Software we use every day are rarely built from scratch. Writing an application includes the use of open-source libraries which are licensed for free use across the world. Many of these may carry hidden vulnerabilities and pose risks.
This is where Software Bill of Materials (SBOM) helps. It acts like a detailed ingredient label for software. It reveals what’s inside, who built it, how secure it is and whether it can be trusted. As governments and regulators across India tighten oversight – including SEBI, RBI and CERT-In, SBOMs have become more than a best practice. They are a must-have for security and compliance essential in 2026 and beyond.
What is a Software Bill Of Materials (SBOM)?
SBOM is a detailed, machine-readable inventory of all components that make up a software application. Think of it as a digital parts list for software, listing not only the components themselves, but also metadata such as their versions, suppliers, and licensing details.
Beyond just naming what’s inside, it also maps out how these components relate to each other, tracks cryptographic hashes to ensure integrity and records encryption methods used.
This comprehensive visibility enables organizations to understand exactly what’s running in their environment, right down to the libraries buried deep within dependencies. In an era of escalating supply chain attacks, this visibility is essential.
Key SBOM Components
Here are some key Software Bill of Material components you need to know:
1. Component Information
At its core, an SBOM lists each software component included in an application. This includes:
- Component Name and Version: Pinpoints the exact code elements in use, preventing ambiguity.
- Supplier Information: Identifies who created or provided the component – critical for tracking source reliability.
- License Details: Highlights any open-source or proprietary licensing conditions that could impact legal or operational obligations.
- Cryptographic Hashes: Used to verify component integrity, ensuring no tampering has occurred between development and deployment.
2. Dependency Mapping
Modern applications rely on layers of dependencies – many of which are automatically pulled in during builds. SBOMs map:
- Direct Dependencies: Libraries or modules directly included by the developer.
- Transitive Dependencies: Secondary libraries pulled in by direct dependencies.
- Relationship Hierarchy: The full tree showing how components are interlinked.
- Known Unknowns: Components that may exist within code but are not explicitly declared—flagged as potential risks.
3. Security Information
An Software Bill of Material isn’t just a static list – it embeds useful security metadata:
- Encryption Methods Used: Ensures cryptographic practices meet industry standards.
- Access Control Details: Defines who can use, modify, or interact with components.
- Update Frequency: Tracks how regularly components receive security or functionality updates.
- Vulnerability Status: Maps known vulnerabilities to the components in use, helping prioritize remediation.
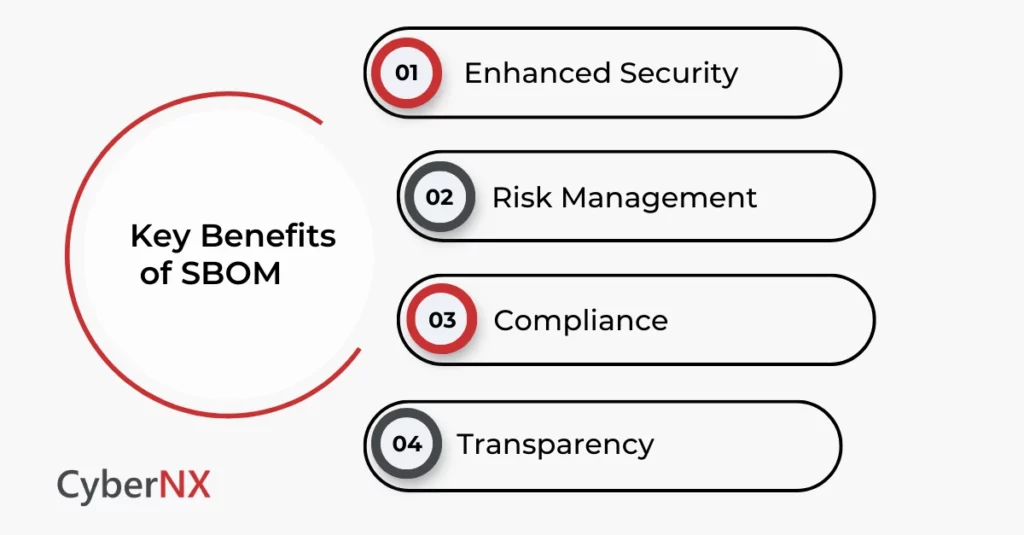
Benefits of Software Bill Of Materials
It offers many benefits to organizations, which are discussed below:
1. Enhanced Security
With SBOMs, organizations can immediately assess whether they’re affected by a newly disclosed vulnerability—without manual investigation. This rapid visibility shortens response times and minimizes risk exposure.
2. Risk Management
It helps identify and mitigate risks throughout the software supply chain. By exposing outdated or unsupported components, teams can act before weaknesses become exploitable.
3. Compliance
Regulatory bodies like SEBI and RBI increasingly require SBOMs as part of their cybersecurity frameworks. Maintaining Software Bill of Materials help businesses demonstrate compliance with national standards and avoid penalties.
4. Transparency
It also creates operational clarity. It gives teams – and auditors – a real-time view of what software is composed of, how it evolves, and where it might pose a liability. This transparency builds trust across the organization and with external stakeholders.
SBOM Requirement of SEBI CSCRF
The Securities and Exchange Board of India (SEBI) mandates that all Regulated Entities (REs) adopt a Software Bill of Materials as part of its Cyber Security and Cyber Resilience Framework (CSCRF).
The objective is clear: increase transparency and accountability within critical digital infrastructure. By making SBOMs mandatory, SEBI aims to strengthen defences against threats hidden deep in software dependencies.
This requirement is not just a formality – it brings tangible benefits. SBOMs under SEBI guidelines ensure complete awareness of software components, their cryptographic hashes, and licensing data.
Organizations gain the ability to monitor vulnerabilities and reduce third-party risk. Importantly, it enables better auditability, helping regulators verify that only authorized and secure software elements are deployed.
Related Content: Understanding SBOM Requirements of SEBI CSCRF
RBI Requirements on Software Bill Of Materials
The Reserve Bank of India (RBI) has set out clear expectations for software supply chain management among banks, NBFCs, and other financial entities. These guidelines focus on reducing systemic risk and ensuring continuity of critical financial services, even in the face of cyber threats. At the heart of these efforts is the adoption of SBOMs.
Financial institutions must maintain detailed inventories of all software components. They are expected to continuously monitor vulnerabilities – especially those linked to third-party code.
Patch management processes must be swift and traceable. Institutions also need to conduct routine risk assessments to identify potential threats across the software lifecycle.
To understand how financial institutions can align with these RBI guidelines using SBOMs, read our detailed blog RBI SBOM Compliance.
CERT-In Requirements on Software Bill Of Materials
By requiring machine‐readable metadata that includes component names, versions, cryptographic hashes, and supplier details, CERT-In pushes for proactive tracking of vulnerabilities throughout the software lifecycle.
Organizations are expected to store SBOMs in secure, version-controlled repositories and update them regularly, especially when new patches or updates are released.
Crucially, CERT-In calls for SBOM integration into development pipelines, so that they are automatically generated during CI/CD workflows. This ensures that every release – even minor or iterative ones – remains fully traceable. Audits and incident investigations become simpler and faster because all component history is recorded and accessible.
Read our detailed blog CERT-In SBOM Guidelines to explore implementation steps, benefits, and compliance strategies.
Managing Software Bill Of Material: Best Practices
Based on the experience of handling many SBOM projects, many companies end up making mistakes while implementing SBOM. Therefore, we have derived some of the best practices that need to be followed for successfully managing SBOM.
1. Generation & Collection
Start by automating SBOM creation within your CI/CD pipelines. Use standardized formats like SPDX or CycloneDX to ensure compatibility. Include both direct and transitive dependencies and verify component integrity using scanning tools.
2. Storage & Management
Centralize your SBOMs in a secure, access-controlled repository. Implement version control to track changes over time and link them with your deployment environments. Maintaining a detailed audit trail helps during compliance reviews.
3. Analysis & Response
Don’t just store SBOMs—use them. Monitor for emerging vulnerabilities, rank them based on business risk, and establish response SLAs. Automation can alert teams when critical issues arise, allowing faster mitigation.
4. Governance & Compliance
Define formal SBOM policies and assign roles for ownership. Require vendors to provide them as part of their software packages. Conduct internal audits regularly to ensure the process aligns with industry and regulatory expectations.
How CyberNX Can Help?
CyberNX delivers an end-to-end SBOM management solution that ensures total visibility, regulatory compliance, and real-time security.
1. Automated Collection
We integrate seamlessly into your CI/CD workflows, collecting SBOMs from multiple sources. Our platform supports container and image registry scanning and enables vendor SBOM ingestion—covering the full software lifecycle.
2. Centralized Management
CyberNX centralizes your SBOMs in a secure repository with version control, data normalization, and full cross-environment visibility. You can track how software components evolve and ensure consistency across teams.
3. Continuous Analysis
Our engine performs real-time vulnerability scanning and risk-based prioritization. It continuously assesses the impact of new threats, automatically identifying exposure points before attackers do.
4. Actionable Insights
With CyberNX, decision-makers get executive dashboards, regulatory compliance reports, trend analyses, and customizable KPIs—empowering faster and more informed action.
5. Flexible Deployment Options
Whether you’re a large enterprise or a regulated financial institution, CyberNX offers deployment models that meet your operational and compliance needs:
- On-Premises Deployment: Full control over data and infrastructure.
- SaaS Deployment: Rapid setup with ongoing updates and maintenance managed by us.
Conclusion
Knowing what’s inside your software is no longer optional. As the complexity of codebases grows and threats become more sophisticated, visibility into software components has become the foundation of secure digital operations. They enable faster vulnerability response, stronger vendor controls, and clearer regulatory alignment.
Our advanced SBOM tool is purpose-built for entities regulated by SEBI, RBI and other leading cybersecurity standards. Plus, it ensures that your complex system stands up to the security challenges of today and tomorrow.
Our in-house built SBOM generation and management tool also helps your business build a smarter, more resilient software supply chain confidently. Ready to take the next step? Contact us today.
Software Bill Of Materials FAQs
Can SBOMs prevent software supply chain attacks?
They don’t act as a firewall, but they significantly strengthen your defence strategy. By providing a full inventory of all software components—including hidden third-party dependencies—they enable faster identification of known vulnerabilities when an attack or exploit is discovered. This helps organizations respond rapidly and limit exposure before attackers can take advantage.
How often should SBOMs be updated?
They should be refreshed every time there’s a change in your software – whether it’s a new feature, patch, or even a minor dependency update. Stale SBOMs can give a false sense of security. Automating the update process within CI/CD pipelines ensures the SBOM always reflects the live production environment, minimizing risk.
Is generating an SBOM resource-intensive for development teams?
It doesn’t have to be. Modern tools can automatically generate it as part of your build or deployment pipeline, removing manual effort. Once integrated, the process becomes routine – delivering real-time component insights without slowing down development or adding extra work for engineers. Find out which are the best tools with our blog Top 5 Software Bill Of Materials – SBOM Tools.
Can SBOMs be shared with customers or partners?
Yes, and sharing SBOMs is becoming a trust-building measure, especially in regulated or high-risk industries. Providing them to customers helps them assess security and compliance risks in your software. However, it’s important to sanitize sensitive information and provide context to ensure it is meaningful and safe to share externally.