Should we choose MDR or MXDR? That’s a question we often hear from security leaders. On the surface, both promise round the clock threat detection and response. Yet the difference between MDR vs. MXDR becomes clear only when you first understand EDR and XDR in detail.
We see many teams rush this decision. The result is mismatched tools, rising alerts, and limited visibility. MDR and MXDR are not competing buzzwords. They are managed services built on different foundations. One focuses on endpoints. The other connects signals across the environment.
In this blog, we break it all down. We explain EDR, MDR, XDR, and MXDR in simple terms. We then compare MDR and MXDR side by side. By the end, you will know which approach fits your security maturity, budget, and risk profile.
Why understanding EDR and XDR comes first
Before comparing MDR and MXDR, we need clarity on what they manage. MDR is essentially a managed service wrapped around EDR. MXDR is a managed service built on XDR. Without understanding EDR and XDR, the comparison stays shallow.
What is EDR?
Endpoint Detection and Response focuses on devices. Laptops, servers, and workloads. EDR tools monitor endpoint activity to detect suspicious behaviour. They record events, analyse processes, and allow response actions like isolating a device.
EDR answers questions such as:
- Which process started the attack?
- What file was executed?
- Which endpoint is compromised?
EDR is powerful. Yet it has a limit. It sees what happens on endpoints only. If an attack moves through email, cloud apps, or identity systems, EDR sees fragments. Not the full story.
What is XDR?
Extended Detection and Response expands visibility beyond endpoints. XDR brings together data from endpoints, network, email, cloud workloads, and identity systems. It correlates signals across these layers.
XDR answers broader questions:
- How did the attacker enter?
- Which systems were touched next?
- What is the attack path across the environment?
XDR reduces blind spots. It also reduces alert noise by correlating events. Instead of ten isolated alerts, you get one incident with context.
What is MDR?
Managed Detection and Response is the managed service version of EDR. In simple terms, MDR means experts monitor, investigate, and respond to threats detected by your EDR platform.
With MDR, you are not just buying a tool. You are buying a security operations capability.
How MDR works in practice
MDR providers deploy or integrate with an EDR solution. Their analysts then:
- Monitor endpoint alerts 24 by 7
- Investigate suspicious activity
- Confirm real threats
- Take response actions based on agreed playbooks
MDR is well suited for teams that:
- Lack an internal SOC
- Struggle with alert fatigue
- Want faster endpoint threat response
However, MDR still lives largely at the endpoint layer. If your biggest risks lie in cloud sprawl, identity misuse, or email attacks, MDR may feel limited.
What is MXDR?
Managed Extended Detection and Response is the managed service version of XDR. MXDR goes beyond endpoints and covers the wider attack surface.
MXDR providers manage detection and response across:
- Endpoints
- Networks
- Email systems
- Cloud platforms
- Identity and access tools
The goal is unified detection with expert-led response across the entire environment.
How MXDR changes security operations
MXDR analysts work with correlated data from multiple sources. This allows them to:
- Detect attacks earlier in the kill chain
- Understand lateral movement
- Respond with precision across systems
For example, an MXDR service can link a phishing email, stolen credentials, and endpoint malware into one incident. Response actions then span email, identity, and endpoint controls.
MXDR fits organisations that:
- Run hybrid or cloud-first environments
- Face advanced or targeted attacks
- Want strategic visibility, not just alerts
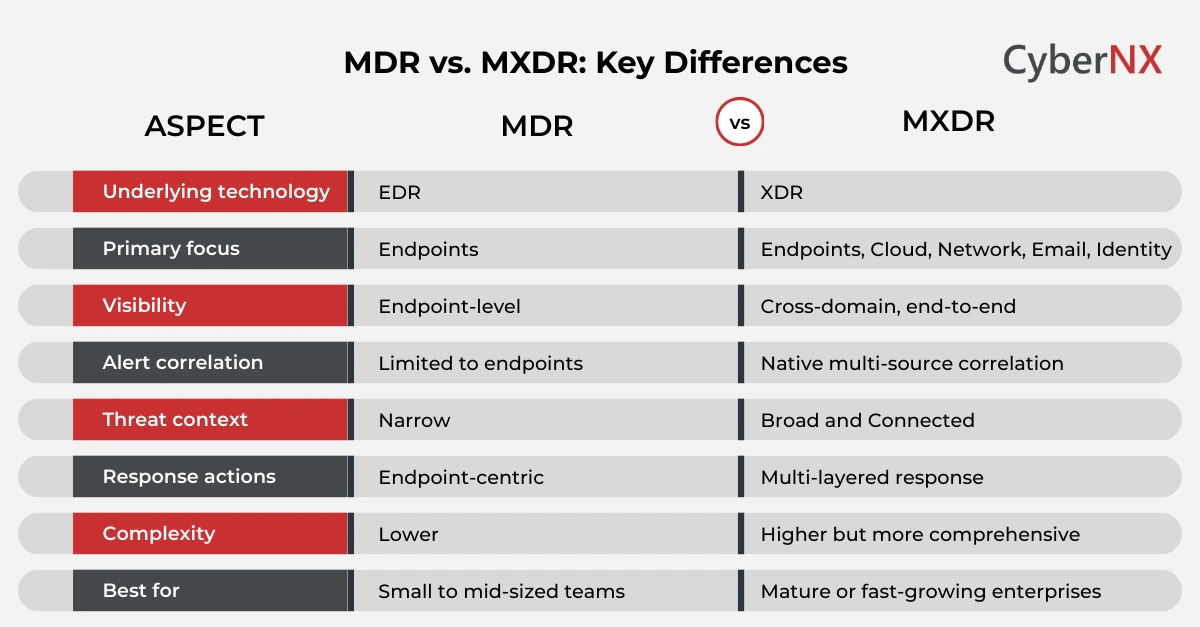
MDR and MXDR: The core difference
At its heart, MDR and MXDR differ in scope. Both reduce operational burden. Both bring expert oversight. The difference lies in how much of your environment they see and protect.
Choosing between MDR vs. MXDR
There is no universal answer. The right choice depends on your environment and goals.
When MDR makes sense
MDR works well if:
- Endpoints are your primary risk
- You need fast, reliable detection
- You want a simpler managed service
For many organisations, MDR is a strong first step. It stabilises security operations and buys time.
When MXDR is the better fit
MXDR is the better option if:
- You operate across cloud and on-prem systems
- Identity attacks and email threats are rising
- You need strategic visibility for leadership decisions
MXDR supports long-term security maturity. It aligns better with complex enterprise environments.
Common misconceptions we see
Many leaders assume MXDR is just MDR with more marketing. Our experience shows otherwise. The architectural difference between EDR and XDR directly impacts detection quality and response speed. Another misconception is cost. MXDR often appears more expensive. Yet when you factor in tool sprawl, internal staffing, and missed incidents, MXDR can reduce total security spend.
How we approach MDR and MXDR
We work alongside your team to assess risk, not just tools. Our approach starts with understanding your environment, attack surface, and business priorities. For some clients, MDR delivers exactly what they need. For others, MXDR unlocks visibility they never had before. We help you choose with clarity, not pressure.
Conclusion
Understanding MDR and MXDR starts with understanding EDR and XDR. MDR is the managed evolution of endpoint security. MXDR is the managed evolution of unified detection across the enterprise. Both have value. The right choice depends on how much of your environment you want protected, and how quickly you need context to act.
If you want help evaluating MDR or MXDR for your organisation, speak with our experts today. We will guide you with practical insight and clear next steps. We also provide MDR and XDR services, aimed at boosting your entire digital ecosystem security.
MDR vs. MXDR FAQs
Can MDR and MXDR coexist in the same organisation?
Yes, they can. Some organisations use MDR to secure endpoints while adopting MXDR for broader visibility across cloud, email, and identity. This approach often appears during transitional phases of security maturity.
Does MXDR replace a SOC completely?
MXDR can replace parts of a traditional SOC, especially monitoring and first-level response. However, many organisations use MXDR as a force multiplier, allowing internal teams to focus on strategy, risk, and governance.
Is XDR required before moving to MXDR?
Yes. MXDR is built on XDR technology. Without XDR’s ability to correlate signals across multiple security layers, MXDR cannot deliver unified detection or coordinated response.
How long does it take to deploy MDR or MXDR?
MDR deployments are typically quicker since they focus on endpoints. MXDR takes longer due to multiple integrations, but the added visibility and context usually justify the effort.