SBOM implementation has moved from a security talking point to a board-level requirement. Regulations are tightening and auditors are asking sharper questions. Meanwhile, software supply chains keep growing more complex. Most enterprises now rely on hundreds of open source and third-party components, often without full visibility.
We see the same concern shared by security leaders across industries. You want to implement SBOMs, but the path feels unclear. Which format should you choose? How do you align SBOMs with existing development workflows? And how do you make the output meaningful for auditors, not just security teams?
This step-by-step SBOM implementation guide answers those questions. It is written for decision-makers who want clarity, structure, and compliance alignment, especially for Indian enterprises operating under regulatory oversight.
What SBOM implementation really means
Before jumping into tools and formats, it helps to reset expectations.
An SBOM is not a one-time document. SBOM implementation is an ongoing capability. It involves tooling, process changes, and governance. Done well, it gives you continuous visibility into software components, known vulnerabilities, licences, and ownership.
Done poorly, it becomes another report that no one trusts.
Our experience shows that successful SBOM implementation starts with understanding your own environment, not copying what others are doing.
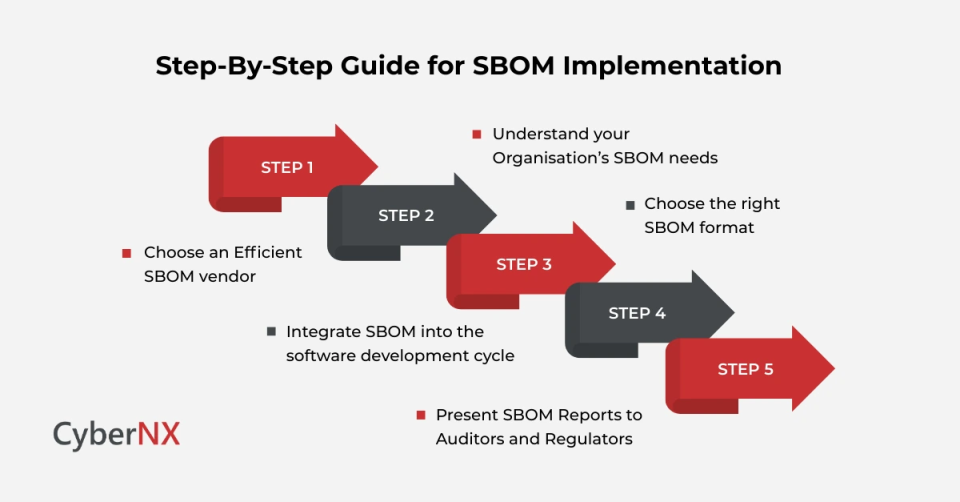
Step 1: Understand your organisation’s SBOM needs
Every SBOM implementation should begin with a clear internal assessment.
1. Identify why you need SBOMs
Different drivers lead to different SBOM designs. Common drivers include:
- Regulatory and audit requirements
- Third-party risk management
- Vulnerability management and incident response
- Customer assurance and contract obligations
Be honest about your primary driver. An SBOM built only for audits will look very different from one designed for real-time vulnerability management.
2. Define scope early
Decide where SBOMs will apply. For example:
- Internally developed applications
- Customer-facing products
- Third-party software procured from vendors
- Cloud-native workloads and containers
Trying to cover everything on day one often leads to delays. Start with high-risk or regulated applications.
3. Clarify who will consume SBOMs
SBOMs are not just for security teams. They may be reviewed by:
- Internal auditors
- External regulators
- Customers
- Procurement and legal teams
Understanding the audience helps shape the format, level of detail, and reporting style.
Industry insight
Gartner notes that SBOM programmes fail most often due to unclear ownership and undefined consumers. Clear accountability reduces friction later.
Step 2: Choose an efficient SBOM vendor
Tool selection is one of the most visible SBOM implementation decisions. It also carries long-term consequences. Here are some factors to consider while choosing an SBOM vendor.
1. Core capabilities to look for
An effective SBOM vendor should offer:
- Automated SBOM generation across languages and build systems
- Continuous updates aligned with CI/CD pipelines
- Vulnerability and licence enrichment
- Export in standard formats
- Integration with existing security tooling
Avoid tools that generate static files with no update mechanism. SBOMs age quickly.
2. Regulatory alignment for Indian enterprises
Indian organisations must pay close attention to regulatory expectations. SBOM tools should support audit and reporting needs aligned with SEBI and CERT-In SBOM guidelines.
This includes:
- Clear traceability of software components
- Evidence of vulnerability monitoring
- Ability to share reports securely during audits or incidents
While SBOMs are not yet mandated across all sectors, regulators increasingly expect demonstrable supply chain visibility.
3. Vendor transparency matters
Ask vendors direct questions:
- How do you discover transitive dependencies?
- How frequently is vulnerability data refreshed?
- Can SBOMs be regenerated automatically after every build?
Strong answers indicate maturity. Vague responses usually signal future pain.
Step 3: Choose the right SBOM format
SBOM implementation depends heavily on format choice. SBOM formats define how information is structured, shared, and understood.
1. Common SBOM formats explained
The two most widely adopted formats are:
- SPDX: SPDX focuses on licence clarity and legal compliance. It is widely recognised by auditors and regulators.
- CycloneDX: CycloneDX is optimised for security use cases. It integrates well with vulnerability management and DevSecOps tools.
2. How to choose between formats
Consider these factors:
- If licence compliance and audits are primary, SPDX often fits better
- If security monitoring and automation are key, CycloneDX offers flexibility
- Some organisations support both, depending on audience
What matters most is consistency. Pick one format and standardise its use across teams.
Step 4: Integrate SBOM into the software development cycle
This is where SBOM implementation either succeeds or stalls.
1. Shift SBOMs left
SBOM generation should happen early in the development process, not just before release. Integrating SBOM tools into CI/CD pipelines allows teams to:
- Detect vulnerable components during builds
- Block risky releases automatically
- Maintain up-to-date inventories without manual effort
When SBOMs are created late, they become reactive and incomplete.
2. Align with DevSecOps workflows
SBOMs should complement existing DevSecOps practices. For example:
- Link SBOM outputs to vulnerability scanners
- Feed component data into risk dashboards
- Alert teams when new CVEs affect existing software
Security teams gain visibility. Developers gain context and no one works in isolation.
3. Keep ownership clear
Assign responsibility for SBOM maintenance. In many organisations:
- Development teams generate SBOMs
- Security teams review and monitor them
- Governance teams use them for audits
Clear ownership prevents gaps and duplication.
Practical tip
Organisations that embed SBOM checks into build pipelines report faster remediation during supply chain incidents, according to recent OWASP community studies.
Step 5: Present SBOM reports to auditors and regulators
SBOM implementation often reaches its true test during audits. Therefore, a good SBOM report is essential.
1. Focus on clarity, not volume
Auditors rarely want raw JSON or XML files. They want assurance. Provide:
- A summary view of component risks
- Evidence of vulnerability monitoring
- Records of remediation actions
Keep technical detail available, but do not lead with it.
2. Map SBOM data to compliance objectives
Translate SBOM outputs into compliance language. For example:
- Show how SBOMs support secure development practices
- Demonstrate third-party risk visibility
- Link vulnerability management to incident response plans
This helps auditors understand intent and maturity.
3. Maintain versioned records
Store historical SBOMs securely. Versioning shows:
- How software changed over time
- When vulnerabilities were introduced or fixed
- Evidence of continuous control
This level of traceability builds trust during regulatory reviews.
SBOM implementation challenges and how to avoid them
Many organisations face similar hurdles. One challenge is tool sprawl. Adding SBOM tools without integration increases noise. Another is lack of governance. SBOMs without policy quickly lose relevance.
We recommend starting small, proving value, then scaling across teams and products. SBOM implementation is a journey, not a checkbox exercise.
Conclusion
SBOM implementation does not need to be complex or disruptive. With a clear understanding of your needs, the right vendor, a suitable format, and strong integration into development workflows, SBOMs become a powerful control rather than a compliance burden.
At CyberNX, our team deploy in-house built, AI-enabled SBOM management tool to help you design SBOM programmes that support security, compliance, and business growth. If you are planning SBOM implementation or reviewing an existing approach, a focused consultation can make the difference between paperwork and real resilience. Talk to our experts to start your SBOM journey with confidence.
SBOM Implementation FAQs
How long does SBOM Implementation typically take?
Initial implementation can take 4–8 weeks, depending on application complexity and automation maturity.
Can SBOM Implementation work with legacy applications?
Yes. While automation may be limited, partial SBOMs can still provide valuable visibility for regulated systems.
Do regulators mandate a specific SBOM format in India?
Currently, regulators focus on outcomes rather than formats. Organisations should choose formats that support automation and auditability.
How often should SBOMs be updated?
SBOMs should be generated with every build or release to remain accurate and defensible.