The main objective of IT security leaders is to keep their respective organizations secure without business disruptions from cyberattacks. A vulnerability assessment report is quite useful in this regard. It gives a clear overview of security flaws present in your entire IT systems and networks. This in turn, help CISOs to prioritize fixes, discuss budgets and plan for compliance. More importantly, a vulnerability assessment and resultant report help prevent costly breaches before they could happen.
In this blog, our experts reveal what goes into a report and why it matters beyond compliance. Plus, you will get a quick overview of how to craft and interpret reports with clarity.
What is Cybersecurity Vulnerability Assessment Report?
A vulnerability assessment report is a document that a cybersecurity testing team hands over to security leaders after conducting vulnerability assessment.
Find everything about this sensitive security exercise in our blog Vulnerability Assessment Guide.
Depending on the testing scope, this report highlights existing flaws in your IT environment. The scope can vary from testing servers, apps and cloud system to APIs, IoT device or all of them.
Know that a generic report will throw a list of issues your way, and that’s it. However, a professional, expert-led and well-prepared report will show vulnerabilities by risk level, exploitability and business impact.
Always partner with vulnerability assessment service providers who tell you the problems and also provides actionable recommendations to fix them.
Is Vulnerability Assessment only required for Compliance?
Too often, business leaders assume assessments are box-ticking exercises for regulatory frameworks like CERT-IN, RBI, SEBI or ISO 27001, PCI DSS and GDPR. While vulnerability compliance matters and offers many benefits, it’s far from the whole story.
Here’s the truth: cybercriminals don’t care whether you’re compliant or not. They look for weaknesses, regardless of your paperwork. An assessment report helps you see your infrastructure the way an attacker would.
Yes, regulators demand proof of testing, but smart organizations go beyond compliance. They use vulnerability assessments as proactive strategy, catching flaws early, reducing incident response costs and earning customer trust.
5 Major Components of a Vulnerability Assessment Report
What encapsulates a good report? What components really add value to you and help you make right decisions? A high-quality report typically includes:
1. Executive Summary
Business leaders approve security budgets and make final decisions. Therefore, a vulnerability assessment report presents technical findings into simple insights. For example, which digital assets were tested, what are the critical risks identified and where does the company stand as far as security posture is concerned. In short, it answers the C-suite’s burning questions.
2. Methodology
This section in the report explains the “how’ part of vulnerability assessment. The tools used, frameworks followed like OWASP or NIST and scope by the service provider. This transparency helps understand the expertise and capabilities of the testing team and gives credibility to the results.
Gain deeper understanding of what is involved in this phase with our blog Vulnerability Assessment Methodology.
3. Findings and Risk Ratings
The is the key part of the report. This helps your business understand how good or bad your security posture is. It highlights the vulnerabilities found in the systems and filters it based on severity (Critical, High, Medium, Low). In addition, one glance and you can find the potential impact and exploitability. This fastens decision making.
4. Remediation Recommendations
Once the problems are identified, the report will include a section on remediation recommendations. A step-by-step guidance on how to fix the flaws found. This could be patching, configuration changes or architectural adjustments.
5. Appendices and Technical Evidence
The report also contain detailed logs, screenshots and proof-of-concept exploit data for IT teams. This ensures no ambiguity and complete transparency.
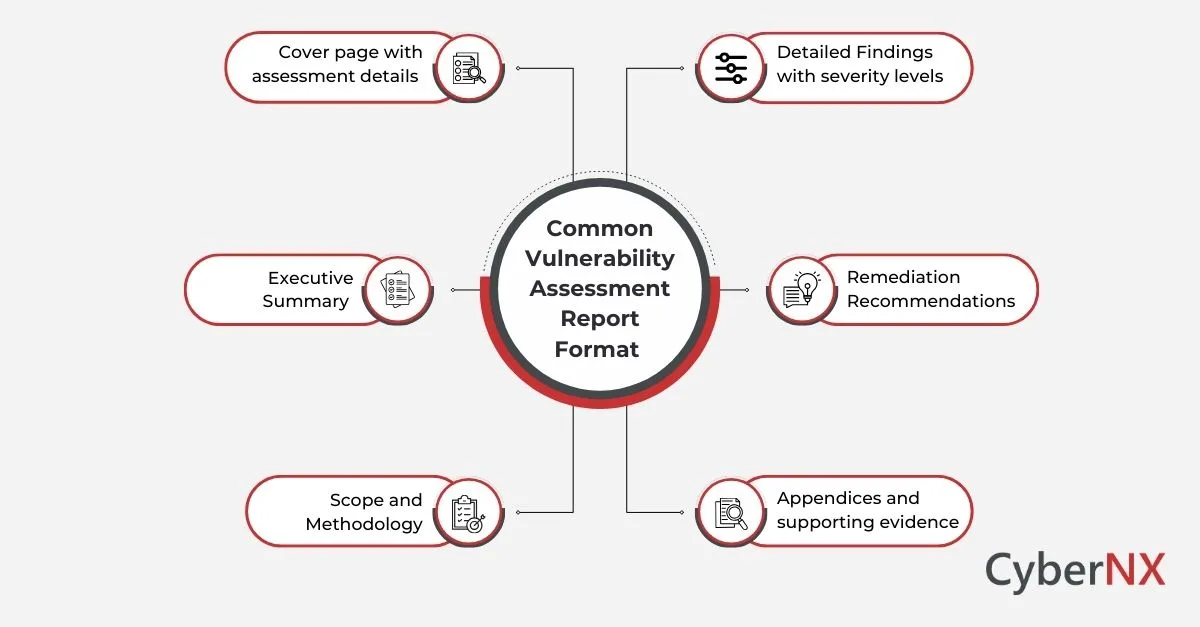
Vulnerability Assessment Report Format
While formats vary, a professional report often follows this structure:
This standardized approach ensures that everyone – from boardroom to server room – understands the findings and next steps.
How to Write Vulnerability Assessment Report?
In our experience of running vulnerability assessment, writing a report is part science and part storytelling. Science for technical teams and story to give clarity to executives.
Here’s a brief overview of how an excellent VA report is created or should be created:
- Start with business context: Link vulnerabilities to what matters most – customer data, uptime, financial loss, or reputation damage.
- Use layered reporting: Executive summary for leadership, detailed technical findings for IT staff.
- Make risk actionable: Avoid generic “patch required” language. Instead, give remediation steps with timelines and priorities.
- Incorporate expert insights: Our team often adds analyst commentary – why a vulnerability exists, common exploit patterns, and real-world case studies. This gives decision-makers context, not just data.
Difference between Pentesting Report and Vulnerability Assessment Report
Penetration testing and vulnerability assessment are different cybersecurity practices. Both generate reports, but the content and purpose differ.
Here’s a concise chart to clarify:
| ASPECT | VA REPORT | PT REPORT |
| Objective | Identify and prioritize weaknesses | Actively exploit vulnerabilities to simulate attacks |
| Approach | Automated scans + manual validation | Manual, adversary-style exploitation |
| Output | Risk ratings, remediation steps | Exploit proof, attack paths, impact demonstration |
| Audience | Security teams + leadership | Primarily technical & security teams |
| Frequency | Regular (monthly/quarterly) | Periodic (annually/bi-annually) |
In short, vulnerability assessments give you breadth, while penetration tests give you depth. Smart organizations use both together.
Conclusion
In today’s threat landscape, waiting for attackers to reveal your weaknesses is no longer an option. A vulnerability assessment report acts as your organization’s early warning system – illuminating blind spots before they turn into breaches.
For CEOs, CTOs, CISOs, and founders, it’s not just a technical necessity – it’s a business safeguard. By investing in regular assessments and understanding their reports, leaders transform cybersecurity from a compliance task into a competitive advantage.
Contact us today for vulnerability assessment services.
Vulnerability Assessment Report FAQs
How often should organizations conduct vulnerability assessments?
At least quarterly, though high-risk industries like finance or healthcare benefit from monthly checks.
Can vulnerability assessment reports be automated?
While tools automate scanning, expert validation and context are critical. Automation alone often produces false positives.
Who should receive the vulnerability assessment report?
Both leadership (for decision-making) and technical teams (for remediation). Reports can be tailored for each audience.
What happens if vulnerabilities in the report aren’t fixed?
Unpatched vulnerabilities leave you exposed to attacks, regulatory fines, and reputational damage. Inaction can cost far more than fixing the issue.