Vulnerability Scanning Services
We deploy advanced vulnerability scanning tool sets that address your specific security, compliance and business needs.
Talk to our Experts Today





















INTRODUCTION
Find System Weaknesses & Reduce Exposure with Vulnerability Scanning Services
Our experts use advanced tools to scan your systems on a regular basis. This reveals your entire attack surface and engineer out vulnerabilities, minimizing risk of a data breach.

We address key challenges:
Unknown and exploitable flaws remain in assets. Our scans map and flags them so teams can plan and prioritized fixes.
Our tool sets surface legacy systems & backlog patches, reducing exposure with automated verification and tracking.
Simplifying compliance by detecting, documenting and measuring vulnerabilities against defined compliance controls.
Unplanned outages tied to security incidents are reduced by identifying critical weaknesses before attackers exploit.
Regular scans evaluate integrations, vendor connections and supply-chain components to reveal third-party exposures.
PROCESS
How It Works?
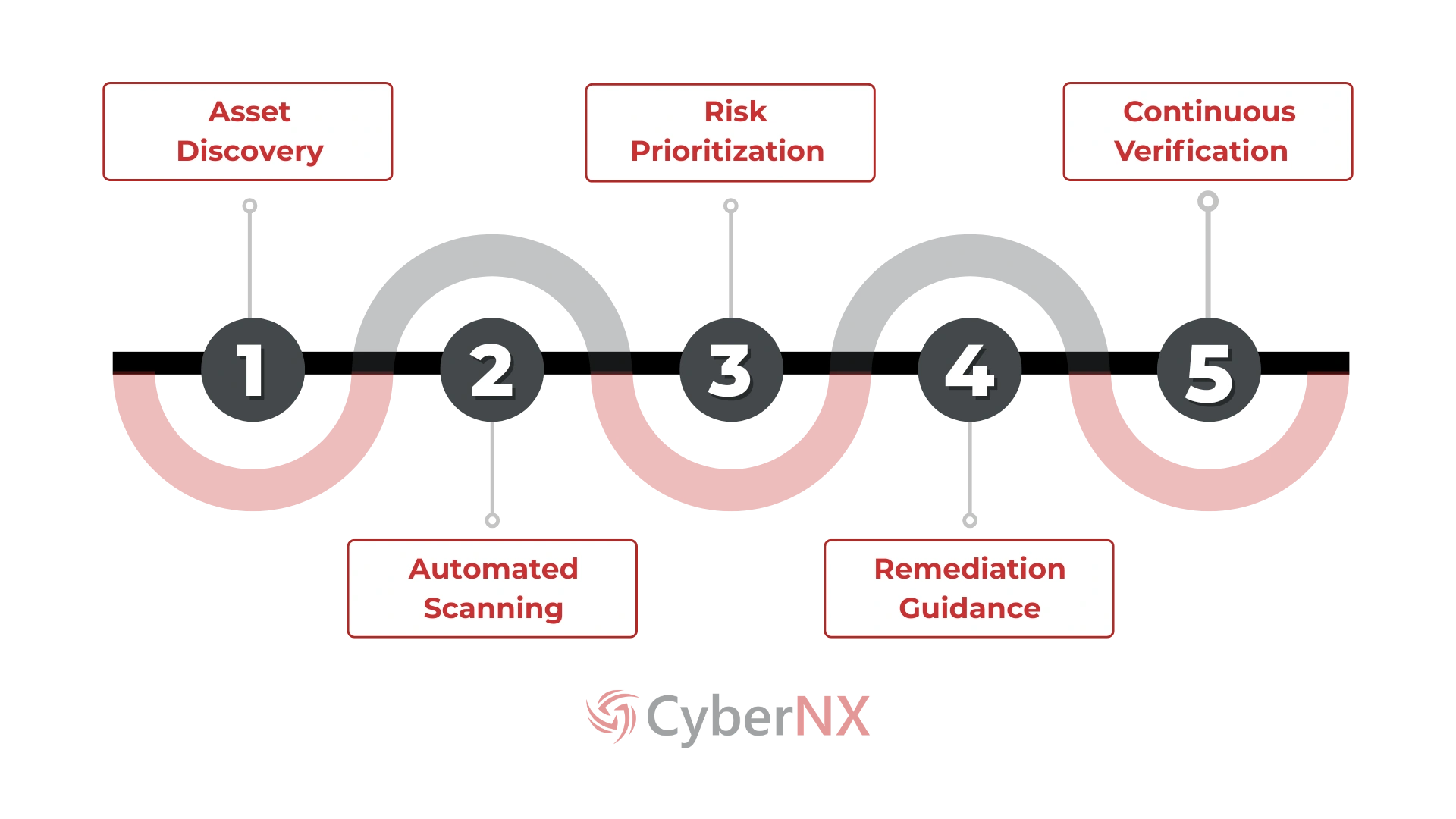
See Risks Clearly and Act Decisively with Our Vulnerability Scanning Solutions.
APPROACH
Why Choose CyberNX for Vulnerability Scanning Services?
Our engineering and security team deploy vulnerability scanning tools that is in sync with your specific environment. The focus is on measurable risk reduction along with practical reports and technical guidance.
Continuous Scanning
24/7 scanning across networks, cloud workloads and apps to detect newly introduced vulnerabilities and configuration drift automatically.
Custom Rulesets
Tailored detection rules to stack and frameworks so scans reflect real-world business priorities, technical nuances and organizational risk.
Risk Prioritization
Combine exploit metrics, asset criticality & business context to rank findings, delivering a remediation roadmap for practical execution.
Actionable Reporting
Readable & exportable reports with step-by-step fixes, evidence traces and executive summaries that inform both engineers and leadership.
Remediation Support
Engineers guide patching workflows, verify fixes & provide technical playbooks to reduce mean time to remediation & long-term enablement.
Customer first Approach is our guiding principle.
BENEFITS
Ward Off Exploitation Attempts & Protect IT Assets with Vulnerability Scanning
Reduced Attack Surface
Continuous discovery & prioritized fixes shrink the available attack surface, lowering the likelihood & impact of successful intrusions.
Audit Readiness
Evidence trails, change logs and attestation-ready reports make audits highly efficient and compliance proofs demonstrably consistent.
Faster Remediation
Clear priorities, developer-centric guidance reduce investigation time & accelerate patch deployment in production, staging environments.
Operational Resilience
Early detection prevents security incidents from cascading into outages, preserving uptime, customer trust and business operations.
Cost Efficiency
Automating detection and validating fixes reduce emergency response costs and lower total security spend across the organisation.
For Customized Plans tailored to Your Needs,
Get in Touch Today!
FAQs
Frequently Asked Questions
Vulnerability scanning automates detection of known flaws across assets, while penetration testing simulates real-world attacks to validate exploitability.
Best practice is monthly or after significant infrastructure changes. Continuous scanning provides the most accurate, real-time risk visibility.
Yes. Scans generate evidence reports and remediation records that map directly to compliance standards like PCI DSS, ISO 27001, and HIPAA.
CyberNX scans servers, applications, APIs, cloud workloads, endpoints, and third-party integrations to provide complete attack surface visibility.
RESOURCES
