Think of your company’s network like your home. You have locks on the doors (firewalls), an alarm system (antivirus), and maybe even a guard dog (intrusion detection). These are important, but sometimes, a clever thief can still find a way in. They might slip through an open window, or find a hidden key. They’re inside, but you don’t know it yet. This is where Cyber Threat Hunting comes in. It’s like having a detective who actively searches your house for anything out of place, even if the alarm hasn’t gone off. They look for the small clues – a misplaced item, a faint footprint – that tell you something is wrong.
In today’s world, cyberattacks are getting more sophisticated. Hackers are like those clever thieves. They’re good at bypassing the usual security measures and can cause big problems, like stealing your company’s data or shutting down your systems. So, how do we find these “insider threats” before they strike?
That’s where this guide comes in. It’s for CISOs, IT managers, and anyone responsible for data security. We’ll explain what threat hunting is, why it’s crucial, and how to do it effectively. We’ll cover different hunting methods, the tools you’ll need, and even how to build a team to use this approach. By the end, you’ll be much better equipped to protect your company from these hidden dangers, using simple, practical advice.
Understanding Threats
Cyber threats are no longer just simple viruses; they’re sophisticated attacks designed to bypass even the most robust defenses. Understanding the different types of threats is absolutely crucial for effective threat hunting – you can’t hunt for something if you don’t know what it looks like.
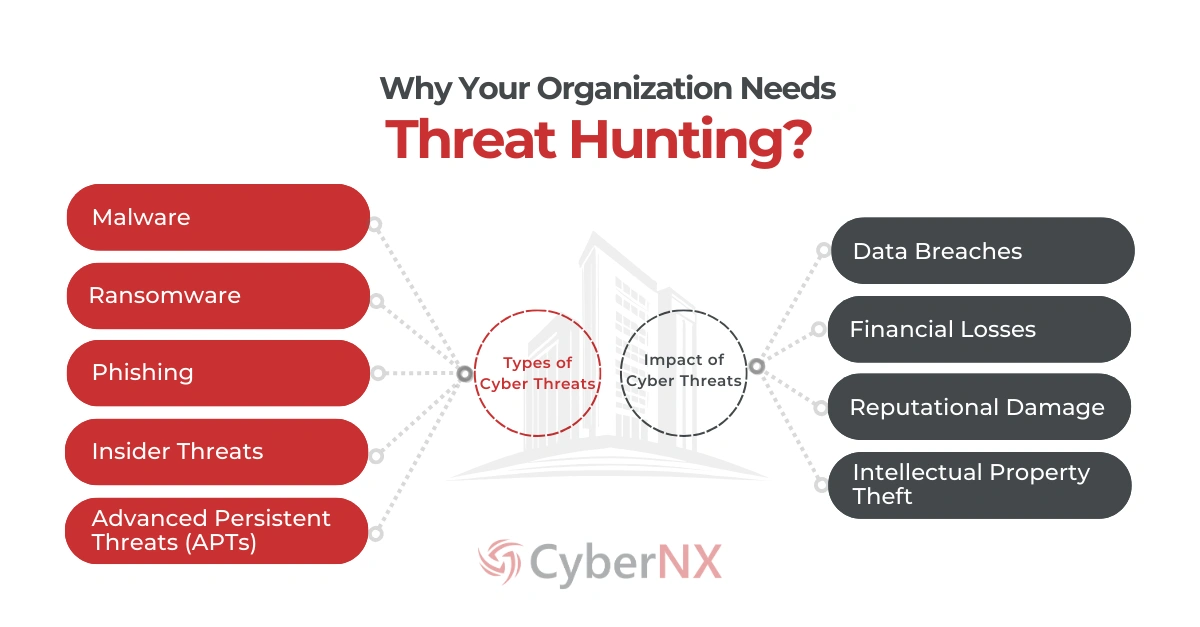
Overview of Cyber Threats
Let’s take a quick look at some of the key players in the cyber threat landscape:
- Malware: This is the broad term for any malicious software designed to damage or disable computer systems. Think viruses, worms, and Trojans – they can corrupt files, steal data, or even give hackers control of your machines.
- Ransomware: This is a particularly nasty type of malware that encrypts your data and then demands a ransom to unlock it. It can cripple businesses and leave them with no choice but to pay up, even though there’s no guarantee of getting their data back.
- Phishing: This is a social engineering attack that tries to trick people into giving up sensitive information, like passwords or credit card numbers. Phishing emails often look like they’re from legitimate companies, making them very convincing.
- Insider Threats: These threats come from within your organization – employees, contractors, or even partners who have access to your systems. They might be malicious, or they might simply make a mistake that opens the door to an attack.
- Advanced Persistent Threats (APTs): These are the most sophisticated threats. They’re carried out by highly skilled attackers who are determined to infiltrate your network and stay hidden for as long as possible. Their goal is often to steal valuable data or intellectual property.
Each of these threats poses unique challenges and requires specific detection and response strategies. That’s why understanding them is the first step in effective implementation of this approach.
Impact of Cyber Threats on Organizations
The impact of cyber threats can be devastating, leading to:
- Data Breaches: Loss of sensitive customer data, intellectual property, and confidential business information.
- Financial Losses: Direct costs associated with incident response, legal fees, regulatory fines, and business disruption.
- Reputation Damage: Loss of customer trust, brand erosion, and negative media coverage.
- Intellectual Property Theft: Stealing valuable trade secrets, research, and development data.
What is Threat Hunting in Cybersecurity?
Threat Hunting is a proactive cybersecurity approach that involves actively searching for hidden threats within a network that have evaded traditional security defenses. Unlike reactive security measures that wait for alerts, this security exercise assumes that a breach has already occurred or is in progress. Its purpose is to uncover these lurking threats before they can inflict significant damage.
Common Challenges Observed in a Threat Hunting Program
Threat hunting isn’t easy. It’s a complex and challenging field, even for seasoned security professionals. Several obstacles can hinder the effectiveness of a this program. Let’s explore some of the key challenges organizations face when implementing and running threat hunting operations.
- Data Overload: Think of finding a needle in a haystack – that’s what sifting through the huge amounts of security data feels like. It takes strong tools and smart processes.
- Skilled Personnel Shortage: Threat hunting needs experts. Finding and keeping skilled cybersecurity pros is tough because there’s a global shortage.
- Evolving Threats: Attackers are constantly developing new and more sophisticated techniques. Threat hunters need to stay ahead of the curve, adapting their methods and tools to keep pace with the ever-changing threat landscape. It’s a continuous learning process.
- Resource Constraints: Threat hunting needs tools, people, and time. Many companies find it hard to give it enough resources, especially when they have other security tasks.
- False Positives: These are alerts that look scary but are actually harmless. Too many false alarms waste time and make it harder to find real threats. It’s important to reduce these to avoid “alert fatigue.”
Why is Cyber Threat Hunting Necessary?
Traditional security measures often rely on signature-based detection and rule-based systems, which can be easily bypassed by sophisticated attackers.
Traditional security systems are reactive – they wait for an alert to be triggered. Threat hunting, on the other hand, is proactive. It assumes that a breach may have already occurred and actively searches for hidden threats.
Signature-based systems can only detect known threats. Modern attackers use techniques like polymorphic malware to evade these defenses. Threat hunting looks for behavior – suspicious activities that might indicate an attack, even if the malware itself is unknown.
The proactive approach thus helps organizations in:
- Faster Detection and Response: Identifying and containing threats earlier, minimizing the impact of an attack.
- Reduced Dwell Time: Drastically shortening the period an attacker remains undetected within the network, limiting the potential damage.
- Improved Security Posture: Uncovering hidden threats and identifying vulnerabilities, strengthening overall defenses and preventing future attacks.
- Enhanced Business Continuity: Minimizing downtime and disruptions to critical operations by detecting and containing threats early.
- Compliance Adherence: Meeting increasing regulatory demands for proactive security practices, as proactive security measures become a compliance requirement in certain industries.
Find Out the Types of Threat Hunting
Understanding the types of threat hunting is key to building a comprehensive and effective program. Let’s explore them:
- Structured Hunting: This is like having a checklist of things to look for. You know what you’re hunting (a specific threat) and use clues (IOCs) to find it.
- Unstructured Hunting: This is like exploring a room without a map. You’re looking for anything unusual or suspicious in the data, even if you don’t know exactly what you’ll find.
- Situational or Entity-Driven: This is like focusing on a specific person or area. You investigate a particular user, system, or asset because you think there’s a higher risk there.
Threat Hunting Methodologies Security Professionals Use
Threat hunting methodology involves a structured approach to searching for threats. Common methodologies include:
- Hypothesis-Driven Hunting: You start with a guess about how an attack might happen and then use data to see if your guess is right.
- Data-Driven Hunting: You start with a guess about how an attack might happen and then use data to see if your guess is right.
- Adversary Simulation and Red Teaming: You pretend to be a hacker and try to break into your own systems to find weaknesses.
- Using Attack Frameworks: You use guides like MITRE ATT&CK to understand how hackers work and find them in your network.
5 Threat Hunting Frameworks
Threat hunting framework provides a structured approach. Key frameworks include:
- MITRE ATT&CK Matrix: A knowledge base of adversary tactics and techniques based on real-world observations.
- Diamond Model of Intrusion Analysis: A framework for analyzing intrusions based on adversary, capability, infrastructure, and victim.
- Cyber Kill Chain: A model that outlines the stages of a cyberattack, from reconnaissance to exfiltration.
- Hunt Framework (SANS Hunting Methodology): A structured approach to threat hunting developed by SANS Institute.
- NIST Cybersecurity Framework: A set of standards, guidelines, and best practices for managing cybersecurity risk.
Threat Hunting vs Threat Intelligence: What’s the Difference?
Threat Hunting vs Threat Intelligence are related but distinct concepts. Threat intelligence provides information about potential threats, including attacker TTPs and motivations. Threat hunting uses this intelligence to proactively search for those threats within the organization’s network. Threat intelligence informs what to hunt for, while threat hunting is the process of actively searching.
Threat Hunting Tools and Platforms
Key tools involved in this exercise include:
- SIEM (Security Information and Event Management) Systems: Collect and analyze security logs from various sources.
- EDR (Endpoint Detection and Response) Tools: Monitor endpoint activity for malicious behavior.
- Threat Intelligence Platforms: Aggregate and analyze threat intelligence feeds.
- Network Traffic Analysis Tools: Detect anomalies in network traffic.
- Custom Scripts and Automation Tools: Automate repetitive threat hunting tasks.
- Log Management Solutions: Centralize log collection and analysis.
Key Phases of Threat Hunting
The threat hunting process typically involves the below discussed steps:
Phase 1: Preparation: Getting ready by setting up tools, gathering intel, and deciding what to hunt for.
- Setting Up Tools and Infrastructure
- Gathering Threat Intelligence Feeds
- Defining Hunt Objectives and Scope
Phase 2: Discovery: Looking through the data for anything unusual, like strange activity or known attack indicators.
- Data Collection and Analysis
- Identifying Anomalies and IOCs
- Exploring New Tactics and Techniques
Phase 3: Investigation: Checking out the suspicious things you found to see if they’re real threats.
- Investigating Potential Threats
- Verifying IOCs and TTPs
- Correlating Findings with Historical Data
Phase 4: Remediation and Mitigation: Fixing the problems you found and taking steps to prevent them from happening again.
- Identifying Root Causes
- Containment and Mitigation Strategies
- Preventive Measures and Recommendations
Phase 5: Post-Hunt Analysis: Writing down what you learned, making things better, and updating your security rules.
- Documentation of Findings
- Feedback and Improvement
- Updating Detection Rules and Playbooks
Industries That Need Threat Hunting
All industries can benefit from threat hunting, but it is particularly critical for organizations in:
- Financial Services
- Healthcare
- Government and Public Sector
- Retail and E-commerce
- Energy and Utilities
- Technology and Software Development
Threat Hunting Exercises
Think of threat hunting as a muscle – it needs regular exercise to stay strong and effective. These exercises are simulated scenarios designed to test and improve your team’s ability to proactively identify and respond to hidden threats. These are crucial for validating your methodologies, familiarizing your team with your tools, and uncovering gaps in your processes.
Why Conduct Threat Hunting Exercises?
- Skill Development: Exercises provide hands-on experience for your threat hunters, allowing them to hone their techniques and learn from simulated scenarios without the pressure of a live attack.
- Process Validation: They help you evaluate the effectiveness of your threat hunting methodologies, workflows, and communication channels.
- Tool Familiarization: Exercises allow your team to become more proficient with the various threat hunting tools and platforms in your arsenal.
- Gap Identification: By simulating different attack scenarios, you can uncover weaknesses in your detection capabilities, data sources, or team coordination.
- Team Building: Collaborative exercises foster better communication and teamwork within your security operations center (SOC).
- Realistic Scenario Testing: You can simulate advanced persistent threats (APTs) and other complex attacks that might not trigger traditional security alerts.
Types of Threat Hunting Exercises
- Tabletop Exercises: These are discussion-based scenarios where the team walks through a hypothetical attack and discusses how they would approach hunting for it. No actual data analysis is involved.
- Walkthrough Exercises: These involve a more practical approach where the team uses real or sanitized data to simulate a hunting scenario, following predefined steps.
- Live-Fire Exercises: These are the most realistic, using a controlled environment to simulate a live attack. The threat hunting team actively searches for the simulated threat in real-time.
- Purple Team Exercises: These involve collaboration between your threat hunting team (Blue Team) and a simulated attacker (Red Team) to identify and remediate vulnerabilities and improve detection capabilities in real-time.
Key Elements of a Successful Threat Hunting Exercise
- Clear Objectives: Define what you want to achieve with each exercise (e.g., test a specific methodology, familiarize the team with a new tool).
- Realistic Scenarios: Base your scenarios on real-world threat intelligence and attack trends relevant to your industry.
- Defined Roles and Responsibilities: Ensure everyone on the team understands their role during the exercise.
- Use of Appropriate Tools and Data: Utilize your actual threat hunting tools and relevant data sources (or sanitized versions).
- Post-Exercise Analysis: Conduct a thorough debriefing to identify lessons learned, areas for improvement, and action items.
- Regular Cadence: Incorporate threat hunting exercises into your regular security operations schedule.
Best Practices for Cyber Threat Hunting: Mastering the Proactive Approach
Effective threat hunting isn’t just about using the right tools; it’s about adopting a strategic and disciplined approach. Here are some best practices to elevate capabilities related to this approach:
- Develop Clear Hypotheses: Start with well-defined hypotheses based on threat intelligence, attack patterns, and observed anomalies. A focused hypothesis makes your hunting efforts more efficient.
- Leverage Threat Intelligence: Stay informed about the latest threats, attacker tactics, techniques, and procedures (TTPs). Integrate threat intelligence feeds into your hunting process to guide your hypotheses and focus your searches.
- Establish Baselines: Understand what “normal” looks like in your environment. Establishing baselines for network traffic, user behavior, and system activity makes it easier to identify deviations that could indicate malicious activity.
- Prioritize Data Sources: Identify and prioritize the data sources that are most likely to contain evidence of malicious activity (e.g., endpoint logs, network traffic, authentication logs). Ensure you have good visibility into these sources.
- Focus on Anomalies: While known IOCs are valuable, don’t overlook subtle anomalies that might not match known signatures. These could be indicators of novel or sophisticated attacks.
- Document Everything: Maintain detailed records of your hunting activities, including hypotheses, data sources analyzed, tools used, findings, and any actions taken. This documentation is crucial for learning and improving your process.
- Automate Where Possible: Identify repetitive tasks in your hunting process that can be automated using scripts or automation tools. This frees up your hunters to focus on more complex analysis.
- Continuously Learn and Adapt: The threat landscape is constantly evolving. Encourage your threat hunters to stay updated on the latest attack trends and techniques through training, conferences, and research.
- Iterate and Refine Your Process: Regularly review your threat hunting methodologies and processes based on the outcomes of your hunts and exercises. Identify areas for improvement and adapt your approach accordingly.
- Integrate with Incident Response: Ensure a seamless handoff between your threat hunting team and your incident response team when a confirmed threat is обнаружен. Clear communication and well-defined escalation paths are essential.
- Use the Right Tools for the Job: Select threat hunting tools that align with your team’s skills, your environment, and your hunting objectives. Ensure your team is properly trained on how to use these tools effectively.
- Embrace a Proactive Mindset: Threat hunting is a proactive endeavor. Encourage your team to think like an attacker and actively seek out hidden threats rather than passively waiting for alerts.
By incorporating threat hunting exercises and adhering to these best practices, you can significantly enhance your organization’s ability to proactively detect and respond to sophisticated cyber threats, ultimately strengthening your overall security posture.
How to Choose the Best Threat Hunting Service Provider for You?
Finding the right threat hunting partner is crucial. Here’s what to consider:
- Assess your security needs and risk profile: What are your biggest vulnerabilities? What kind of data do you need to protect most? A good provider will tailor their services to your specific needs.
- Look for experience and expertise: How long have they been doing this? What kind of threats have they successfully hunted? Ask for case studies and references.
- Evaluate methodologies and tools: Do they use proven methods and cutting-edge tools? Are they familiar with frameworks like MITRE ATT&CK?
- Ensure integration with existing systems: Can their tools integrate with your current security infrastructure (SIEM, EDR, etc.)? Seamless integration is key for efficient threat hunting.
- Consider incident response capabilities: What happens after a threat is found? Can they help you contain the threat and remediate the damage?
- Check data privacy and compliance: How do they handle your sensitive data? Are they compliant with relevant regulations (GDPR, HIPAA, etc.)?
Threat Hunting Metrics and Success Measurement
How do you know if your threat hunting program is working? Here’s how to measure success:
Key Performance Indicators (KPIs) for Threat Hunting:
- Time to Detection: How quickly are you finding threats? Shorter is better.
- Number of IOCs Detected: How many indicators of compromise are you uncovering? This shows how much ground you’re covering.
- Number of Threats Mitigated: How many threats have been successfully neutralized? This is the ultimate measure of success.
Measuring ROI of Threat Hunting: This can be tricky, but consider the cost of not having threat hunting (e.g., the potential cost of a data breach).
Continuous Improvement Using Metrics: Regularly review your KPIs to identify areas for improvement and refine your threat hunting processes.
The Future of Threat Hunting
The field of threat hunting is constantly evolving. Here’s a glimpse into the future:
- AI and Machine Learning in Threat Hunting: AI and machine learning can automate many threat hunting tasks, making it faster and more efficient. They can analyze massive datasets and identify subtle patterns that humans might miss.
- Automating Detection and Threat Analysis (automated threat hunting): This will allow threat hunters to focus on more complex tasks, freeing them from repetitive manual work.
- The Role of Behavioral Analytics: Analyzing user and system behavior to identify anomalies will become increasingly important. This can help detect insider threats and other subtle attacks.
- Advancements in Threat Intelligence Sharing: Better sharing of threat intelligence will allow organizations to stay ahead of emerging threats and collaborate more effectively.
- Evolving Attack Techniques and the Need for Adaptive Threat Hunting: As attackers become more sophisticated, threat hunting must become more adaptive, constantly evolving to meet new challenges. This means continuous learning, refinement of techniques, and a willingness to embrace new technologies.
Conclusion
Cyber security threat hunting is a critical component of a robust security strategy. By proactively searching for hidden threats, organizations can significantly reduce their risk and minimize the impact of cyberattacks. Building or enhancing a threat hunting program is an investment in your organization’s security and resilience. Contact CyberNX Technologies today to learn how we can help you implement a world-class threat hunting program.