Software supply chain risk keeps growing. Open-source libraries, third party components and build pipelines moving at break-neck speed. Most security leaders know they need visibility and many already generate an SBOM. But few know what to do next.
This is where an SBOM maturity model helps. It shows how far your organisation has come and what progress looks like. Not theory or perfection but practical steps that fit real teams.
In this guide, we share what we see working across enterprises. We focus on outcomes, reduced exposure, provide faster response and clear ownership. If you are a CISO or IT head trying to bring order to software risk, this guide is for you.
What is SBOM maturity model?
An SBOM maturity model describes how effectively an organisation creates, manages and uses its software bill of materials. It is not about producing a file for compliance. It is about turning component data into security decisions.
At low maturity, SBOMs exist in silos. At higher maturity, they inform risk management, procurement and incident response.
The maturity model helps you answer three hard questions.
- Do we know what software we run?
- Can we trust it?
- Can we act fast when something breaks?
Without a model, progress feels random. With one, improvement becomes measurable.
Why CISOs struggle without an SBOM maturity model
Many leaders start SBOM initiatives with good intent. They quickly hit friction but somehow the approach derails. Here are some of the common reasons we find why CISOs struggle:
First, tooling overload. Different teams generate different SBOM formats. Lack of alignment causes major problems. Teams should weigh in different formats like CycloneDX and SPDX and use the same one.
Second, no clear ownership leads to no accountability. Security teams look at SBOM for insight. On the other hands, your engineering team who wants speed may find SBOM as an impediment. Then there is procurement team who want assurance. Bringing them all together is essential.
Third, no shared definition of success. Is success an SBOM file, a dashboard or fewer incidents. This needs to be answered clearly.
An SBOM maturity model creates a common language. It aligns security, engineering and leadership around outcomes.
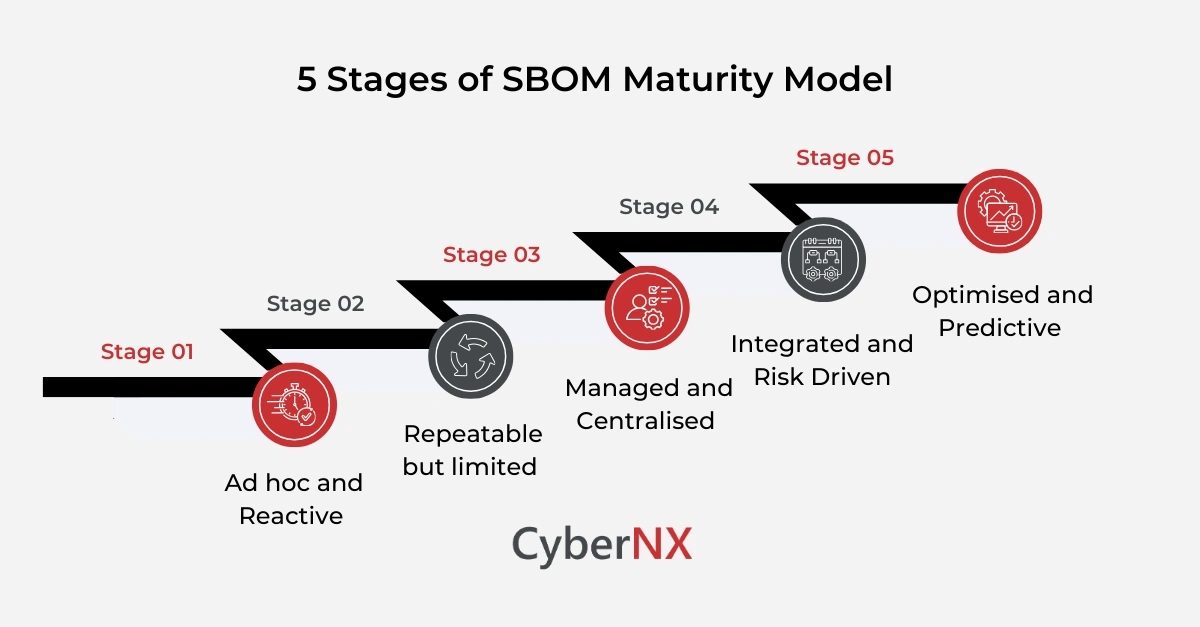
Core stages of the SBOM maturity model
Most organisations move through clear stages. The names vary. The pattern does not.
Stage 1: Ad hoc and reactive
SBOMs appear only when required. Often after a customer request or audit.
Characteristics include.
- Manual generation
- No standard format
- Stored locally or emailed
- Rarely updated
Risk remains high. Teams lack confidence in their own software.
Stage 2: Repeatable but limited
SBOM generation becomes part of some build processes. Coverage improves.
You start to see.
- Automated tools in CI pipelines
- Basic component inventories
- Known open source usage
However, SBOMs still sit apart from security workflows. They inform reports, not action.
Stage 3: Managed and centralised
This is where the SBOM maturity model starts to deliver value.
At this stage.
- SBOMs follow a standard format
- Central repositories exist
- Ownership is defined
- Updates occur regularly
Security teams begin linking SBOM data with vulnerability feeds.
Response times improve. Visibility increases. Confidence grows.
Stage 4: Integrated and risk driven
SBOMs become part of everyday security decisions.
Here, organisations.
- Map SBOM data to asset criticality
- Prioritise vulnerabilities based on real exposure
- Support incident response with accurate component insight
The maturity model now supports business risk conversations.
Stage 5: Optimised and predictive
Few organisations reach this stage. Those that do gain a real advantage.
At this level.
- SBOMs inform procurement decisions
- Risk trends influence architecture choices
- Continuous monitoring replaces periodic checks
Security shifts from chasing issues to shaping outcomes.
How to assess your current SBOM maturity
Assessment does not need to be complex. Ask simple, honest questions.
- Do we generate SBOMs for all applications
- Are they updated automatically
- Can we query them during an incident
- Do leaders trust the data
Map answers to maturity stages and gaps become visible. An SBOM maturity model works best when used as a roadmap, not a scorecard.
Key benefits of advancing your SBOM maturity model
Improvement brings tangible gains.
- Faster vulnerability response: When a new flaw emerges, teams know where it exists. Response shifts from panic to process.
- Stronger supplier conversations: SBOM maturity improves trust with customers and partners. You can show control, not claims.
- Reduced operational noise: Security teams stop chasing low risk alerts. Focus returns to what matters.
- Better regulatory readiness; As SBOM expectations grow, mature programmes adapt with less disruption.
Many organisations lack time or specialist skills. This slows momentum. A trusted partner brings structure. Clear stages and proven practices. At CyberNX, we work alongside teams to embed SBOM maturity into existing security workflows.
Conclusion
An SBOM maturity model turns visibility into confidence. It replaces guesswork with insight. It helps leaders make informed decisions about software risk. This guide is not about chasing the highest level. It is about moving forward with purpose. Every step strengthens resilience. Every improvement reduces uncertainty.
If you want to assess your current maturity model and build a practical roadmap, speak with CyberNX. A focused conversation can clarify next steps and unlock real value. Our SBOM management tool helps businesses automate SBOM generation and meet regulatory requirements with ease. Request a demo today.
SBOM maturity model FAQs
How often should SBOM maturity be reviewed?
Review maturity at least quarterly. Faster moving environments may benefit from monthly check ins.
Can SBOM maturity support DevSecOps goals?
Yes. Mature SBOM practices integrate naturally with CI pipelines and developer workflows.
Is SBOM maturity relevant for legacy applications?
Absolutely. Legacy systems often carry the highest hidden risk and benefit greatly from visibility.
Does SBOM maturity help with customer trust?
Yes. Clear SBOM practices demonstrate control and transparency during security reviews.