Software development today depends heavily on open-source libraries and third-party components. This approach speeds up delivery, but it also introduces hidden dependencies that are difficult to track over time. As applications evolve, teams often lose visibility into what software components are in use.
This lack of visibility becomes a problem when vulnerabilities are disclosed. Security teams struggle to determine whether they are affected, where the vulnerable components are deployed and how urgently action is required. The result is reactive decision making and unnecessary disruption.
SBOM vulnerability analysis addresses this challenge by bringing structure and clarity to software supply chains. It enables organisations to understand their software composition and continuously assess component level risk. For businesses focused on long term software supply chain security, this capability plays a critical role.
What is SBOM vulnerability analysis?
SBOM vulnerability analysis is the process of evaluating a Software Bill of Materials to identify known security vulnerabilities within the components used to build an application. An SBOM is a detailed inventory that lists libraries, frameworks, third party packages and transitive dependencies, along with version information.
Vulnerability analysis adds security context to this inventory by continuously comparing components against trusted vulnerability databases. When a new vulnerability is disclosed, affected components are identified and mapped to the applications and environments where they are used.
This approach turns a static list of software components into an active security control. Instead of relying on manual checks or delayed discovery, teams gain timely insight into exposure across their software estate.
Why software supply chain security needs deeper visibility
Modern software supply chains are complex and interconnected. A single application may rely on hundreds of components, many of which are introduced indirectly. These transitive dependencies are often invisible to development and security teams.
Attackers understand this complexity. Compromising a widely used component can impact multiple organisations at once. Without clear visibility, businesses are left reacting to disclosures without understanding their true exposure.
SBOM vulnerability analysis provides the depth of insight required to manage this risk effectively. It enables organisations to answer critical questions quickly and accurately, including:
- Which vulnerable components are in use
- Which applications depend on them
- Where those applications are deployed
- How severe the exposure is in context
This clarity is essential for maintaining control over software supply chain risk.
Difference between vulnerability scanning and SBOM vulnerability analysis
Traditional vulnerability scanning focuses on identifying weaknesses in running systems, applications or infrastructure. These tools examine exposed services, configurations and runtime behaviour to detect known issues. While valuable, this approach often provides limited insight into the underlying software composition.
SBOM vulnerability analysis works at a different layer. It examines the components that make up an application, regardless of whether they are currently exposed or detected at runtime. This allows teams to identify vulnerable libraries that may not surface during traditional scans.
Key differences include:
- Vulnerability scanning focuses on deployed assets, while SBOM analysis focuses on software components
- Runtime scans may miss dormant or indirectly used libraries, while SBOM analysis captures transitive dependencies
- SBOM analysis enables earlier detection during development and build stages
Used together, both approaches provide stronger coverage across the software lifecycle.
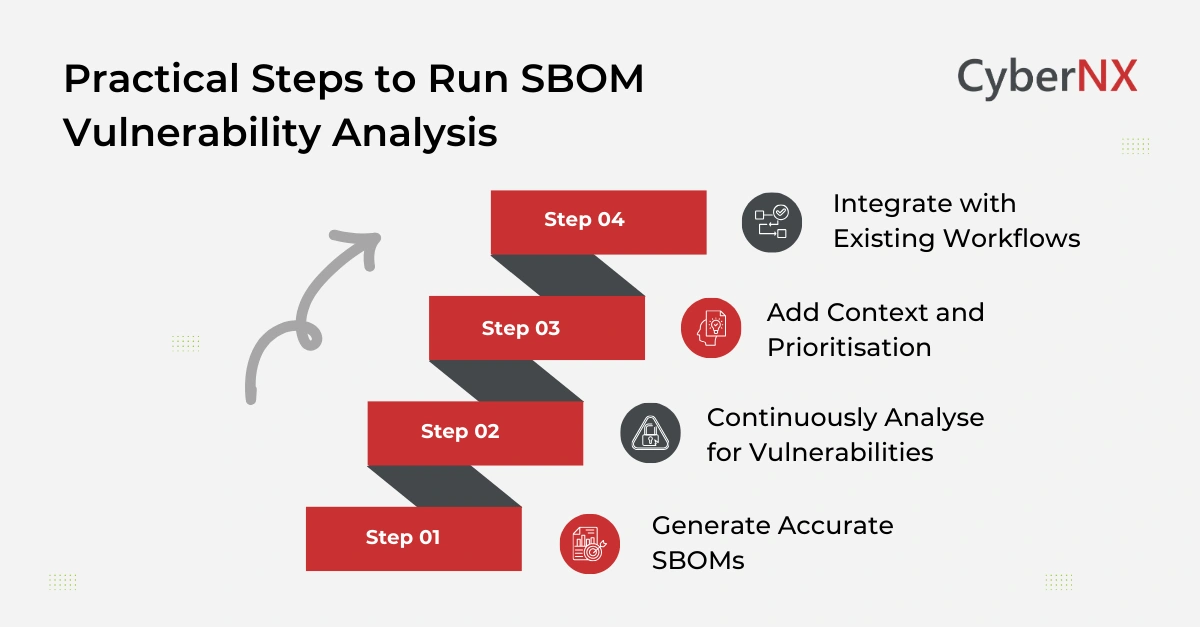
Practical steps to run SBOM vulnerability analysis
Here is a step-by-step guide to conducting vulnerability analysis related to SBOM:
1. Generate accurate SBOMs
The first step is generating an SBOM for each application. This should be automated and integrated into build or packaging processes to ensure consistency. The SBOM must include direct and indirect dependencies with accurate version information.
2. Continuously analyse for vulnerabilities
Once generated, SBOMs should be continuously analysed against up-to-date vulnerability databases. This ensures that newly disclosed vulnerabilities are detected without delay. One time analysis is insufficient, as software risk changes constantly.
3. Add context and prioritisation
Raw vulnerability data is not enough. Effective vulnerability analysis adds context such as severity, exploit availability and usage within the application. This enables teams to prioritise remediation based on real exposure rather than volume of findings.
4. Integrate with existing workflows
Findings should flow into existing security and development workflows. Clear ownership between teams ensures that vulnerabilities are addressed efficiently. Over time, organisations can refine prioritisation based on business impact and operational risk.
How businesses benefit from SBOM vulnerability analysis
Such analysis delivers both security and operational benefits. Improved visibility reduces uncertainty and supports faster decision-making during vulnerability disclosures.
Businesses benefit in several practical ways:
- Faster identification of affected applications during security events
- Reduced remediation time through targeted fixes
- Fewer emergency releases and unplanned outages
- Stronger collaboration between security and engineering teams
- Improved audit readiness and stakeholder confidence
By understanding software composition at a deeper level, organisations gain control rather than reacting under pressure.
Where organisations often struggle
Adopting SBOM vulnerability analysis is not just a technical exercise. Many organisations struggle with ownership and integration. Without clear responsibility, SBOMs become documentation rather than actionable insight.
Successful programmes treat vulnerability analysis as a shared discipline. Security teams provide governance and prioritisation, while engineering teams own remediation. Starting with critical applications helps build momentum and demonstrate value early.
Conclusion
Software supply chains are foundational to modern digital businesses, but they introduce risk when left unmanaged. SBOM vulnerability analysis provides a practical way to understand software composition and continuously assess component level exposure.
By combining visibility with ongoing vulnerability assessment, organisations strengthen software supply chain security in a measurable and sustainable way. The result is calmer incident response, better prioritisation and greater confidence across teams.
For businesses looking to improve control over their software risk, SBOM vulnerability analysis offers a strong starting point.
Speak to our experts to explore how vulnerability analysis can support your security strategy.
Our indigenously built SBOM management platform is designed to meet SEBI, RBI and CERT-In mandates related to supply chain security. It helps organisations boost security capabilities by building clarity, reducing disruption and protecting what you deliver.
SBOM vulnerability analysis FAQs
Is SBOM vulnerability analysis relevant for internally developed software?
Yes. Internally developed applications often rely heavily on third party components. SBOM vulnerability analysis helps identify and manage the risk introduced by these dependencies, even when the core application code is developed in house.
How often should vulnerability analysis related to SBOM be updated?
It should run continuously or at least daily. Vulnerabilities are disclosed frequently, and delayed analysis increases exposure. Automated monitoring ensures timely awareness without manual effort.
Does SBOM related vulnerability analysis require major process changes?
Not necessarily. Many organisations integrate SBOM generation into existing build pipelines. The key change is using the output actively to inform security and development decisions.
Can SBOM vulnerability analysis help during incident response?
Yes. When a vulnerability is disclosed, SBOM analysis quickly shows where the affected component is used. This reduces investigation time and supports faster, more accurate containment.