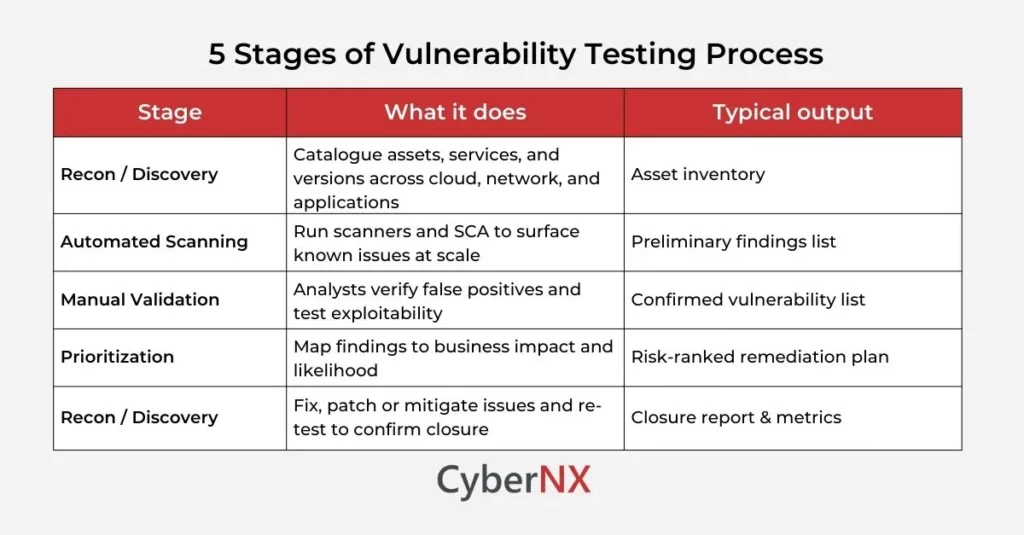
5 Stages of Vulnerability Testing
Vulnerability testing in cybersecurity follows a structured flow, moving from discovery to remediation. Each stage builds on the last, ensuring weaknesses are not just identified but also validated, prioritized and resolved.
Common Vulnerabilities Found in Digital Assets
We have been conducting a lot of vulnerability assessment and penetration testing for companies across industries. Our research shows that even mature environments show familiar patterns and the most common flaws found are:
1. Unpatched Software and Outdated Frameworks
Legacy systems and third-party libraries often harbour known CVEs that attackers can exploit with minimal effort. These unpatched gaps are among the easiest ways for attackers to gain entry.
2. Cloud and Identity Misconfigurations
Modern IT environments include cloud systems, and this trend is only increasing. In such a scenario, a single misconfigured S3 bucket or overly permissive IAM policy can be dangerous. This is because it can expose terabytes of sensitive data. Cloud complexity has directly turned identity and access errors as one of the top recurring vulnerabilities.
3. Weak Authentication Practices
This is a perennial issue in business setting. Credential reuse, poor password hygiene and a lack of multi-factor authentication are easy pickings for threat actors. The weaknesses often serve as the attacker’s first foothold into otherwise well-defended systems. And these can lead to drastic consequences.
4. API and Application Logic Flaws
Business logic vulnerabilities, broken access control, and insecure API endpoints are increasingly targeted. These flaws may not show up in automated scans but can result in data manipulation, privilege abuse, or transaction fraud.
5. Privilege Escalation and Poor Segmentation
Once a cyber attacker gains low-level access to the system, flat network structures or excessive admin rights frees them to escalate privileges. So, what begins as a minor vulnerability escalate into complete environment compromise. This is true if segmentation and least privilege aren’t enforced.
However, many of these are process problems that show up repeatedly and become tractable once surfaced with context.
5 Types of Vulnerability Testing Tools
To cover enterprise risk, you’ll typically combine several tool classes:
- Network scanners: Testers often use these tools to map ports and services and find exploitable exposures at the infrastructure level.
- Web application scanners: This is also used to identify common web flaws like injection, auth bypass and broken access control.
- Software composition analysis (SCA): Detect vulnerable open-source components and licensing risks.
- Infrastructure-as-code (IaC) and container scanners: Catch insecure deployments before they reach production.
- Fuzzers and API testing tools: Stress inputs and edge-cases to reveal logic and parsing defects.
The balanced approach is to mix automated scanning with human expertise. The former finds the obvious whereas the latter is important to validate the consequential.
Conclusion
A resilient organization treats discovery as a routine capability. Structured assessments done regularly and tied to business context turn unknowns into manageable projects. When security teams deliver risk-ranked, actionable findings, boards and executives stop debating hypotheticals and start funding fixes that matter.
If you want to shift from reactive firefighting to proactive risk management, consider building a cadence where scans, manual validation and business prioritization form a single loop. After that loop is dependable, you’ll see fewer surprises and clearer conversations about the outcomes leaders need. Contact us today for vulnerability testing services.
Vulnerability Testing FAQs
How often should an organization scan its estate?
Frequency depends on change velocity: weekly for fast-moving cloud services, monthly for stable networks, and immediate scans after any significant change or release.
Should vulnerability findings be shared with product teams?
Yes. The most effective remediation happens when security and product collaborate – security provides risk context; product provides remediation paths.
Can automation replace human validation?
No. Automation scales discovery, but human validation is essential to reduce false positives and to assess business impact.
How do you measure program success?
Track mean time to remediate high-risk findings, percentage of incidents tied to previously known vulnerabilities, and trend lines showing a shrinking high-risk population over time.