Teams often run VAPT without a clear plan. They jump into scanning or testing but miss critical steps that define the quality of the engagement. A strong VAPT checklist brings structure. It helps security leaders prepare, execute and validate assessments with confidence. It also makes life easier during audits and internal reviews, especially when systems evolve quickly.
Many decision makers now use a checklist to align teams, remove guesswork and ensure results translate into meaningful fixes. If your organisation handles sensitive data or operates in regulated environments, the right checklist can simplify the journey and uncover risks that usually escape attention.
What is the VAPT checklist?
A VAPT checklist is a structured list of tasks, controls and preparation steps that guide the entire VAPT process. It ensures no stage is missed, from scoping through testing and remediation. It is not a replacement for testing, but a tool that helps teams run assessments in a predictable and repeatable way.
Before any assessment begins, a checklist helps you answer important questions. What systems are in scope? Who owns them? What risks matter most? What level of testing is acceptable? Without that clarity, VAPT becomes inconsistent and hard to measure.
Taking the guesswork out of security testing
Before diving into the checklist itself, it is important to understand why structured preparation matters. Modern environments shift too quickly. Teams deploy updates at speed, connect new services and adopt cloud platforms without always reviewing security impact. A plan ensures VAPT assessments adapt to this reality.
Organisations also use checklists to improve communication between engineering, product, compliance and security teams. Clear expectations help avoid delays and reduce friction during audits. When regulators ask for proof, a documented checklist offers reliable evidence.
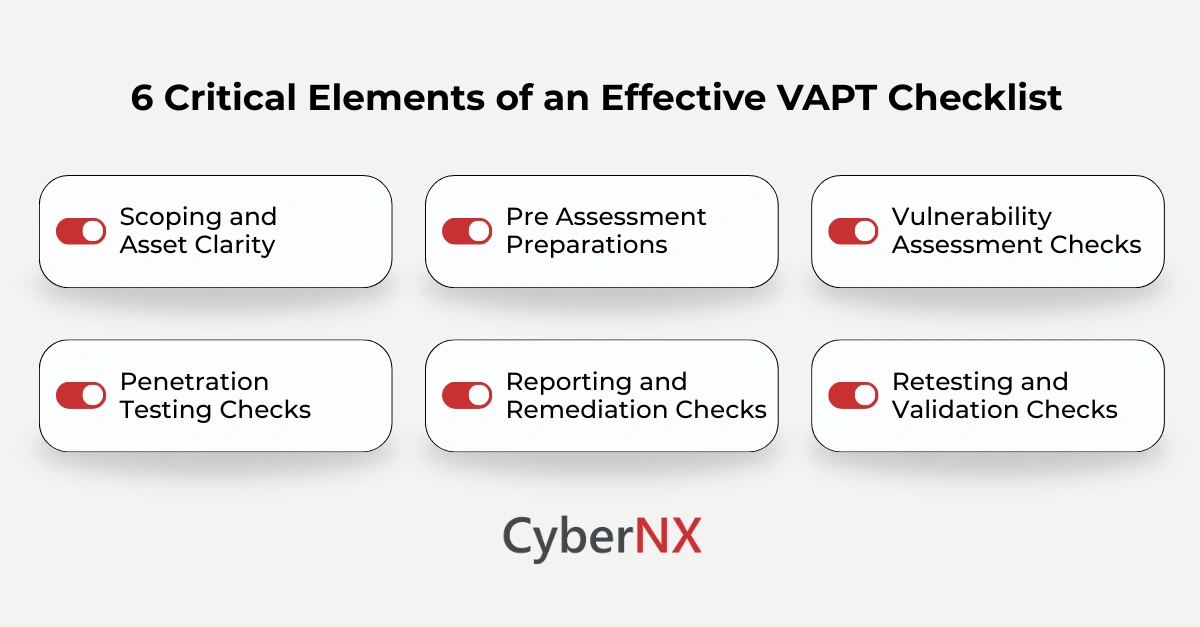
Key elements of an effective VAPT checklist
Every VAPT checklist should cover preparation, testing, validation and documentation. Below is a complete view of what decision makers should include. This structure helps teams run assessments that are consistent, measurable and aligned with risk.
1. Scoping and asset clarity
This section deals with early planning. Without clear scoping, VAPT tends to drift or overlook important systems.
- Identify systems in scope such as web applications, mobile apps, APIs, servers, cloud workloads and network zones.
- Define business criticality for each asset.
- Confirm ownership and access permissions.
- Record dependencies like third party integrations or shared services.
- List compliance requirements that affect testing depth.
A clear scope avoids surprises later and keeps everyone aligned.
2. Pre assessment preparations
Once systems are defined, the team prepares the environment. These steps ensure a smooth and safe test.
- Ensure test environments mimic production where practical.
- Back up critical systems before active testing.
- Confirm testing windows with IT and operations teams.
- Document authentication details and test accounts.
- Share architecture diagrams to support deeper manual testing.
- Approve rules of engagement for safe exploitation.
This preparation helps testers work faster and with fewer interruptions.
3. Vulnerability assessment checks
The next stage focuses on structured scanning. Teams should confirm the following steps are part of the plan.
- Use updated scanners with the latest signatures.
- Scan operating systems, databases, storage, network devices and cloud configurations.
- Identify outdated software versions and missing patches.
- Review misconfigurations across firewalls, IAM services and container workloads.
- Capture findings with severity ratings and evidence.
This forms the foundation for risk discovery.
4. Penetration testing checks
Manual testing helps identify gaps that scanners miss. These steps ensure the test reflects realistic attacker behaviour.
- Test authentication and session handling.
- Validate authorisation controls and privilege paths.
- Inspect input validation and error handling.
- Review business logic for overlooked attack flows.
- Test APIs for rate limits, broken object access and token weakness.
- Attempt safe exploitation to show real impact.
This section turns raw data into meaningful insight for leadership.
5. Reporting and remediation checks
A VAPT assessment is only valuable when results are clear and actionable. This part of the checklist focuses on quality reporting.
- Provide a detailed executive summary for leadership.
- Include technical findings with impact ratings.
- Offer clear guidance for remediation and patching.
- Prioritise fixes based on risk rather than count.
- Record false positives and justified exceptions.
A strong VAPT report helps teams move quickly and confidently toward closure.
6. Retesting and validation checks
This stage confirms that the fixes applied are strong enough. It also supports audit readiness.
- Validate that patches have been applied correctly.
- Confirm that old vulnerabilities do not reappear.
- Review new behaviours introduced during fixes.
- Update risk registers and documentation.
- Close assessment formally with sign off.
This final step demonstrates discipline and ensures improvements last.
Why BFSI, fintech and regulated sectors rely heavily on VAPT checklists
Regulated organisations operate under constant scrutiny. They manage sensitive financial data and run mission critical systems that cannot fail. A structured checklist helps them meet compliance expectations from regulators such as RBI, SEBI and CERT In while maintaining operational stability.
Banks and fintechs often work with complex APIs, legacy systems and cloud native platforms. A checklist prevents gaps during VAPT, especially when multiple teams collaborate on the same product. It also helps organisations show consistency in testing which is valuable during audits.
Insights from industry reports and leaders
Recent observations from industry leaders point to a shift. Organisations want clarity, faster insights and stronger follow through. They also want testing that adapts to rapid deployment cycles.
Reports highlight increasing exploitation of misconfigured cloud assets and exposed APIs. Leaders now use VAPT checklists to reduce blind spots and improve collaboration between teams. Security specialists highlighted the importance of predictable testing cycles supported by structured checklists. They suggested that checklists improve accountability and reduce common oversights that cause breaches.
These insights show a growing maturity across sectors where VAPT is treated as a continuous improvement practice rather than a one-time activity.
Conclusion
A VAPT checklist is more than a template. It is a plan that helps organisations test systems with clarity, improve collaboration and achieve better results from their assessments. It ensures nothing critical slips through the cracks and gives leadership confidence during audits and reviews.
If your organisation wants a structured and reliable approach to VAPT, our team can help. We create checklists tailored to your environment, your risk profile and your compliance obligations. With our VAPT services, assessments become smoother, clearer and more impactful.
Speak with our experts to design a VAPT checklist that strengthens your security and supports your compliance journey.
VAPT checklist FAQs
What is the purpose of a VAPT checklist during security assessments?
A VAPT checklist helps teams stay organised and avoid missing critical steps during testing. It creates clarity across engineering, security and compliance groups so everyone knows what to expect before the assessment begins. It also strengthens documentation which is valuable during audits.
How detailed should a VAPT checklist be for complex systems?
It should be detailed enough to cover key stages without overwhelming the team. Most organisations use a layered approach where core items stay fixed and system specific items get added based on risk. This keeps the checklist flexible while ensuring completeness.
Can a VAPT checklist improve the speed of remediation?
Yes, because a checklist offers structure and reduces confusion once findings arrive. Teams understand priorities earlier which speeds up patching and reduces back and forth between stakeholders. It also builds accountability across functions which helps close vulnerabilities faster.
Should internal teams or external vendors maintain the VAPT checklist?
Internal teams should manage the main checklist since they understand the environment best. External vendors can refine it with advanced testing practices and emerging risks. Working together helps create a checklist that stays practical, current and effective.