SaaS companies move fast. Features ship weekly, integrations expand quietly and dependencies grow in the background. Over time, even disciplined engineering teams lose full visibility into what actually runs their platform. This is the problem SaaSBOM is designed to solve.
A SaaSBOM gives SaaS companies a clear, structured view of the software components, services and dependencies behind their applications. For founders, CISOs and product leaders, it turns unknown risk into something visible, manageable and measurable.
In this guide, we explain what SaaSBOM really means, why it matters specifically for SaaS businesses, and how to implement it in a way that supports growth rather than slowing teams down.
What is SaaSBOM?
SaaSBOM stands for Software as a Service Bill of Materials. It is an inventory that documents everything that makes up a SaaS product. This includes open-source libraries, commercial software, APIs, microservices, cloud services and third-party integrations.
Unlike traditional SBOMs, a SaaSBOM reflects how SaaS products are delivered and operated. Customers do not install your software. They rely on you to run it securely on their behalf.
That trust comes with responsibility.
A SaaSBOM helps SaaS companies answer important questions. What components are running in production right now? Which third parties can access customer data? How quickly can we assess exposure when a vulnerability is disclosed?
Without clear answers, risk builds quietly.
The software supply chain risks unique to SaaS
SaaS platforms depend heavily on external components. Open-source frameworks, cloud-native services and API-based integrations enable speed and scale.
Each dependency also expands the attack surface.
A vulnerability in an open-source library can spread across environments within hours. A compromised third-party service can expose customer data without warning. Even small changes in cloud configuration can introduce gaps that go unnoticed.
Our experience shows that many SaaS teams underestimate these risks until a customer audit or security incident forces urgent visibility.
SaaSBOM brings that visibility earlier, when it is easier to act.
How SaaSBOM supports SaaS growth, not just security
Security controls often get framed as blockers. SaaSBOM should not be one of them.
For SaaS companies, a well-maintained SaaSBOM improves day-to-day efficiency. Engineering teams spend less time chasing unknown components. Security teams respond faster to emerging threats. Sales teams handle security questionnaires with confidence.
Most importantly, SaaSBOM builds credibility with enterprise customers who increasingly expect evidence of secure development and operations.
Visibility enables speed. Not the other way around.
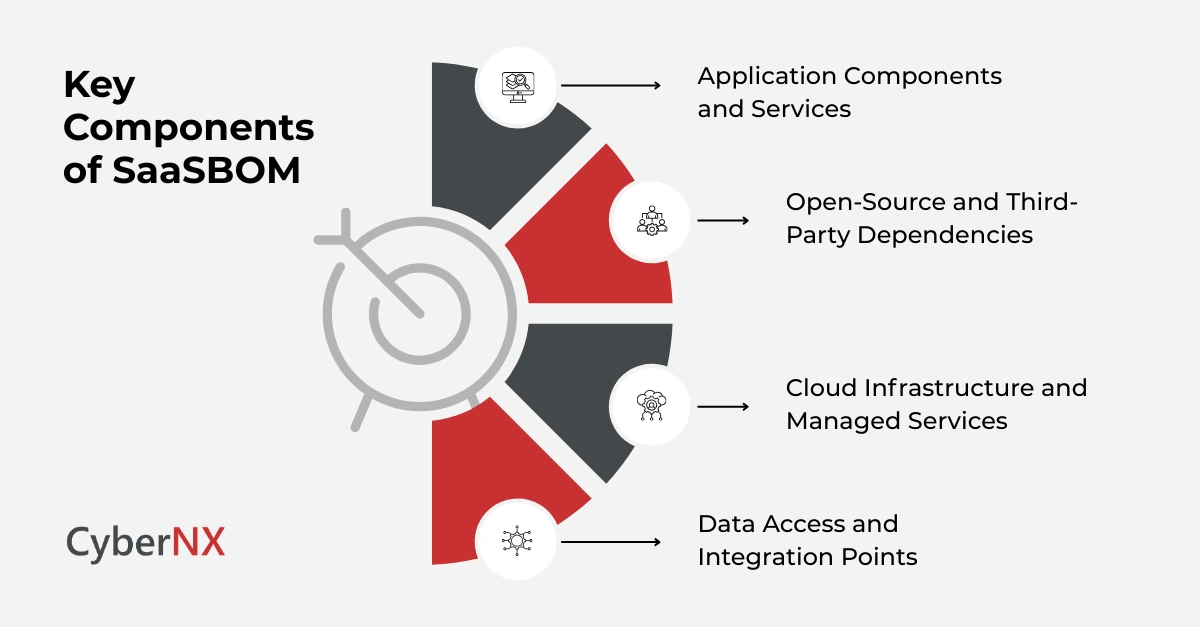
The building blocks of an effective SaaSBOM
A SaaSBOM should reflect how your platform actually runs, not how architecture diagrams suggest it runs.
1. Application components and services
This includes backend services, frontend frameworks, APIs and internal tools that support the SaaS offering. Each component should have clear ownership, versioning and deployment context. Clear ownership prevents delays when incidents occur.
2. Open-source and third-party dependencies
Open-source libraries power most SaaS platforms. A SaaSBOM records their versions, licences and update cadence. This visibility reduces exposure to known vulnerabilities and helps manage licence compliance.
3. Cloud infrastructure and managed services
SaaS environments rely heavily on cloud-native services. Databases, messaging systems, identity services and monitoring tools are all part of the supply chain. SaaSBOM helps teams understand shared responsibility boundaries and associated risks.
4. Data access and integration points
Integrations often introduce the highest level of risk. A SaaSBOM should document how data flows between services and which external systems can access customer information. This supports stronger access control and audit readiness.
Why SaaSBOM is becoming a customer expectation
Enterprise buyers are more security-aware than ever. Security questionnaires now go beyond policies and certifications. Customers want clarity.
They ask how vulnerabilities are managed. How quickly disclosures are handled. How third-party risk is controlled.
A SaaSBOM allows SaaS companies to answer these questions clearly and consistently. It signals maturity and readiness to operate at scale.
SaaSBOM and increasing regulatory pressure
While SaaSBOM is not yet mandated in most regions, the direction is clear. Governments and industry bodies are pushing for greater transparency across software supply chains. SaaS companies that adopt SaaSBOM early are better prepared as requirements evolve. They avoid rushed compliance efforts and reduce long-term cost and disruption.
How CyberNX helps SaaS companies operationalise SaaSBOM
We work with SaaS teams at different stages of growth, from fast-scaling startups to mature platforms serving enterprise customers.
Our approach stays practical. We help you identify what matters most, build a SaaSBOM that reflects real-world operations, and integrate it into existing engineering and security workflows.
Our experience shows that small changes, applied consistently, often deliver the biggest improvements in visibility and control.
Conclusion
For SaaS companies, trust is the product. Customers rely on you to operate secure, resilient services every day.
This SaaSBOM guide shows that transparency is not a burden. It is a strength. By understanding your software supply chain, you reduce risk, respond faster to threats and build confidence with customers and partners.
If you want to strengthen your SaaS security posture and prepare for future expectations, SaaSBOM is a strong place to start.
Looking to build or mature your SaaSBOM without slowing development velocity? Speak with our experts to explore our SBOM management tool capabilities and a practical, SaaS-focused approach that fits your scale and growth plans.
SaaSBOM FAQs
Is SaaSBOM only relevant for large SaaS companies?
No. Early-stage SaaS companies often gain the most value from SaaSBOM. Building visibility early prevents blind spots as the platform grows. It is far easier to maintain an accurate view of dependencies when systems are simple than to reconstruct one after years of rapid expansion.
How is SaaSBOM different from a traditional SBOM?
A traditional SBOM focuses on software that customers install and run themselves. SaaSBOM reflects how SaaS products actually operate. It covers hosted services, cloud infrastructure, integrations and runtime dependencies that customers never see but rely on every day.
Who should own SaaSBOM in a SaaS organisation?
SaaSBOM works best with shared ownership. Security teams define the requirements and risk priorities. Engineering and DevOps teams keep the information accurate as systems change. This shared model ensures the SaaSBOM stays current and useful rather than becoming a static document.
Can SaaSBOM support incident response?
Yes. During an incident, time matters. A SaaSBOM allows teams to quickly identify which services, dependencies and integrations are affected. This speeds up impact analysis, supports clearer communication and helps teams focus remediation where it matters most.