Uncover Hidden Cyber Threats in Your Digital Environment
Advanced Cyber Threat Hunting Services
Identify potential risks, lateral movement patterns, and stealthy attackers to fortify your defenses and protect your most critical assets.
Talk to our Experts Today





















INTRODUCTION
Proactively Detect Cyber Threats with Expert Threat Hunting Services from CyberNX
How prepared is your organization to identify and mitigate advanced cyber threats lurking in your digital environment? CyberNX’s Threat Hunting as a Service goes beyond traditional defenses to proactively seek out hidden vulnerabilities, advanced persistent threats (APTs), and malicious activities within your infrastructure.
We address your key challenges:
Detect vulnerabilities and
alicious activities that routine monitoring or automated systems may overlook.
Test your defenses against sophisticated, real-world attack strategies, ensuring readiness for modern cyber threats.
Gain deep insights into the effectiveness of your current detection and prevention measures.
Strengthen your team’s ability to detect, respond to, and recover from security incidents swiftly.
Pinpoint specific areas to improve your security posture and prevent future breaches.
PROCESS
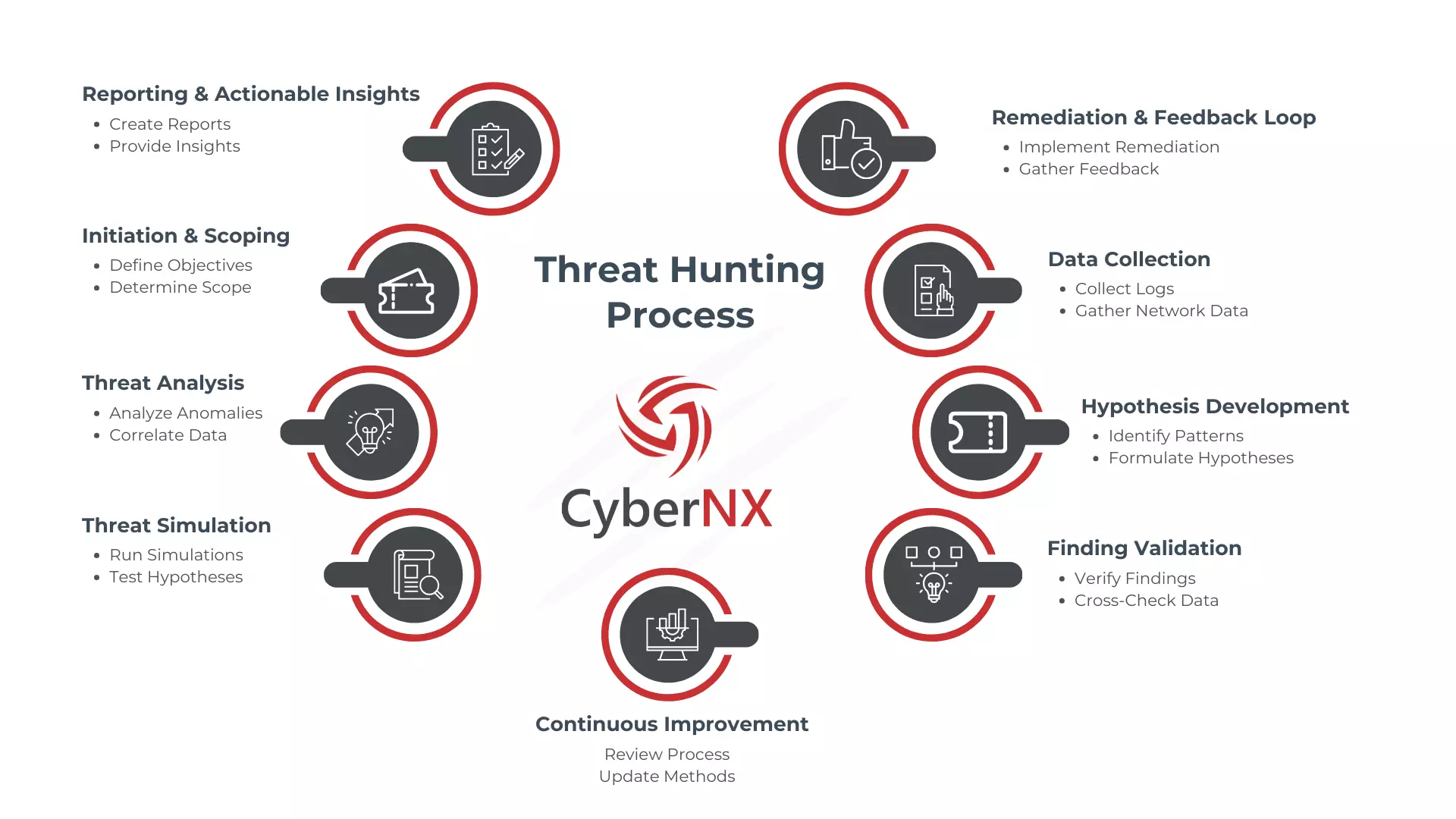
How It Works?
Looking for Threat Hunting Services? Connect with us.
APPROACH
Threat Hunting as a Service: What Sets CyberNX Apart?
Cutting-Edge Processes
Specialized Skills
CERT-IN Empanelled
Risk Mitigation Assistance
Highly Skilled Team
Customer first Approach is our guiding principle.
BENEFITS
Advanced Threat Hunting Services from CyberNX
Evaluate Detection and Response Capabilities
Test your security team’s ability to detect and respond to advanced cyber threats. Our assessments highlight strengths and areas for improvement in handling stealthy attackers.
Comprehensive Risk Assessment
Analyze how attackers could infiltrate your network, exploit vulnerabilities, and compromise critical data. We help you understand potential risks to your digital assets and infrastructure.
Comprehensive Threat Hunting Report
A detailed report that includes all findings, analysis, and step-by-step actions taken during the threat hunt, offering clear visibility into security gaps and areas for improvement.
Fact-Based Threat Analysis
Receive an in-depth analysis of detected threats with actionable insights to mitigate risks, enhance defenses, and prioritize remediation efforts.
Executive Summary
Get a concise report tailored for senior management, outlining critical findings and strategic recommendations to strengthen your cybersecurity framework.
Uncover Complex Threats
Identify advanced persistent threats (APTs), malicious behaviors, and sophisticated attack vectors that evade automated security tools.
For Customized Plans tailored to Your Needs,
Get in Touch Today!
FAQ
Frequently Asked Questions
Threat hunting is a proactive cybersecurity practice that involves actively searching for and identifying potential threats that may have already bypassed existing security controls. Unlike incident response, which reacts to known alerts or incidents, threat hunting starts with a hypothesis or an indication of compromise and involves searching for evidence of malicious activity that may not have triggered any alarms.
Threat hunting offers several benefits, such as reducing attack surfaces, anticipating new attack vectors and improving an organisation’s ability to quickly deploy and integrate existing and new security controls and capabilities. Threat hunting can also improve the security posture of an organisation, helping the organisation stay ahead of emerging threats.
Organisations can choose to conduct threat hunting more frequently based on their specific security needs and risk tolerance or as per any regulatory guidelines. For example, the SEBI CSCRF mandates MIIs and Qualified REs to conduct threat hunting exercises quarterly.
Threat hunters can leverage various security tools and technologies to aid their investigations. For example, Security Information and Event Management (SIEM) systems can help aggregate and analyse security logs from various sources, enabling threat hunters to identify patterns and anomalies that may indicate malicious activity.
Threat intelligence plays a crucial role in threat hunting by providing context and insights into the latest attack techniques, adversary tactics, and indicators of compromise (IOCs), which can be used to develop hypotheses and guide the search for potential threats.
RESOURCES
