Every organisation that runs software, networks or cloud services carries hidden risks. The Vulnerability Management Lifecycle is the systematic approach that turns those risks into manageable work. It is important to state and reiterate that it is not a one-time project. But a continuous program that protects value and preserves trust.
For CISOs, CTOs and business leaders, understanding this lifecycle is less about technical minutiae and more about how reliably the organisation finds, fixes and proves risk reduction over time.
At its heart, the vulnerability management lifecycle is a loop: discover, assess, prioritise, remediate, verify and learn. Each stage feeds the next, and each requires clear ownership, measurable outcomes and the right mix of automation and human judgment. Get any stage wrong – triage that never happens, patches that break production, or blind spots in discovery – and the loop fails.
6 Phases of Vulnerability Management Lifecycle
Here are the five phases which constitute vulnerability management cycle:
1. Discover
You cannot protect what you cannot see. Discovery blends automated scanning, asset inventories and integration with cloud and CI/CD pipelines to map your attack surface. The best programs treat discovery as continuous telemetry, not a quarterly checkbox: new containers, shadow cloud services and third-party components should automatically appear in your inventory and be fed into this lifecycle.
2. Assess and Prioritise
Scanners find thousands of issues. Prioritisation separates distraction from action. A modern approach weights exploitability, asset criticality, business impact and compensating controls. Combining threat intelligence with contextual data (which systems talk to production, which hold sensitive data) reduces mean time to meaningful action and aligns security work with business outcomes.
3. Remediate
Remediation can be patching, configuration change, compensating control or planned acceptance with documented risk. Assign clear owners and realistic SLAs based on severity and business risk. Where direct fixes are slow or risky, use containment – micro segmentation, access restrictions or virtual patching – but log decisions and timelines in the lifecycle so they are auditable and revisited.
4. Verify
Verification closes the loop. After remediation, automated rescans and manual validation confirm fixes. For high-risk findings, run regression tests and apply attack simulations where feasible. Verification data is critical evidence for auditors, boards and incident response teams – it proves that the vulnerability management lifecycle produces measurable risk reduction, not just churn.
5. Report and Govern
Reporting must translate technical detail into business implications: which vulnerabilities were closed, how long it took, and how residual risk is being managed. Use dashboards for operational teams and concise executive summaries for leadership. Governance integrates vulnerability outcomes into change controls, procurement and third-party risk assessments so the lifecycle drives decisions across the organisation.
6. Learn and Iterate
Post-remediation reviews, root-cause analysis and metrics help improve the process. Common fixes become automation playbooks; repeat findings surface training gaps or architectural issues. Continuous refinement ensures the vulnerability management lifecycle matures from reactive firefighting to strategic risk reduction.
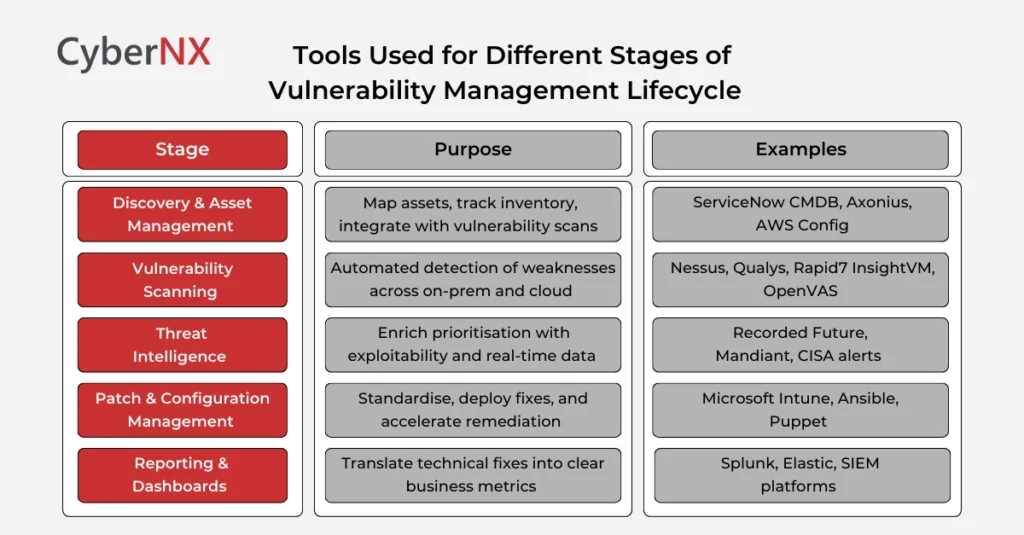
Common Tools Used for Vulnerability Management
The right tools enable speed and consistency across the lifecycle. While no single product covers everything, leaders often see value in combining multiple categories:
Selecting tools should not be a procurement checklist but a strategy aligned to your environment, scale and regulatory landscape. A mature vulnerability management lifecycle combines automation with contextual business logic, not tool sprawl.
Practical Metrics to Track
Here are the major metrics IT security leaders should track:
- Time to discover (from asset creation to visibility)
- Time to assess and prioritise
- Time to remediate by severity
- Percentage of critical findings verified within SLA
- Reduction in exploitable, externally-facing vulnerabilities over time
Leadership Checklist
Those in the leadership should set objectives, take appropriate decisions and observe if the output matches what is required.
- Treat vulnerability management as a program with budget and accountable owners.
- Set SLAs tied to business impact, not scanner output alone.
- Invest in discovery integrations (cloud, containers, CI/CD) to feed the lifecycle.
- Use automation for repetitive verification but retain human judgment for prioritisation.
- Tie vendor and third-party assessments into your lifecycle governance.
Future of Vulnerability Management
The landscape of vulnerabilities is shifting rapidly, and so must the lifecycle. Leaders should anticipate these trends:
- AI-driven exploitation: Attackers are already using AI to craft exploits and phishing lures, which means detection and prioritisation must also leverage AI.
- Cloud-native complexity: With ephemeral containers, serverless workloads and SaaS integrations, discovery will need to be near real-time and integrated into development pipelines.
- Supply chain visibility: Software bills of materials (SBOMs) will become standard, feeding lifecycle assessments with component-level data.
- Continuous validation: Penetration testing and red teaming will increasingly run as ongoing services, closing the gap between theory and real-world exploitation.
- Board-level accountability: As regulations tighten, expect vulnerability reports to become part of quarterly board packs, making the vulnerability management lifecycle a governance issue, not just a security practice.
The organisations that thrive will be those that automate aggressively, invest in skilled teams and keep the lifecycle aligned to both business outcomes and evolving threats.
Learn more about this topic with our blog Vulnerability Management Guide.
Conclusion
The best security programs treat vulnerability management as a business capability – measurable, repeatable and accountable. The vulnerability management lifecycle is the operating rhythm that turns technical findings into business resilience. Start small, measure relentlessly, and make the loop your competitive advantage.
If you would like a ready-to-use mapping template, produce an inventory of owners, tools and SLAs for each stage and review it monthly. That simple habit moves vulnerability handling from tactical firefighting to strategic risk governance – and it creates a measurable improvement that executives can see and sign off on. Connect with us for vulnerability management services.
Vulnerability Management Lifecycle FAQs
How often should an organisation run the vulnerability management lifecycle?
The cycle should run continuously, not just during quarterly scans or audits. Modern enterprises with dynamic cloud environments often run automated discovery daily and prioritisation workflows weekly, ensuring vulnerabilities are addressed before attackers exploit them.
What role does executive leadership play in the vulnerability management lifecycle?
Executives provide sponsorship, allocate budgets, and enforce accountability. Without leadership support, remediation deadlines slip and reporting loses visibility at the board level. CISOs and CTOs should ensure the lifecycle is embedded in governance, risk, and compliance processes.
How is vulnerability management different from patch management?
Patch management is one element of remediation, while the vulnerability management lifecycle covers the full loop – discovery, assessment, prioritisation, remediation, verification, and continuous improvement. In short, patching is tactical, but vulnerability management is strategic.
Can the vulnerability management lifecycle be outsourced?
Yes, many organisations partner with managed security service providers (MSSPs) or specialised vulnerability management services to run parts or all of the lifecycle. Outsourcing brings expertise and automation, but leadership must still own governance, risk decisions, and reporting.