Modern organizations are undergoing transformation with IT services penetrating across the business spectrum. There is a surge in adoption of cloud-based environments, agile application development practices and use of diverse, custom operational tools.
Amid this changing business landscape, the attack patterns have considerably changed as well with the AI, automation and insider threats. Plus, the end-user focused endpoints are the primary target in the attack campaigns of today.
Security operations teams can now leverage Extended Detection and Response (XDR) tool, which is seen as a better alternative to or extension of other security tools.
This next-gen security approach and advanced features make it an industry standard, empowering teams to detect, investigate and respond faster and smarter.
What is an XDR Tool?
The definition of Extended Detection and Response (XDR) varies depending on who you ask. Some see it as a technology for unifying telemetry while others as a comprehensive response automation solution. This is because different vendors have built XDR with different features.
That was an overview about the Extended Detection and Response approach in security. Gain deep insight about XDR with our blog Extended Detection and Response (XDR) Guide.
But what exactly is an XDR tool? It is a threat detection and response tool in cybersecurity that extends beyond the capabilities of its predecessors like EDR and NDR.
Extended detection and response tool consolidates telemetry across multiple security layers such as endpoint, email, server, cloud and network. It uses AI models for automation of repetitive tasks. Adds data analytics and threat intelligence to analyse and correlate data, detect and investigate threats and automate centralized and appropriate responses across the entire IT ecosystem.
Compared to EDR (Endpoint Detection and Response), XDR offers broader visibility beyond endpoints. While MDR (Managed Detection and Response) is a service-driven model often leveraging EDR or XDR, organizations can manage XDR tool internally or in a hybrid model.
Still find detection and response tools puzzling? Read our detailed blog EDR vs MDR vs XDR.
Benefits of Extended Detection and Response Tools
Those organizations still struggling to fill the security gaps for effective detection and response, can benefit from XDR tools.
Extended detection and response tool essentially amplifies the speed and scale at which detection and response can be done by security teams. Here are some of the key benefits:
- Improves threat detection accuracy by unifying signals from multiple vectors
- Reduces false positives
- Cuts investigation time
- Enhances endpoint security
- Reduces alert fatigue by correlating alerts into prioritized threat stories
Organizations benefit from faster incident response, simplified operations and enhanced visibility, all while lowering the total cost of ownership. Most importantly, many organizations now prefer XDR because they future proof your cybersecurity strategy in a multi-vector attack landscape.
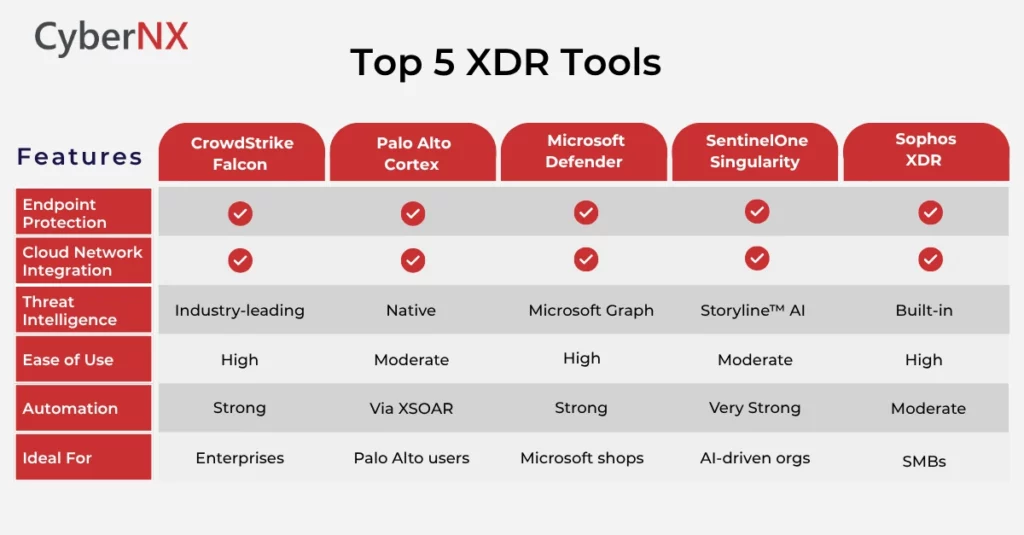
Top 5 XDR Tools
There are several Extended detection and response tool options available in the market today, but their functionalities differ. Therefore, to make it easier for you, we have given an overview of the top 5 XDR tools in 2026:
1. CrowdStrike Falcon Insight XDR
It is not surprising to see CrowdStrike Falcon Insight at the top. This XDR tool builds upon their industry-leading endpoint protection foundation with extended capabilities that span across cloud, identity, and workloads.
Key Features:
- Native integration with their EDR and threat intelligence
- Correlates data across endpoints, identity, and workloads
- AI-powered threat detection with automation, detecting wide array of threats
- Real time response actions via single console
- Lightweight agent with minimal performance impact
2. Palo Alto Networks Cortex XDR
Another well-known vendor in the cybersecurity space, Cortex XDR by Palo Alto Networks gathers data from network, endpoint and cloud, offering a holistic view of existing and emerging threats. It is known for integrations with other Palo Alto security products.
Key Features:
- Unified, automated incident management across endpoints, cloud, and network
- Machine learning-focused behavioural analytics
- Native integration with Palo Alto firewalls and Prisma Cloud
- Root cause analysis and threat visualization capabilities
- Automated playbook execution via Cortex XSOAR
3. Microsoft Defender XDR
Include in their security suite, Microsoft Defender XDR (formerly Microsoft 365 Defender) offers native XDR capabilities across Microsoft’s ecosystem that includes endpoints, identity, email and cloud apps.
Key Features:
- Integration with Microsoft 365, Azure and Windows endpoints
- Cross-domain threat correlation (email, identity and endpoint)
- Attack simulation and secure score benchmarking
- Automated investigation and response
- AI-driven incident timelines and analytics
4. SentinelOne Singularity XDR
SentinelOne’s Singularity XDR, released in 2020, is known for autonomous, real time threat mitigation. Plus, this Extended detection and response tool uses AI and machine learning to detect and respond at good speed.
Key Features:
- Autonomous detection and response without cloud dependency
- Patented Storyline™ technology for contextual threat visualization
- Script less malware and fileless attack detection
- Ransomware rollback and real time remediation possible
- Cloud, container and IoT visibility
5. Sophos XDR
Sophos XDR upgrades its Intercept X with insights across email, server, firewall and cloud workloads, making it equal to other similar XDR tools. Plus, it integrates smoothly with the Sophos Central platform.
Key Features:
- Data lake analytics from multiple sources
- Extended telemetry from firewall, server, mobile and email
- Threat hunting using SQL-based queries
- Easy integration with MDR services from Sophos
- Scheduled reports and trend analytics
Bonus mentions include Trend Micro Vision One and Cynet. The former offers robust detection and correlation capabilities tailored for hybrid cloud and containerized environments. The later is known for its built-in automation, MDR capabilities and all-in-one security stack suited for lean IT teams.
Comparison Chart of Top 5 XDR Tools
Here, you will find key features that differentiate the top 5 XDR tools.
How to Choose the Right Extended Detection and Response Tool
First, assess your IT environment, existing tool stack and in-house security resource. Based on this assessment, you should choose the right Extended detection and response tool according to your security and business needs. Here are few key considerations:
- Existing tech stack compatibility
- Cloud, hybrid or on-premises deployment needs
- Required level of automation and AI support
- Budget and licensing model
- Internal team maturity
A good XDR tool should improve visibility, simplify security operations and make the endpoint protection strategy effective.
Conclusion
Once, XDR was considered as the future concept. Today, it has become a reality with advanced features, necessary for proactive, intelligent and unified threat defence. It empowers internal SOC teams to offer complete security to organizations.
Our XDR services promise to offer you advanced automation, deeper visibility and better ROI on security investments. Plus, our experts can help you protect your entire IT environment from modern and advanced threats. Contact us today.
XDR Tool FAQs
How does XDR improve analyst efficiency compared to traditional security tools?
XDR streamlines security operations by consolidating alerts from multiple vectors – endpoints, cloud, email, and network – into a single platform. Analysts no longer need to manually stitch together fragmented data from disparate tools. With correlated incidents, prioritized threat stories, and automated investigations, XDR significantly reduces mean time to detect (MTTD) and respond (MTTR). This allows teams to focus on high-value tasks instead of alert triage.
Can XDR be used in small to mid-sized businesses, or is it only for large enterprises?
While XDR is often marketed toward enterprises, many modern XDR platforms are designed with scalability in mind. Vendors offer XDR solutions tailored for SMBs, featuring simpler deployments, intuitive dashboards, and even managed services. Smaller businesses benefit from centralized visibility and threat response without needing large security teams or complex integrations.
Is XDR compatible with existing SIEM or SOAR systems?
Yes, most leading XDR solutions are designed to integrate with existing SIEM and SOAR tools. While XDR consolidates data and automates many tasks, it can complement SIEM systems by feeding enriched telemetry and correlation insights. Similarly, integration with SOAR platforms allows for deeper playbook customization and cross-environment automation. Organizations can enhance – not replace – their existing security stack with XDR.
What types of threats does XDR detect more effectively than EDR or standalone tools?
XDR shines in detecting multi-stage and lateral movement attacks that span across endpoints, email, cloud, and network layers. Unlike EDR, which is limited to endpoint data, XDR correlates diverse signals to uncover stealthy threats like credential abuse, supply chain compromises, and cross-domain phishing campaigns. Its ability to spot patterns across multiple surfaces makes it especially powerful against advanced persistent threats (APTs).