You know that uneasy feeling when you lock your house door but keep glancing back, wondering if you really turned the key? That’s what cybersecurity often feels like for businesses today. You’ve got firewalls. You’ve got antivirus. Maybe you even have a small security team keeping an eye on threats. But deep down, you’re asking: Is my business safe?
That’s where Vulnerability Assessment (VA) steps in. Coming back to the house metaphor, think of VA as the digital equivalent of checking every window, every backdoor, every weak hinge in your house, before a burglar does.
This guide is for you if you’re trying to make sense of all the noise around cyber risks. We’ll walk through what vulnerability assessment really means, why it matters, the process behind it, and how you can use it to sleep a little easier at night.
What is Vulnerability Assessment (and Why Should You Care)?
At its simplest, a vulnerability assessment is like a health check-up for your IT systems. It scans your digital “body” – that includes servers, networks, applications, endpoints—and finds out the weak spots.
The goal isn’t just to find flaws. It’s to understand:
- What could break?
- How bad would it be if it broke?
- How quickly should I fix it?
Here’s the thing: hackers don’t care whether your business is big or small. They’re opportunists. If they see an unlocked door, they’ll walk right in. That’s why knowing your weaknesses before they do is the first real step in defence.
Benefits of Vulnerability Assessment
Let’s talk about the pay-off. Why should you invest the time, money, and effort in vulnerability assessment? Well, for these reasons:
- Reduced risk of breaches – Because most attacks exploit known vulnerabilities.
- Regulatory compliance – Many industries require regular assessments.
- Cost savings – Fixing an exposed system costs far less than recovering from a breach.
- Better IT hygiene – Clean, patched, updated systems run smoother.
- Fewer sleepless nights – Knowing you’ve checked the locks.
At its core, vulnerability assessment is about control. Instead of waiting for the storm, you’re reinforcing the roof before the rain starts.
Common Challenges (And How to Deal with Them)
It’s not all sunshine, though. There are roadblocks with vulnerability assessment testing services. The major ones are discussed:
- Too many false positives – Tools flagging issues that aren’t real
- Overwhelming results – Hundreds of vulnerabilities, no idea where to start
- Lack of in-house expertise – Not every business has a cybersecurity team
- Budget pushback – Leadership often sees security as “extra cost”
Here’s the truth: every business faces these. The trick is persistence. Start small. Use a vulnerability testing service if needed. Show leadership the cost of inaction (a single breach can damage a company’s reputation overnight).
Vulnerability Assessment vs. Penetration Testing
A lot of people mix these up, and honestly, it’s not surprising. They sound similar, but they’re not the same. Here’s how you can define them:
- Vulnerability assessment: Spotting cracks in the wall. Listing them. Prioritizing them.
- Penetration testing: Acting like a cyber attacker and actually trying to break in through those cracks.
Know everything about pentesting with our blog Penetration Testing Guide.
You need both eventually. But if you’re just starting out, a vulnerability assessment is usually the smarter, less intimidating step. It gives you a map before you head into battle.
The Frustration Every Business Feels
With many years of experience in the field, we know how it feels sometimes. You’ve probably felt one (or all) of these:
- We know cyber risks are out there, but we don’t know where to begin.
- We’ve already invested in tools, but we’re not sure if they’re enough.
- Our clients keep asking about security certifications and audits, and we don’t have answers.
- The IT team is overworked. Security feels like another mountain to climb.
Sound familiar? You’re not alone. Vulnerability assessment was designed to tackle exactly these frustrations. It takes the unknowns and puts them on paper in plain language.
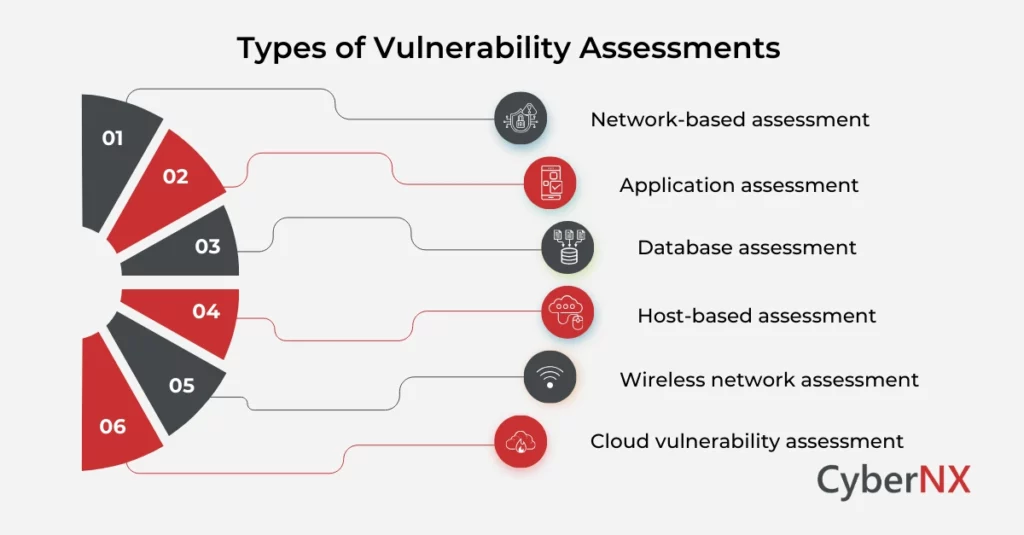
Types of Vulnerability Assessments
Not all assessments are the same. Depending on your business, you might need one or a mix of these:
- Network-based assessment – Looks at routers, switches, firewalls, servers. Basically, the skeleton of your IT.
- Application assessment – Digs into your web apps, mobile apps, or SaaS products. Because attackers love sneaking in through poorly coded apps.
- Database assessment – Checks for misconfigurations, weak passwords, or unpatched systems in the place that stores your crown jewels: data.
- Host-based assessment – Focuses on specific devices like laptops, desktops, and virtual machines.
- Wireless network assessment – Tests your Wi-Fi setup to see if attackers can piggyback in.
- Cloud vulnerability assessment – A newer but crucial one. As businesses move workloads to AWS, Azure, or Google Cloud, the attack surface shifts.
Think of these as different “medical tests.” A blood test won’t catch a lung infection. Likewise, a network scan won’t tell you if your cloud storage bucket is exposed.
How the Vulnerability Assessment Process Actually Works
This is where most guides get boring. But let’s keep it simple. The process usually flows like this:
1. Define the Scope
What do you want tested? Just your web apps? The entire corporate network? Cloud? A clear scope saves time and money.
2. Scan the Environment
Here’s where the tools come in – Nessus, OpenVAS, Qualys, Nexpose. They scan through your systems, looking for weak spots like outdated software, missing patches, or insecure configurations.
3. Analyse the Results
The scan results are messy. Hundreds, sometimes thousands, of “potential issues.” This is where expertise matters – separating the harmless noise from the real threats.
4. Prioritize Vulnerabilities
Not every flaw is a ticking bomb. Some are harmless, some are catastrophic. A good vulnerability assessment ranks them:
- Critical
- High
- Medium
- Low
5. Report and Recommend
Finally, you get a detailed report. But the good ones don’t just dump data. They translate it into a plan: “Here’s what to fix first. Here’s what can wait. Here’s how to do it.”
Read our blog Vulnerability Report. It will help IT security leaders get a clear picture about reports and what to expect from them.
The Role of Vulnerability Testing Services
Let’s be honest. You could try running free tools yourself. But here’s the catch: raw data isn’t wisdom.
This is why many businesses turn to a vulnerability testing service. These providers don’t just scan your environment. They bring expertise, interpret and advise. They keep you from wasting days chasing false alarms. Downloading a scanner tool doesn’t make you secure. A vulnerability testing service helps bridge that gap.
On its own, vulnerability assessment won’t make you bulletproof. But it’s the foundation. Once you know your weaknesses, you can layer on:
- Penetration testing – To simulate real-world attacks.
- Security audits – To measure against compliance standards.
- Continuous monitoring – To stay updated as new threats emerge.
Pen testing is your stress test. Ongoing monitoring is your daily workout. Together, they keep your digital body fit.
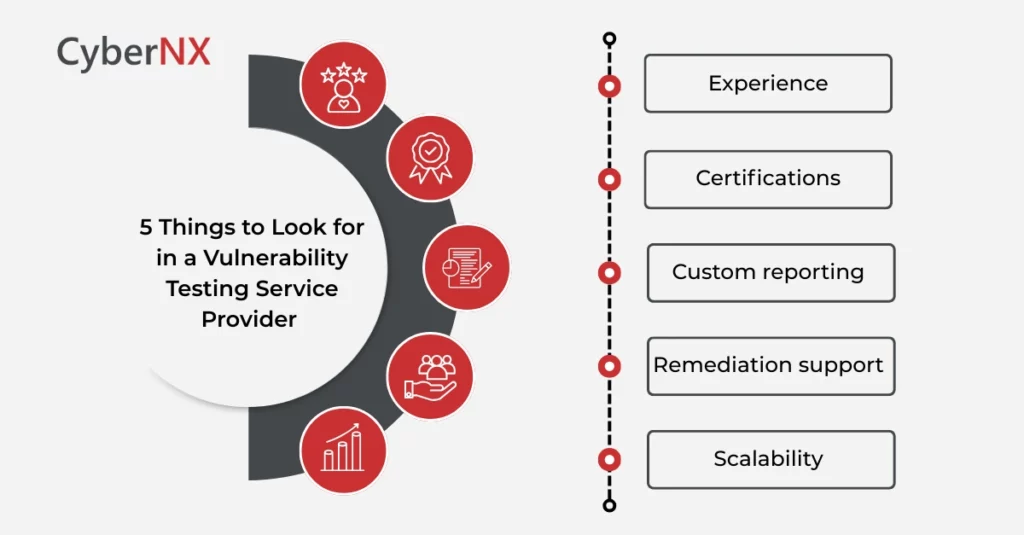
Choosing the Right Vulnerability Testing Service
Okay, let’s get practical. If you’re considering outsourcing, here’s what to look for in a provider:
- Experience – How long have they been in the game?
- Certifications – Are they accredited (like CERT-In in India)
- Custom reporting – Do they explain findings in plain language?
- Remediation support – Do they just list problems, or also guide you on fixing them?
- Scalability – Can they handle your systems as you grow?
Don’t just pick the cheapest. This isn’t buying printer paper. It’s about protecting your business from threats that can cost millions. Getting a grasp of vulnerability assessment best practices will also help you ask the right question to the vendors.
The Human Side of Vulnerability Assessment
Here’s something most blogs won’t tell you: this isn’t just about tech. It’s about people.
Every vulnerability assessment you run is also building a culture of security in your company. It tells your employees, your clients, even your investors: “We care. We take this seriously.”
And that matters. Trust is the currency of business today. Lose it, and you’re done. Strengthen it, and you build loyalty that no competitor can easily steal.
Conclusion
Cybersecurity doesn’t have to be a constant source of anxiety. A vulnerability assessment is one of the most practical, grounded steps you can take. It strips away the guesswork. It gives you clarity. And most importantly – it helps you act before it’s too late.
If you’ve been hesitating, waiting for the “right time,” let this be your nudge. The right time is now. Your business deserves the peace of mind. Your customers deserve the protection.
Connect with us for outcome-driven vulnerability assessment services. Our experts will help you find what’s lurking out there in the dark corners of the internet and protect your business 24X7.
Vulnerability Assessment Guide FAQs
How often should a full vulnerability assessment be performed for a mid-sized SaaS company?
While continuous discovery is ideal, schedule a comprehensive, expert-validated assessment at least quarterly, with automated scans running weekly and critical assets monitored continuously.
Can vulnerability assessment replace penetration testing?
No. Vulnerability assessment and penetration testing are complementary. Assessments discover and prioritize weaknesses; penetration testing simulates attacker behaviour to validate exploitability and business impact.
What is the role of an asset inventory in a successful vulnerability assessment program?
Asset inventory is foundational. You cannot measure or remediate what you cannot track. A maintained inventory is the anchor for prioritization, remediation, and auditability.
How should startups with limited resources approach remediation?
Prioritize risks that threaten customer trust and revenue. Use compensating controls, automation, and phased architectural improvements. Leverage a trusted vulnerability testing service to validate high-impact findings and optimize engineering effort.