Security teams often sense gaps in their defences but struggle to confirm how those gaps behave under real pressure. A red team engagement helps answer those unknowns. It studies how an adversary could move through an environment and focuses on goals, not just vulnerabilities. It also shows how people, processes and technology respond when tested together.
This guide explains red team engagement, highlights leadership considerations, success signals, and how a well-planned engagement supports overall resilience. We avoid the usual step-by-step simulation approach and instead focus on strategy, clarity and outcomes that help CISOs and leadership teams make informed decisions.
What is a red team engagement?
Business leaders often get confused between red teaming, red teaming exercise and red team engagement, and rightly so. That’s why defining each of them is important.
Red teaming is an umbrella term, under which comes everything else. It refers to offensive security activities that exploit and expose weaknesses across the entire digital ecosystem.
A red team exercise is a single, time-bound simulation where an offensive security team emulates a real attacker to test specific aspects of an organization’s defences, following a defined scope, objectives, and rules of engagement.
In contrast, a red team engagement refers to the broader, formal service arrangement under which one or more exercises are planned and executed; it includes scoping, operational planning, communication protocols, documentation, reporting, and post-assessment activities.
This approach creates depth. It looks beyond individual technical weaknesses, uncovers how small gaps can combine to form meaningful attack paths. It also evaluates defensive reactions, communication flows and decision-making timelines. This separates red teaming from traditional assessments.
How red team engagement differs from other testing methods
Many organisations confuse red teaming with penetration testing or purple teaming. Each has a purpose, but their focus is different. A red team engagement in cybersecurity is objective-driven. It uses creativity and persistence. It treats the environment like a real attacker would.
Penetration testing asks, “Where are the weaknesses?” Red teaming asks, “What can someone achieve through your weaknesses?” Purple teaming asks, “How can offensive and defensive teams learn together?”
Understanding this distinction helps organisations choose the right approach for their goals.
Why organisations choose red team engagement
Growing businesses face a wider attack surface. Identity sprawl. Supply chain complexity. Expanding cloud workloads. These shifts create interconnected risks. Traditional testing often misses how attackers chain them together.
A red team engagement helps leaders answer critical questions:
- How would an experienced attacker approach our environment?
- Are our detection and response controls aligned with real threats?
- Are internal teams able to recognise subtle but harmful activity?
- Does our organisation respond quickly when incidents unfold?
The answers offer clarity. They help leaders prioritise security investments and refine incident response processes.
Key phases of a modern red team engagement
This guide stays away from over-technical walkthroughs. Instead, it focuses on the strategic elements that matter to decision-makers.
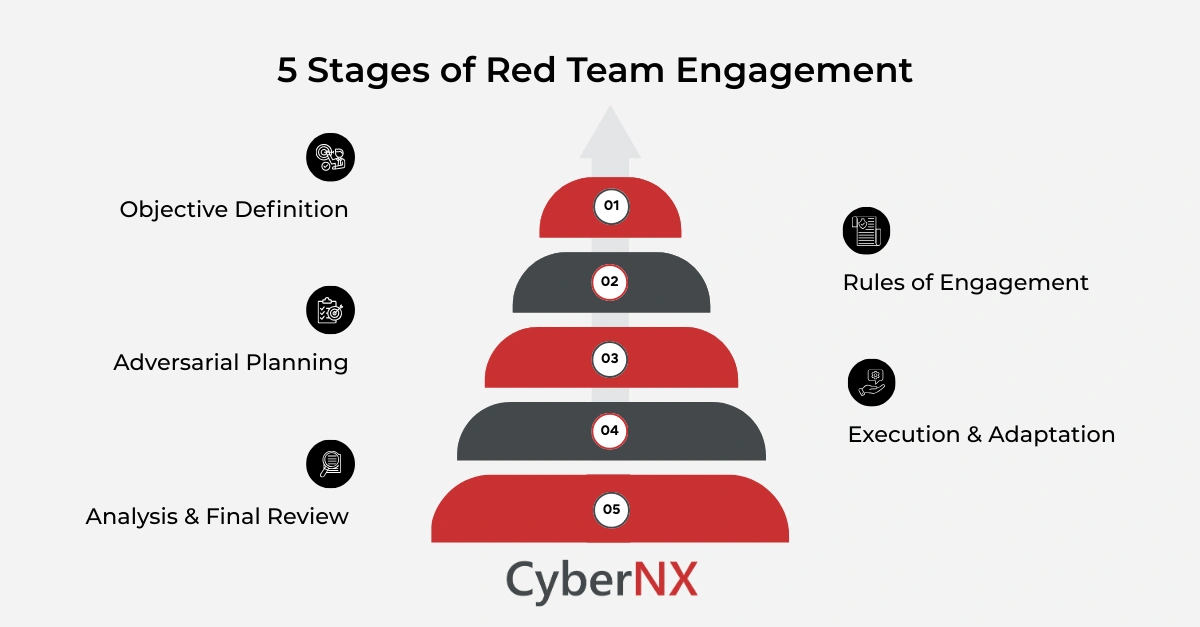
1. Objective definition
Leadership defines a scenario. It may involve protecting a system, a process or a high-value asset. The clearer the objective, the more focused and meaningful the engagement.
2. Rules of engagement
The team sets boundaries. These rules define access restrictions, acceptable techniques and communication channels. Clear boundaries keep the exercise safe while maintaining realism.
3. Adversarial planning
The red team studies the organisation’s systems, behaviours and likely weaknesses. Planning includes social routes, digital routes and hybrid pathways. This planning phase often shapes the outcome more than the technical execution.
4. Execution and adaptation
Attackers rarely follow one path. They observe, adjust and pivot. A good red team takes the same approach. They evaluate opportunities, test multiple paths and advance towards the set objective.
5. Analysis and final review
After the engagement, findings move beyond “what happened”. They cover why certain gaps existed, how they linked together and how the organisation responded.
What should a red team report include
A high-impact report combines clarity and depth. It helps leadership understand what happened and why. It also helps engineering teams strengthen controls.
A complete report often includes:
- Clear narrative: The report tells the complete story. It explains how the red team approached the objective, which paths worked and why defenders struggled to see the activity.
- Impact assessment: This highlights the real business effect. Leaders gain clarity on potential data loss, service disruption or operational risk.
- Detection timeline: This section helps blue teams understand when defenders noticed activity and where blind spots existed.
- Actionable remediation: Guidance focuses on achievable steps. These actions help teams strengthen identity controls, monitoring capabilities and internal processes.
- Optional retest summary: If a follow-up assessment is performed, the report includes how the improved defences responded.
Red team engagement example scenarios
Here are some realistic ways organisations use red teaming. These red team scenarios avoid the typical technical narrative and instead focus on strategic goals.
- Attempting to gain access to confidential financial data
- Testing whether an attacker could use employee accounts to move deeper into systems
- Studying how quickly the SOC reacts to subtle privilege escalation
- Evaluating how well internal teams handle an unexpected incident notification
- Understanding whether cloud misconfigurations allow lateral movement
Each red team engagement example shows how objectives guide the entire exercise.
Why the defensive response matters as much as the attack path
Security leaders often focus on the technical side. Yet the defensive response is equally important. Red teaming tests more than technology.
It also tests:
- communication between teams
- clarity of escalation pathways
- maturity of monitoring systems
- confidence of responders during an incident
- timeline from detection to containment
These observations often deliver the strongest improvements.
Signals of a successful red team engagement
Success is not measured by whether the red team reaches the objective. It is measured by the clarity the organisation gains.
A strong engagement gives leaders:
- clear insight into how attackers think
- practical recommendations tied to business priorities
- a realistic understanding of response gaps
- early warnings about risky pathways or weak processes
- an opportunity to refine defence strategies
These insights shape long-term resilience.
When organisations benefit most from red team engagements
Red teaming helps leaders during key moments:
- before major product launches
- after cloud expansion
- when teams adopt new identity models
- while preparing for regulatory reviews
- after mergers or acquisitions
- when boards ask for assurance on cyber readiness
These points often create new attack paths. Red teaming helps highlight them quickly.
Conclusion
A red team engagement gives organisations a clear view of how an attacker might behave inside their environment. It blends strategy, creativity and real adversarial thinking. Leaders use it to understand gaps, strengthen processes and validate response capabilities.
CyberNX supports organisations with structured, goal-oriented red team engagements that align with business needs. Each engagement focuses on clarity, realistic scenarios and practical outcomes. Speak with our experts to know more about our red teaming services and plan your next engagement and strengthen your security readiness.
Red Team Engagement FAQs
How does a red team engagement help leadership teams make better decisions?
It gives leaders visibility into real attack paths, defensive blind spots and response timelines. These insights help allocate budgets, evaluate control maturity and shape long-term security planning. The engagement turns abstract risks into clear, measurable outcomes leadership can act on.
Is a red team engagement disruptive to operations?
The engagement is designed to run quietly. The rules of engagement ensure safety, stability and minimal impact on production systems. Internal teams often do not know the engagement is happening, but the testing avoids techniques that could harm business operations.
Can a red team engagement work in cloud-only environments?
Yes. Modern red teaming includes cloud identity structures, API behaviour, privilege routes, exposed services and configuration drift. Cloud environments add complexity, and adversarial testing helps organisations understand how attackers could navigate these systems.
How long does a typical red team engagement last?
The timeline depends on scope and objectives. Many engagements run from two to six weeks. Broader scenarios may extend longer. The duration ensures realistic planning, execution and analysis without rushing critical findings.