Lots of companies perform security tests every year. These tests include pentests, vulnerability scans etc. But attackers still manage to find a way in. That is because regular testing methods often separate offensive techniques from defensive validation. In the real world, both sides evolve at the same time.
A purple team assessment bridges this gap. It merges offensive and defensive thinking into one coordinated exercise. It doesn’t just look for weaknesses. It also checks whether your team can spot, respond to and stop real attacks as they happen.
In this guide, we’ll take you behind the scenes of a purple team assessment and show you how real techniques are tested, improved, and validated to build long-term resilience.
What is a purple team assessment?
A purple team assessment is a collaborative activity in which offensive (red team) and defensive (blue team) experts work together to test and improve the security of an organisation.
As part of this assessment, teams look at how well:
- Attacks are carried out and simulated
- Defences find and stop those attacks
- Teams, tools, and processes work together
- Detection rules and alerts work
- Gaps lead to actionable improvements
Purple teaming has always been about attack simulations that expose real gaps across the entire digital ecosystem. However, it is not limited. With purple team assessment, it is a structured learning process for security teams.
Why companies use purple team assessments
More security leaders now like purple teaming because it gets results faster than red or blue exercises done alone.
Here’s why it matters:
- It checks real-world attack paths from start to finish.
- It improves the detection rules and alert tuning.
- It strengthens incident response readiness.
- It brings security teams together around shared goals.
- It quickly shows useful, high-impact changes.
Purple teaming turns testing into a continuous improvement cycle.
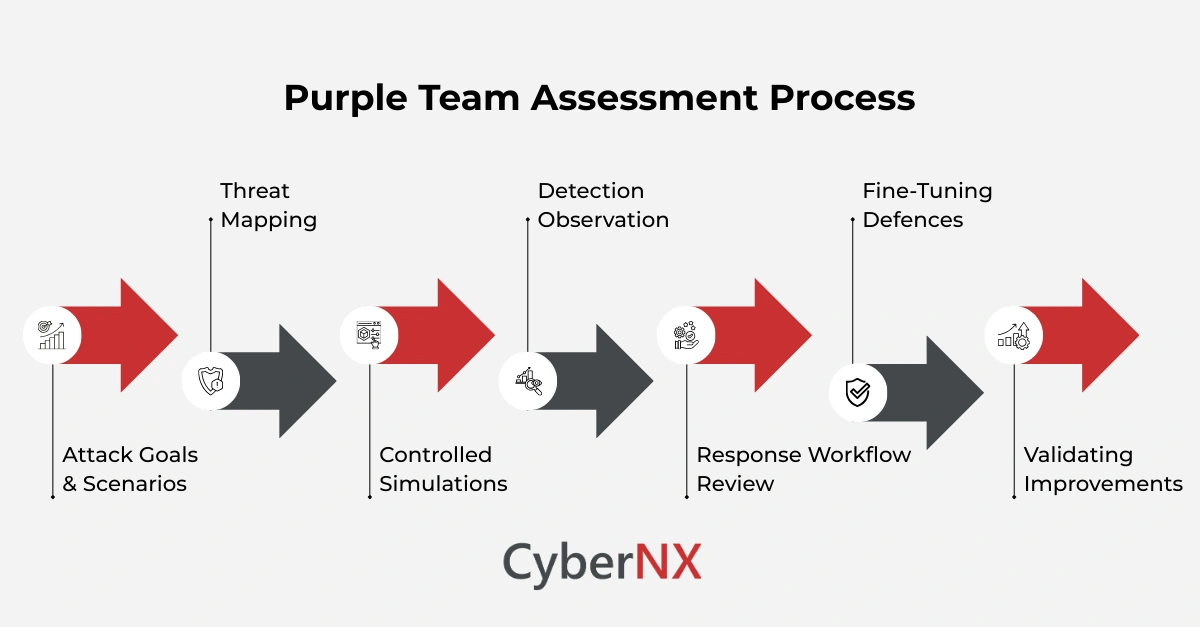
How a purple team assessment works behind the scenes
A purple team assessment is much more organised than a simple attack simulation. This is what really happens during the process.
1. Attack goals & scenarios
Setting goals is the first step in the assessment. These goals help the exercise stay on track with real risks.
Some common scenarios are:
- credential theft or misuse
- attempts to steal data
- lateral movement methods
- privilege escalation
- taking advantage of cloud misconfigurations
- malware behaviour or endpoint compromise
Clear goals make sure that both teams are working towards measurable results.
2. Threat mapping
Next, we make sure that the simulated attacks fit with the organization’s structure. This makes sure it’s real and useful.
We look at:
- current controls and monitoring tools
- the network structure
- cloud platform configurations
- AD/identity structures
- logging coverage
This map creates the prototype for the whole assessment.
3. Controlled simulations
Red team experts act like real attackers. These actions are carried out carefully to avoid causing problems while still showing real threats.
Some examples are:
- phishing attempts and payload drops
- taking advantage of IAM policies that may be misconfigured
- taking advantage of unpatched systems
- creating persistence mechanisms
- using legitimate tools to get more access
- moving laterally across networks without being spotted
These methods copy the behaviour of ransomware groups and APT actors.
4. Detection observation
As attacks unfold, we analyse how well defensive systems react.
We look at:
- whether logs capture events
- which alerts fire (or fail to fire)
- noise-to-signal ratio
- SIEM correlation accuracy
- endpoint detection capabilities
- real-time response patterns
This reveals blind spots that attackers could exploit silently.
5. Response workflow review
Once detection occurs, focus shifts to response quality. We evaluate the blue team’s ability to handle incidents under pressure.
Key factors include:
- triage accuracy
- escalation speed
- communication clarity
- containment decisions
- investigative depth
- ticketing and documentation
This step highlights the practicality of incident response plans.
6. Fine-tuning defences
One of the best things about purple teaming is immediate improvement. As issues occur, they are fixed on the spot.
Usually, improvements include:
- updating the rules for SIEM correlation
- reducing false positives
- adjusting EDR policies
- improving log collection
- making access controls stronger
- fixing weak points in the architecture
This speeds up maturity much faster than regular red team exercises.
7. Validating improvements
To confirm progress, attacks are reattempted under the updated security posture.
This helps verify:
- detection accuracy
- alert clarity
- response effectiveness
- containment quality
- system resilience
The loop continues until the organisation reaches the desired maturity level. In this quest, security teams use a wide range of purple team tools to achieve the desired objectives in each of the phases.
Common weaknesses uncovered during purple team assessments
We see the same patterns in many fields. Recognising these helps teams prepare better.
The most common weaknesses are:
- missing telemetry or incomplete logging
- ineffective alert rules
- slow to respond to early signs
- misconfigured cloud controls
- too much reliance on automation
- alert fatigue and noise overload
- poor coordination between security and IT teams
- weak lateral movement detection
Purple teaming exposes these weaknesses in real-world conditions.
Conclusion
A strong approach to purple team assessment helps organisations uncover real attack paths, improve detection accuracy and strengthen response workflows. Testing becomes collaborative. Defences become sharper. And teams gain more confidence in their ability to withstand the modern and fast-improving threats.
We work closely with organisations to design structured purple team assessments that align with your architecture and security maturity. Our goal is simple. We want to help teams move from reactive defence to proactive, intelligence-driven resilience. If you want help with building resilient security structure and improving the core of your defences, contact us and know more about our purple team services.
Purple team assessment FAQs
How often should organisations conduct a purple team assessment?
Most organisations benefit from annual or bi-annual assessments, with smaller simulations performed quarterly. High-growth or high-risk environments may require quarterly micro-simulations to keep controls aligned with new attack techniques.
Does a purple team assessment replace red and blue team exercises?
A Purple Team Assessment does not replace red or blue exercises. Instead, it improves both by combining their strengths and improving collaboration. Red teams test attack paths while blue teams refine detection and response based on immediate feedback.
Who should participate in a purple team assessment?
Security analysts, incident responders, SOC teams, threat hunters, IT operations and cloud/platform teams. Cloud and platform teams also play a key role as modern attack paths frequently target misconfigurations or identity weaknesses. Involving cross-functional teams gives full visibility and more realistic mitigation methods.
Is a purple team assessment disruptive to operations?
When conducted correctly, the exercises are controlled, safe and designed to avoid any business disruption. Exercises are executed with clear scoping and close coordination between teams to ensure no production systems are affected. The goal is to simulate real-world threats without interrupting business continuity.