Security teams want better visibility, any day. Attackers move fast, controls shift and gaps appear between tools, teams and processes. Many organisations run red team or blue team exercises. But they still struggle to convert insights into improvement. This is where purple team engagement helps. It brings offensive and defensive teams together and creates shared understanding and faster learning. In addition, it helps teams discover blind spots without waiting for an incident.
At CyberNX, we see purple teaming as a practical step toward stronger resilience. It is structured, collaborative and supports continuous improvement. In this blog, find out how you can turn defence into an advantage with purple team engagement.
What is purple team engagement?
Purple teaming is the methodology that combines offensive and defensive cybersecurity efforts. A purple team engagement could be described as the simulation applying the said methodology for a specific project. It is a collaborative security exercise where red team experts test systems through controlled attacks.
Blue team members defend, detect and respond. Both groups work together. They share insights in real time. The goal is not to score points. It is to improve defences.
This approach blends the creativity of red teams with the operational depth of blue teams. It helps organisations strengthen detection, response and prevention in one structured cycle.
What purple team engagement means in cybersecurity
In cybersecurity, purple teaming focuses on:
- Testing real attack paths
- Strengthening detection rules
- Improving SOC playbooks
- Reducing response time
- Closing visibility gaps
It is a learning-driven exercise. Each scenario builds clarity about how attackers behave and how defenders respond.
Closing the loop: why purple teaming is the security force multiplier
Security tools generate alerts. Red teams find weaknesses. Blue teams chase incidents. But teams often operate in silos. Purple teaming changes this. It removes barriers. It brings people together to review attacks, share context and improve defence.
- Clear alignment between attack and defence: Red teams show how attackers move. Blue teams highlight what they can see. Both groups understand the gap between expected and actual detection.
- Stronger SOC maturity: Purple teaming helps SOC teams tune rules. It helps them improve visibility, refine queries and strengthen response workflows.
- Practical learning: Teams learn from live, realistic scenarios. They improve step by step. No guesswork, no assumptions.
- Faster improvements: Every test leads to immediate feedback. This accelerates remediation and detection enhancements.
MITRE ATT&CK Evaluations Insights, 2024 said the following about purple teaming: Collaboration between red and blue teams accelerates security maturity by revealing detection blind spots quickly. This is why we rely heavily on ATT&CK mapping during purple team exercises. It gives structure. It gives clarity.
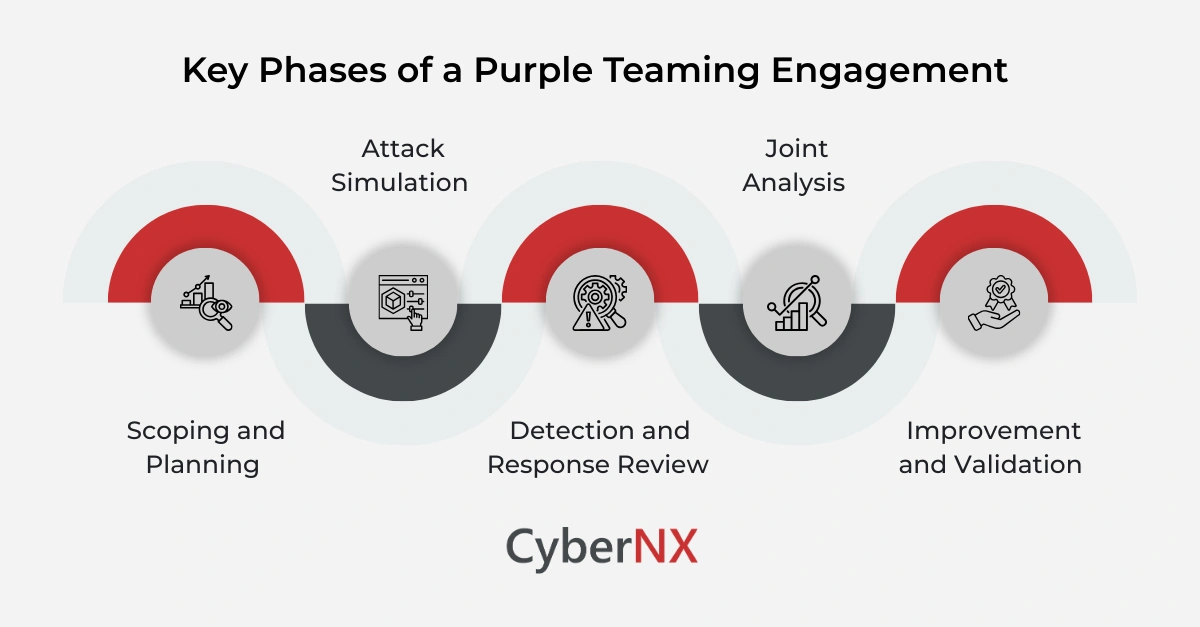
Unlocking key phases of purple teaming engagement
Most teams look for a simple structure. We keep the flow clear and easy to follow.
1. Scoping and planning
We align on goals, understand your critical assets, and then go on to select attack scenarios that matter to your business.
2. Attack simulation
Red team members run controlled attacks. These include:
- Privilege escalation
- Lateral movement
- Credential theft
- Web or API exploitation
- Data exfiltration attempts
Each simulation is mapped to MITRE ATT&CK for clarity.
3. Detection and response review
Blue teams track alerts, logs and events. They check detection gaps. They verify how quickly they can respond.
4. Joint analysis
Both teams sit together. They break down:
- What worked
- What failed
- What went unnoticed
- What needs improvement
This is the heart of purple teaming.
5. Improvement and validation
Based on findings, teams tune controls.
This includes SOC rules, firewall policies, endpoint configurations and response playbooks. A follow-up test validates improvements.
Purple team engagement example
A financial services company wants to conduct a SOC maturity assessment.
They choose three attack scenarios:
- Stolen credentials used on VPN
- Lateral movement to internal databases
- Data extraction using encrypted channels
During the engagement:
- The red team triggers credential misuse attempts.
- The SOC tracks user behaviour analytics and EDR alerts.
- The teams discover missing detection for lateral movement.
- Together, they tune rules and improve log correlation.
- A second test confirms the new detection works.
This cycle creates real improvement in a short time.
Advantages: how purple teaming drives defence posture
Purple teaming supports long-term defence. It builds maturity faster than isolated exercises.
- Stronger visibility: Teams learn where gaps exist in SIEM, EDR or network logs.
- Faster detection: SOC teams refine rules and queries with real attack data.
- Better collaboration: Security becomes a shared responsibility rather than isolated tasks.
- Improved resilience: The organisation becomes better prepared for actual attacks. One improvement at a time.
Actionable Steps for Executing High-Impact Purple Team Engagement
Teams often ask how to run this exercise effectively.
- Start with business priorities: Focus on high-value assets and realistic threats.
- Keep communication open: Red and blue teams must share insights frequently.
- Use MITRE ATT&CK: It provides structure and traceability.
- Document each scenario: Clarity helps SOC teams strengthen rules later.
- Validate improvements: Always retest. Small changes create measurable progress.
How CyberNX supports purple team engagement
We work as partners, guide teams step by step and design practical, easy-to-understand exercises.
Our approach includes:
- Realistic attack scenarios
- SOC-focused improvements
- Clear documentation
- ATT&CK-based mapping
- Post-engagement support
Our experience shows that collaboration builds stronger defence than isolated testing.
Conclusion
A purple team engagement creates shared learning. It brings clarity to detection and response. It helps red and blue teams work as one. And it supports long-term resilience through continuous improvement.
If you want a structured, collaborative approach to strengthening your SOC, we are ready to assist your security team. Book a consultation with us to know more about our purple teaming services and how our team can enhance your security maturity with a tailored purple team engagement.
Purple team engagement FAQs
How long does a purple team engagement usually take?
Most engagements take one to four weeks depending on the number of scenarios and complexity of your environment. Smaller exercises move faster. Larger enterprises with multiple systems require more detailed planning and review cycles.
Is a purple team engagement like a red team assessment?
No. A red team assessment is adversarial. The red team works independently. A purple team engagement is collaborative. Both offensive and defensive teams coordinate in real time. The focus is improvement, not stealth.
Can a purple team engagement help improve SOC detection rules?
Yes. This is one of the biggest advantages. Real attack data helps SOC teams build better signatures, alerts and behavioural detections. It also highlights missing logs and weak correlation patterns.
What skills are needed for a purple team engagement?
Red teams need offensive testing expertise. Blue teams need detection, monitoring and incident response capabilities. Both groups must be open to collaboration. Good communication makes the engagement effective.