What matters to security teams today is clarity. They want to see real risks, and they want steps that could help them fix issues quickly. A VAPT report gives this clarity as it brings together findings from vulnerability assessment and penetration testing into one structured document. This report helps leaders understand their exposure. It also helps engineers prioritise remediation work.
But many teams still struggle. This is because some reports feel too technical while others lack business context. Some feel too vague and others feel overwhelming. We believe a VAPT report should be simple, relevant and easy to act on. This guide explains what a strong report includes and shows how to create one that supports real improvement.
What a VAPT report really is
You might know about VAPT and how it helps in finding loopholes in the system and fixing it before attackers do. But the key to a successful VAPT exercise is the report delivered in the end. This is because a VAPT report summarises security weaknesses found across systems, applications or networks. But it does more than list issues. It explains impact, shows the likelihood of exploitation and gives clear steps to fix them.
A well-written report supports teams at every level:
- Leadership sees risk in business terms.
- Engineers see exact fixes.
- Compliance teams see documented evidence.
What makes a good VAPT report
A high-quality report is:
- Clear
- Actionable
- Evidence-driven
- Easy to navigate
- Aligned with business impact
These qualities help teams move faster and strengthen defences with confidence.
Why VAPT reports matter
A VAPT exercise is only useful if the results are understood. Many teams collect data but struggle to convert insights into action. A strong report bridges this gap.
- Helps identify critical weaknesses: You see which issues pose real threats. You learn where attackers may start. This helps you fix the most important problems first.
- Supports compliance: Industries like BFSI, healthcare and IT services require documented testing. A clean VAPT report helps teams complete audits without stress.
- Builds stronger engineering practices: Developers understand where code needs improvement. Infrastructure teams understand where controls need strengthening. Security teams learn patterns that help them prevent future issues.
- Aligns security with business: Leaders want risk framed in simple terms. A clear VAPT report helps them make better decisions.
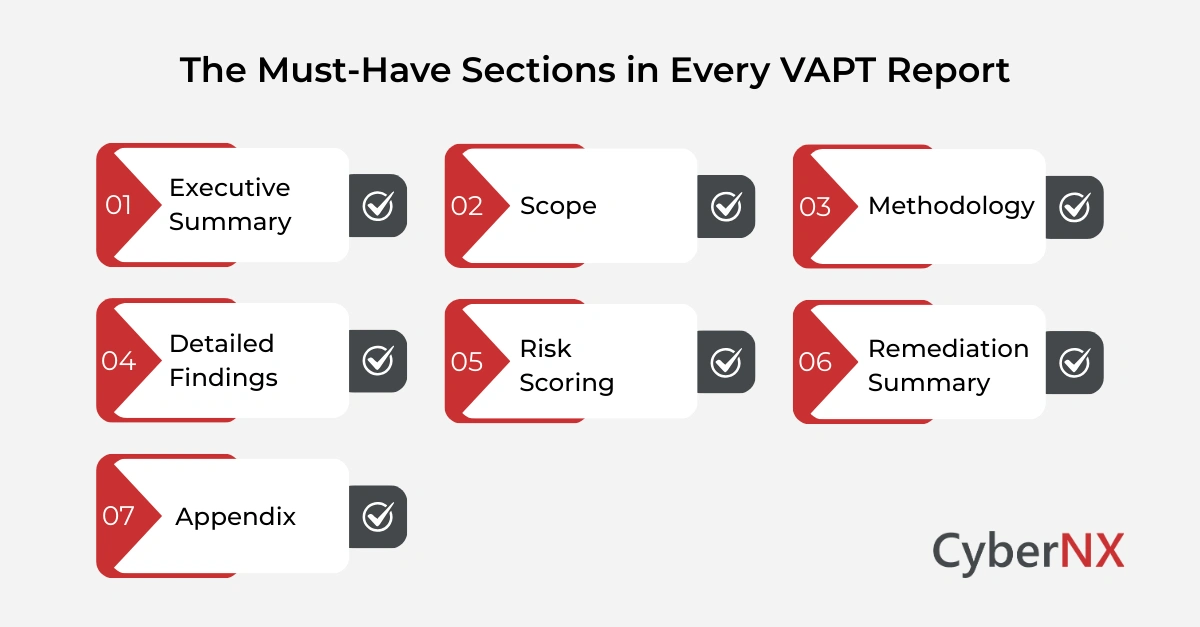
Key sections every VAPT report must include
Many teams search for a VAPT report sample to understand structure. While formats vary, certain sections are essential.
Below is the structure we use at CyberNX.
1. Executive summary
This is for leadership. It explains:
- High-risk issues
- Business impact
- Overall risk posture
- Required actions
It stays simple. No jargon. Just clarity.
2. Scope
This section lists:
- Systems tested
- Tools and methods used
- Limitations
- Testing timelines
A clear scope avoids confusion in future audits.
3. Methodology
We share our VAPT methodology in simple terms. Examples:
- Black-box testing
- Grey-box testing
- Manual verification
- Automated scanning
This gives credibility and transparency.
4. Detailed findings
This is the heart of the report.
For each issue, we include:
- Title of vulnerability
- Description
- Impact
- Severity rating
- Proof of exploitation
- Affected components
- Remediation steps
We keep the language direct and practical.
5. Risk scoring
We use standard models like CVSS. This helps teams prioritise.
6. Remediation summary
We highlight key fixes. Simple. Actionable. Easy for engineering teams.
7. Appendix
This includes:
- Tool outputs
- Screenshots
- Logs
- Reference links
It supports evidence needs during audits.
SANS Institute Reporting Essentials Guide 2024 says, “Clear reporting is as important as testing itself. Teams act faster when the report speaks their language.” We follow this approach when writing reports. We aim for clarity first. Tools and techniques come later.
How to make a VAPT report
If you want to create your own report, follow these steps. They keep the process simple and structured.
Step 1: Understand the audience:
A CTO, a security analyst and a developer read reports differently. Write with all three in mind.
Step 2: Start with high-level insights:
Decision-makers want a snapshot, whereas engineers want detail. Therefore, start with the big picture and then go deeper.
Step 3: Use a consistent severity scale:
Keep risk ratings simple. High, Medium, Low or CVSS is the usual method followed. In addition, maintain consistency because it helps in building trust.
Step 4: Add clear remediation guidance:
Do not write generic fixes. Instead, focus on writing exact steps. For example: Instead of “Sanitise user input”, write “Validate and escape user input in parameter X using method Y.” This will make it clear for key stakeholders.
Step 5: Provide proof:
Screenshots and logs reduce doubt. Teams act faster when evidence is clear.
Step 6: Summarise actions:
Add one page with key fixes because leaders prefer summaries and engineers appreciate quick references.
Sample outline: VAPT report sample
Below is a simplified sample you can use as a template.
1. Executive Summary
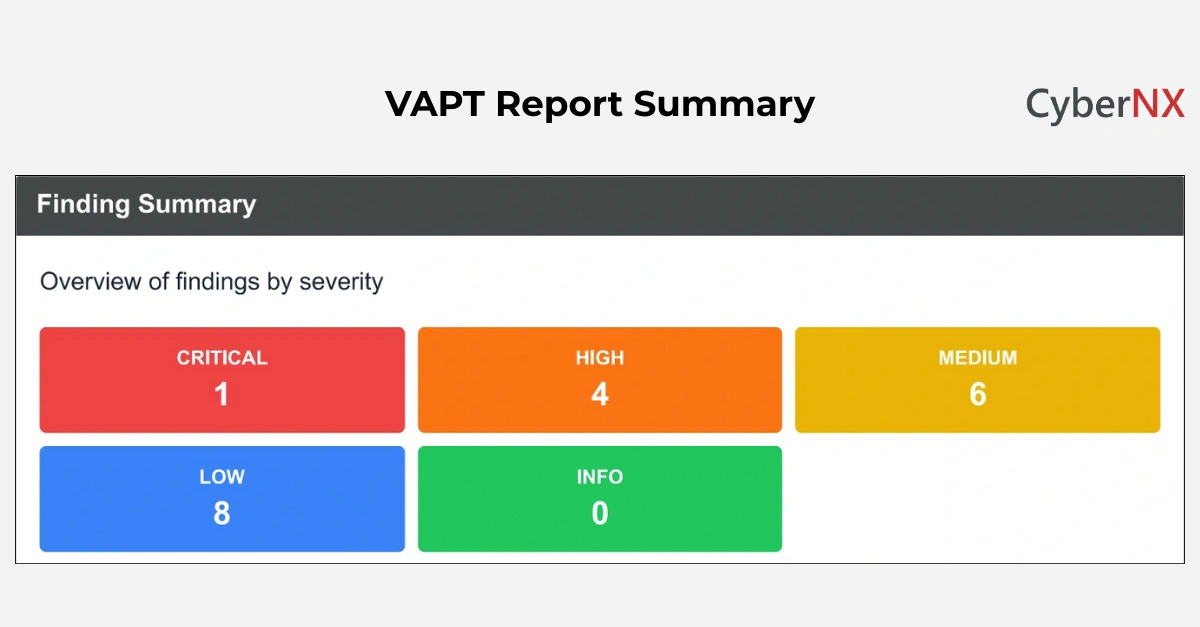
- Overall risk posture: Medium
- High-risk vulnerabilities: 2
- Medium-risk vulnerabilities: 5
- Low-risk vulnerabilities: 6
- Key recommendation: Patch server configuration and update authentication logic.
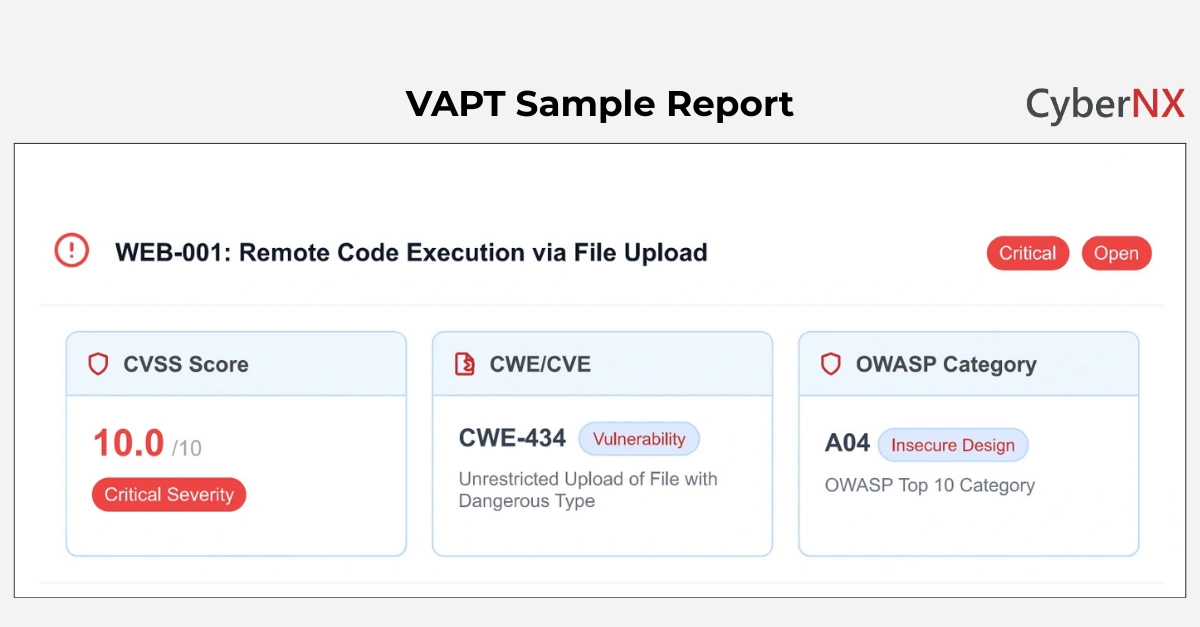
2. Finding Example
- Title: Insecure Direct Object Reference
- Severity: High
- Impact: Attackers can access other users’ data.
- Affected Modules: User profile API
- Proof: Provided with screenshots and test logs
- Fix: Add authorisation checks for every resource request.
This structure keeps the report readable and actionable.
How CyberNX creates high-quality VAPT reports
We keep reports simple and professional, focus on clarity and tailor insights to your business and technology stack.
Our reports offer:
- Clean summaries for leadership
- Clear risk ratings
- Detailed proof for engineers
- Actionable fixes
- Support calls to explain findings
- Guidance to strengthen long-term security
Our experience shows that clear reporting makes remediation faster and more effective.
Conclusion
A VAPT report is more than documentation. It is a roadmap for stronger security. A clear report helps leaders see risk. It helps engineers fix issues with confidence. And it supports compliance without friction. If you want a report that improves real security outcomes, we are here to support you. Book a consultation with us to know how our VAPT services can help your security program and how you can get a clear, actionable VAPT report that strengthens your security posture.
VAPT Report FAQs
How long does it take to prepare a VAPT report?
A typical VAPT report takes three to seven working days after testing is complete. The timeline depends on how many assets are in scope, the number of findings, and how much manual verification is required. Larger environments with several applications or complex APIs need additional time. We focus on accuracy and clarity, so each finding is reviewed, validated and documented before final delivery.
Can a VAPT report be used for compliance audits?
Yes. Most industries accept a well-documented VAPT report as part of their audit evidence. It supports standards like PCI DSS, ISO 27001, SOC 2, HIPAA and RBI guidelines. Auditors mainly look for clarity on scope, methodology, severity ratings and remediation timelines. A structured report helps your team complete the audit without stress and shows clear proof that security testing was done.
How detailed should remediation steps be in a VAPT report?
Remediation steps should be specific and practical. They should guide developers and infrastructure teams through exact fixes. Vague instructions slow teams down. Clear remediation guidance makes engineering work smoother. This includes the steps to fix the root cause, configuration changes, affected modules and references to best practices. When guidance is clear, teams complete remediation faster.
Do automated tools generate complete VAPT reports?
Automated tools help with scanning, but they cannot produce a complete and reliable report on their own. They often generate false positives and lack context on business impact. Manual validation is essential. A strong VAPT report blends automated results with manual testing, proof of exploitation and actionable remediation steps. This combination makes the report credible and useful for decision-makers.