If you are in cybersecurity, you know that new vulnerabilities are discovered daily. You also know for the fact that attackers move faster than ever. And in the middle of it all, you’re staring at reports with hundreds (sometimes thousands) of issues that need attention.
Which ones matter most? Which can wait? How do you keep the business running while also keeping it secure? Understanding the nuances of vulnerability management process can help you get maximum out of the program.
In case, you are just starting, read our expanded and detailed blog Vulnerability Management.
The process basically gives a clear, repeatable way to identify risks, prioritize what matters and take action before an attacker does. Done right, this process reduces chaos. It also helps in building trust across teams and give leaders confidence that they’re protecting the business in a practical, sustainable way.
Is Vulnerability Management Process Hard to Follow?
Every CTO or CISO knows the frustration. You run a scan and – bam – hundreds, maybe thousands of vulnerabilities show up. It’s overwhelming. Some look urgent. Others have been lingering for months. And then there’s the tension: do you patch now and risk disrupting business operations, or wait and risk exposure?
It feels like being the captain of a ship with leaks popping up all over. Plug one hole, another appears. That’s the reality of security today. The process isn’t about eliminating every hole forever. It’s about creating a rhythm and discipline to manage them smartly.
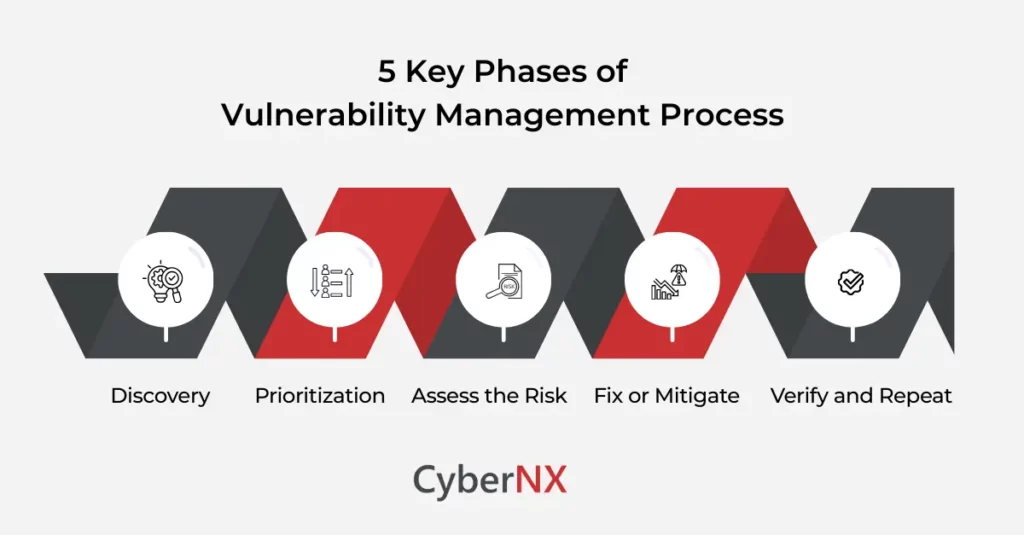
Vulnerability Management Process: 5 Key Phases
Let’s break it down. The vulnerability management process usually unfolds in five big steps. They may look neat on paper, but in real life, they often overlap. And that’s okay.
1. Discovery
You can’t protect what you don’t know about. That means scanning your systems, applications, endpoints, cloud assets—basically everything connected to your network.
Many companies get stuck here because their IT environment is sprawling. New apps behave abnormally without notice. Shadow IT sneaks in. That’s why discovery is never one-and-done, it’s continuous.
2. Prioritization
Here’s the challenges: not every vulnerability exposed is a fire. Some are just sparks that may never ignite. Others are flames ready to burn down everything that come its way. The vulnerability management process requires you to triage.
Think: What assets are critical? What data sits behind this system? How easy is this to exploit? That’s how you avoid chasing noise and instead focus on the vulnerabilities that could genuinely sink your ship.
3. Assess the Risk
Sometimes a vulnerability looks scary on paper, but in your specific setup, it’s less of a threat. Other times, something minor turns into a big deal because of where it lives in your environment.
Risk assessment is about context. Imagine finding a cracked tile in your bathroom. Annoying, but not catastrophic. Now imagine that same crack on a tile holding up your kitchen ceiling fan. Context changes everything.
4. Fix or Mitigate
Remediation usually means patching, but it could also mean applying a workaround, changing a configuration or isolating a system.
Here’s where leadership frustration often increases. Patching takes coordination across teams. Sometimes downtime and sometimes arguments. The vulnerability management process works best when IT and security teams communicate clearly and when leadership supports making the tough call to patch – even when it’s inconvenient.
5. Verify and Repeat
Fixing isn’t the end. You need to verify that the vulnerability is actually gone. Then? Start again. This process is a cycle. Not a one-time project. Threats evolve. New cracks appear. Repeating the process is what keeps your organization resilient.
Challenges Faced by IT Leaders
CTOs, CISOs, security leads, you’re not only managing vulnerabilities, you’re managing expectations. Business leaders want things fast, secure and cheap. But the truth? You can usually pick two.
The vulnerability management process forces tough choices. Which systems get patched first? Which business units face downtime? Which risks can you live with for now? These aren’t easy calls, and they require backing from the top.
It’s less about tools (though tools matter) and more about culture. Is your organization committed to treating security as ongoing hygiene?
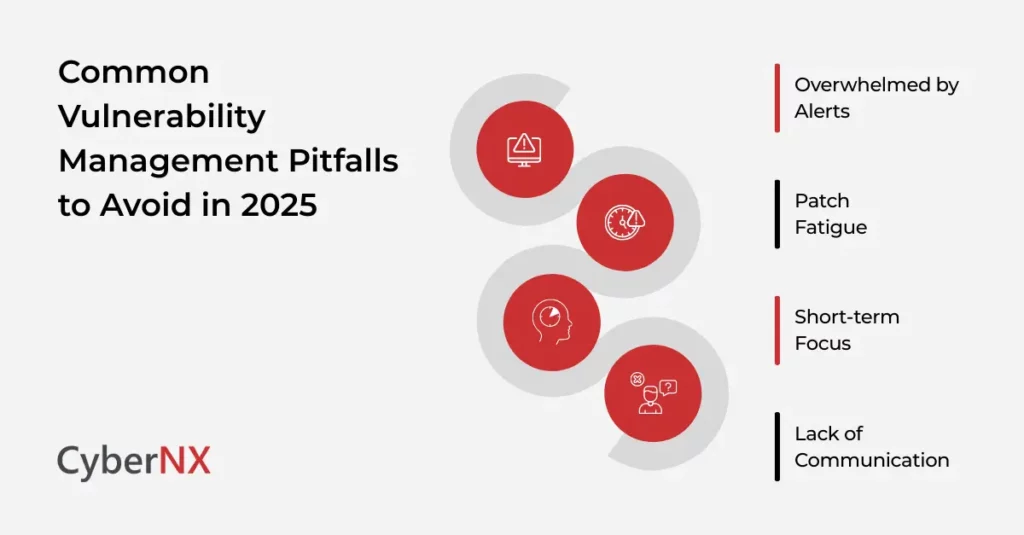
Common Pitfalls Observed by Our Experts
Even the best security teams fail. Here are a few patterns we’ve seen:
- Overwhelmed by Alerts: You drown in scan reports but don’t act. Fix: build a clear prioritization framework.
- Patch Fatigue: Teams get tired of constant updates. Fix: automate where possible and schedule downtime windows.
- Short-term Focus: You fix today’s issue but ignore systemic gaps. Fix: look at trends, not just isolated incidents.
- Lack of Communication: IT, security, and leadership aren’t aligned. Fix: create a shared scorecard for visibility.
Each of these pitfalls chips away at trust and efficiency. Being aware of them helps you steer clear.
Vulnerability Management Process Outcomes
Here’s the good news. When the vulnerability management process is embedded into the DNA of your business, everything feels calmer. You move from firefighting to strategy.
Instead of waking up to a headline about a breach that could have been avoided, you get to tell the board, “Yes, we knew about that vulnerability. Yes, we patched it. Here’s the proof.” That confidence is worth its weight in gold.
And beyond peace of mind, there’s the real-world payoff: reduced downtime, stronger compliance posture and a reputation for taking security seriously.
Emerging Threats and the Future of Vulnerability Management
In 2025, organizations face new categories of vulnerabilities that demand attention:
- Supply chain weaknesses
- Critical cloud misconfigurations
- AI-powered phishing attacks
Recent incidents have shown just how costly this can be. High-profile breaches caused by unpatched software or overlooked third-party components have disrupted operations, exposed sensitive data and impacted reputations globally.
Looking ahead, the vulnerability management process itself is evolving to keep pace. Organizations are moving beyond reactive patching. Experts see security leaders tilting towards:
- Predictive remediation
- Leveraging AI to identify the vulnerabilities most likely to be exploited
- Continuous risk scoring helps prioritize efforts based on real-world impact
- AI-driven patch management automating routine fixes without compromising operational uptime
For security leaders, this means anticipating tomorrow’s risks and embedding foresight into every step of the process. Those who embrace these innovations will reduce exposure, streamline operations and stay one step ahead of attackers in an increasingly complex digital environment.
Conclusion
Vulnerabilities aren’t going away. New ones are disclosed every week, and attackers are quick to take advantage. The difference between organizations that stay resilient and those that suffer avoidable breaches often comes down to one thing: process.
The vulnerability management process gives you a structured, ongoing way to deal with the noise – discovering assets, prioritizing threats, assessing risks, applying fixes, and verifying results. It’s not a one-time project but a discipline that keeps your security program aligned with business realities.
For security leaders, this process means fewer surprises, faster response to emerging threats, and stronger confidence when reporting to the board or regulators. It’s not about perfection – it’s about having a system in place that ensures the biggest risks are handled before they turn into incidents.
If you don’t already have a defined vulnerability management process, now is the time to make it a priority. Contact us for vulnerability management services.
Vulnerability Management Process FAQs
How often should a vulnerability management process be carried out?
The frequency depends on your industry, compliance requirements, and risk appetite. Highly regulated sectors like finance or healthcare may need continuous scanning and weekly patch reviews, while others might manage with monthly cycles. What matters most is consistency and the ability to adapt when new, critical vulnerabilities emerge.
What’s the difference between vulnerability management and vulnerability assessment?
A vulnerability assessment is a snapshot – it identifies weaknesses at a point in time. Vulnerability management is the ongoing, structured process of discovery, prioritization, remediation, and verification. In other words, assessments feed into the broader vulnerability management process, but on their own they’re not enough.
Can automation fully handle the vulnerability management process?
Automation helps by reducing noise, scheduling scans, and even applying patches in some cases. But it can’t replace human judgment. Context – like understanding business priorities or regulatory risks – requires leadership decisions. The best programs blend automation with skilled oversight.
How does vulnerability management support compliance requirements?
Regulations like PCI DSS, HIPAA, and ISO 27001 all expect organizations to have ongoing vulnerability management in place. A strong process provides audit trails, proof of patching, and evidence of risk reduction. It’s not just about passing audits – it’s about reducing the chance of fines and reputational damage.