Like the right prescription after medical diagnosis is indispensable, so is a strong penetration testing reporting generation after conducting a penetration test.
The testing process uncovers vulnerabilities, but if the findings are not clear, prioritised and actionable, security improvements will stall.
For business leaders like CEOs, CTOs and founders – understanding the structure and impact of a penetration testing report is absolutely necessary. Because it is a roadmap for risk reduction and a document that wins customer confidence. Plus, it helps in avoiding compliance-related penalties.
What is Penetration Testing Report?
A pentesting report, simply put, is a summary document. It details everything about the simulated cyberattack performed by ethical hackers on your digital infrastructure.
The types of details include findings(vulnerabilities), context of findings, risk score, evidence and recommendations. In short, the report reveals how healthy the security posture of your organisation is.
Types of Penetration Testing Reports
Penetration testing reports come in various formats. From high-level executive summaries to detailed technical analyses. Each type highlights vulnerabilities, risk levels and actionable recommendations for different audiences.
1. Internal Penetration Testing Report
This report is focused on risks from within your organization such as rogue employees, compromised devices and lateral movement after a breach.
Key characteristics:
- Tests from the perspective of someone with internal access.
- Simulates insider threats or attackers who breach external defences
- Explores privilege escalation, access control issues and segmentation flaws
2. External Penetration Testing Report
This report exposes threats coming from outside your network, which are typically from the internet.
Key characteristics:
- Focuses on public-facing assets: web apps, APIs, VPNs and cloud environments.
- Identifies entry points a real-world attacker might use to gain access.
- Often the first line of assessment for regulatory or customer-driven audits.
Organisations benefit from both report types. External testing checks your perimeter while internal testing assesses the damage if that perimeter fails.
Importance & Purpose of the Pen Test Report
Penetration testing report in cybersecurity engagements is crucial. Because it converts abstract threats into concrete, prioritised risks. The leadership, board and engineers can understand and act upon. For business leaders, it is often the only tangible output from an otherwise complex, technical process.
Here, we throw more light on the benefits of penetration testing report:
1. Risk Communication Across Stakeholders
Showing binary scan results to the business board does not work. At the same time, a pen testing report, written in clear business terms, helps bridge that gap.
For example, instead of saying “TLS 1.0 detected,” the report might say: “Outdated encryption protocol may allow attackers to decrypt sensitive customer data, violating GDPR requirements.”
2. Alignment of Priorities
The report enables cross-functional teams like security, product and infrastructure to align around a shared roadmap for security fixes. Rather than chasing theoretical issues, the team can focus on real, proven attack paths.
3. Operational & Strategic Benchmarking
With recurring pen tests (quarterly or annually), you can track whether your security posture is improving. Are vulnerabilities repeating? Is time-to-remediation improving? Are new features introducing new risks?
4. Regulatory Readiness & Legal Defence
In the event of a breach, a documented penetration testing report shows that your company took reasonable steps to secure systems, potentially reducing legal liability or regulatory penalties.
Consider this example: If your SaaS platform is undergoing ISO 27001 certification, a penetration report may be the deciding document that helps auditors assess whether you meet Annex A controls related to vulnerability management.
Or if your enterprise customer demands security assurance before signing a contract, the pen test report becomes the “proof” that your product is secure by design.
As you can see, a pen test report empowers your business to make smarter, faster and informed decisions about where to focus, where to invest and how to stay secure.
Benefits of a Penetration Testing Report
The real value of running the test comes to the fore after what you do with the testing report. Some of the benefits our experts have noted include:
- Reduces risks proactively by fixing gaps before attackers find them
- Demonstrates due diligence to customers, regulators and partners
- Elevates internal alignment between engineering, security and leadership.
- Benchmarks security maturity over time by comparing periodic reports.
For founders, such as report strengthens investor confidence. For CTOs, it sharpens your roadmap. And for CEOs, it turns a black-box technical exercise into a tangible business decision.
Key Components of the Report
Here’s a deeper look at what should be included in the report:
1. Executive Summary
The report should summarize the test objectives, major findings and strategic recommendations in clear, concise and context-aware language.
Look at this example:
“The test identified four critical vulnerabilities across customer-facing applications, including unauthenticated access to internal APIs. These findings pose a high risk to customer data confidentiality. Remediation is recommended within 14 days.”
No acronyms, no technical jargon. But a clear statement of business risk.
2. Scope and Methodology
It details the systems tested (e.g., production web app, internal network, cloud workloads), the test type (black-box, white-box) and Penetration testing methodologies used (e.g., OWASP, NIST, MITRE ATT&CK).
This assures that the test was methodical, structured and relevant to the organization’s real-world threat landscape. It also helps validate compliance requirements.
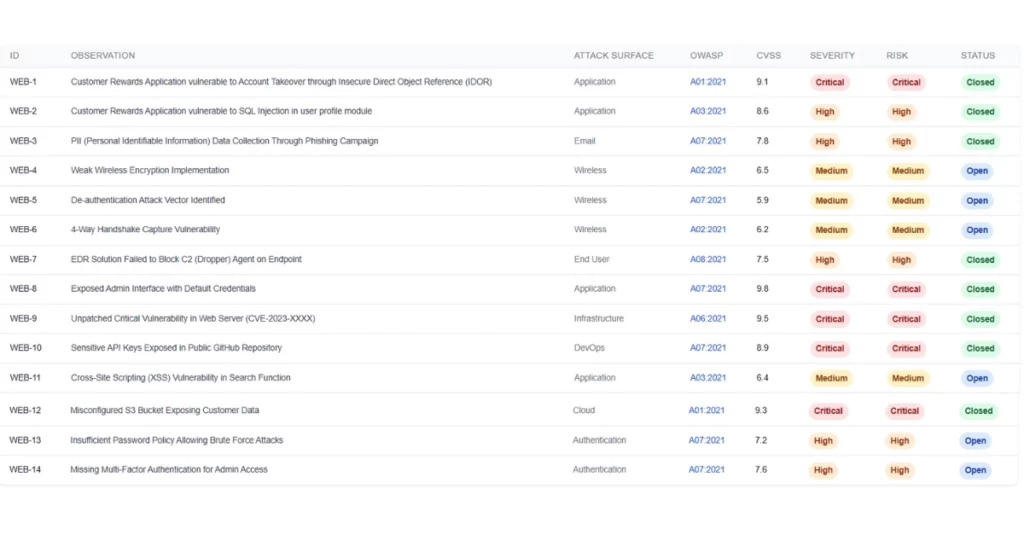
3. Findings with Risk Ratings
Each vulnerability should be fully described and ranked using a consistent risk scoring system (CVSS, likelihood vs. impact, etc.).
Each finding typically includes:
- Title (e.g., “SQL Injection on Login Form”)
- Description (what it is and how it was found)
- Affected Asset or Endpoint
- Risk Rating (e.g., Critical, High, Medium)
- Technical Impact (e.g., database access, remote code execution)
- Proof of Exploit (e.g., screenshot, request logs, payloads)
4. Business Impact
This is where technical details are translated into tangible consequences. The report should explain what a successful exploitation would mean for the organization.
Examples:
- Loss of customer data may result in GDPR penalties and reputational damage.
- Denial-of-service vulnerability in the API could lead to service outages affecting SLAs.
This section helps decision-makers understand urgency and allocate resources accordingly.
5. Remediation Guidance
Each issue should be detailed and include actionable fixes. This could be code-level recommendations, firewall rules, configuration changes or compensating controls.
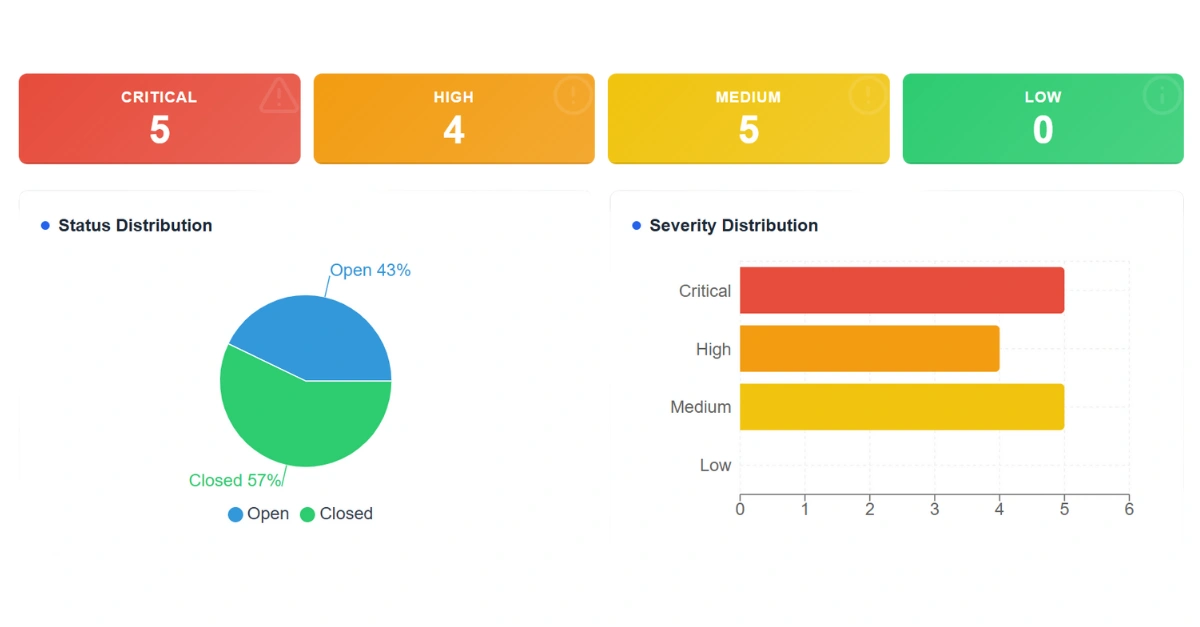
6. Risk Summary Matrix
A heatmap or tabular overview showing how vulnerabilities are distributed by severity helps. Stakeholders could glance over it and gain insights.
Example:
7. Appendix
Include supporting information such as:
- Tools used
- Raw output logs
- Attack chains or kill chains
- CVSS score calculation methodology
This helps technical teams reproduce the findings and understand how they were derived
Tips to Create an Effective Pen Test Report
When you review a vendor’s sample penetration testing report, keep these best practices in mind:
1. Insist on Clarity, Not Jargon
The report should speak two languages: technical precision for engineers, business impact for executives. Avoid buried insights in security-speak.
2. Demand Context, Not Just Lists
A list of CVEs is not a report. It is a scan result. The best reports provide context: where the vulnerability exists, why it matters and how an attacker could use it.
3. Prioritize Risks, Not Volume
It’s tempting to show lots of findings. But too many low-severity alerts should not overshadow one critical issue. The report should make this distinction.
4. Include Visuals
Architecture diagrams, attack paths and screenshots of successful exploitation help convey risk far better than text alone.
5. Make Remediation Actionable
Avoid generic advice like “use secure coding practices.” Look for specific, reproducible, step-by-step fixes.
6. Include a Remediation Timeline
Good reports help prioritize fixes over weeks or months based on severity. This is especially useful for planning engineering sprints.
7. Keep It Confidential but Shareable
The report should be formatted to be shared, internally or with third parties, but it should also be labelled clearly with confidentiality notices to avoid misuse.
Compliance Standards for Pen Test Reports
Depending on the industry, penetration testing report is structured using different frameworks. Here’s a brief look at the major standards:
- PCI DSS: Requires regular pentesting for systems that handle cardholder data. Reports must include test scope, methodologies and risk ratings.
- SOC 2: Emphasizes risk management. A pen test report serves as evidence of control effectiveness.
- ISO 27001: Penetration testing supports several control objectives under Annex A.
- HIPAA: While it does not mandate pen testing, it encourages regular testing of technical safeguards.
The pentest report should align with auditors’ expectations.
What Will You Get with CyberNX?
At CyberNX, our experience over the years has shown us that a good, impactful, detailed and transparent pentesting report is the key. Clients expect it and we provide exactly that.
Our pentesting experts create customized reports like “Executive Summary” or “Standard report” with all the details. Plus, we make sure all our findings and recommendations align with the specific business context.
1. Executive Summary
A concise, high-level overview of the penetration testing engagement—covering scope, methodology, key findings, and strategic takeaways for stakeholders.
2. Technical Findings
Comprehensive documentation of discovered vulnerabilities, categorized by severity, impact, and supported with technical evidence and proof-of-concept details.
3. Remediation Plan
A prioritized, actionable roadmap with expert remediation steps to address identified risks effectively and reduce exposure.
4. Risk Matrix
Visual mapping of vulnerabilities based on business impact, likelihood of exploitation, remediation complexity, and overall risk prioritization.
Besides, our deliverables also include Knowledge Transfer, Remediation Support and Compliance Mapping.
Conclusion
Penetration testing report is a strategic document that highlights how well your business is protected and where you need to invest next.
To customers, it shows you take security seriously. To engineers, it provides clear direction. To regulators, it proves you are doing your homework.
If you are looking for penetration testing services, get in touch with our experts!
Penetration Testing Report FAQs
Can a penetration testing report be shared with clients or investors?
Yes, and in many cases, it’s a smart move. Sharing a sanitized or executive-level summary of your penetration testing report can build trust, especially with enterprise clients or investors who want assurance that security is taken seriously. Just ensure you strip out technical specifics that could expose your systems. For deeper disclosures, always use an NDA and consider including only high-level risks, resolved issues, and next steps.
Can penetration testing reports be used in board-level risk discussions?
Absolutely. For many boards, cybersecurity risk is now a core governance concern. A well-structured penetration test report—particularly the executive summary and risk matrix – can help leadership understand how security impacts operations, finances, and brand reputation. It supports informed decision-making during budget planning, technology investment, and compliance reviews.
What should I do if the report reveals critical vulnerabilities right before a product launch?
Pause the launch and prioritize fixes. Releasing a product with known critical vulnerabilities and ignoring the steps of a penetration test puts customer data, system uptime, and trust at risk. It’s better to delay a release than face regulatory issues, breaches, or reputational fallout. If you must proceed, consider disabling the affected features or adding temporary compensating controls—then communicate transparently with stakeholders.
What is a sample penetration testing report?
A sample penetration testing report is a redacted example that illustrates typical sections – like methodology, key findings, risk ratings, and remediation advice. It’s useful for understanding format and expectations when preparing for your own test. However, no two systems or threat landscapes are alike, so use samples as guidance – not a substitute for a tailored, expert-led assessment.