Firewalls and Endpoint detection? Yes.
Cloud security? Yes.
24/7 monitoring? Yes.
You have ticked all security boxes and yet one of your biggest risks still answers emails, takes calls and could hold the door open for strangers. Yes, we are talking about your people, your employees.
For CEOs, CTOs and founders leading security-conscious companies, understanding the human element of cybersecurity is important. That’s where social engineering penetration testing steps in. A practical way to test how well your workforce can spot manipulation attempts before they become costly breaches.
This blog explores what social engineering pentesting is, why it matters, how it works, and how you can use it to make your organization more resilient against modern threats.
What Is Social Engineering Penetration Testing?
Social engineering penetration testing simulates real-world attacks that exploit human behaviour rather than technical vulnerabilities. These tests mimic how cybercriminals manipulate employees into revealing sensitive information, clicking malicious links or granting unauthorized access.
Unlike a typical penetration test that targets servers and code, social engineering tests the people behind the systems. The objective is simple but critical: identify where human vulnerabilities exist before an attacker does.
This testing is not just about phishing emails. It can involve pretexting (posing as a trusted entity), baiting (offering something enticing), tailgating (physical intrusion), and more.
Each tactic is designed to test judgment, awareness and adherence to security policies under pressure or deception.
Want to know about other types of Penetration Testing? Check our blog: Types of Penetration Testing: A Complete Overview
Why Social Engineering Penetration Testing Matters: The Commercial Value
Real-World Risk Validation
Even with the best infrastructure, a single mistake by an employee can bypass every digital defence you have built. Social engineering tests help quantify that risk in a way spreadsheets and audits can’t.
Data-Driven Training Decisions
Testing reveals not just if your team falls for an attack, but how and why. This insight helps customise awareness training programs based on actual behaviour, not assumptions.
Regulatory Readiness
Industries under GDPR, HIPAA, or ISO 27001 often require periodic risk assessments including human vulnerabilities. Testing supports compliance without guesswork.
Brand and Reputation Defence
A successful phishing attack can lead to breaches, leaks and public fallout. Proactively identifying social engineering risks keeps you ahead of the crisis.
ROI on Security Spend
You have invested in awareness training. But is it working? Social engineering tests help measure the return by showing what employees actually do under attack conditions.
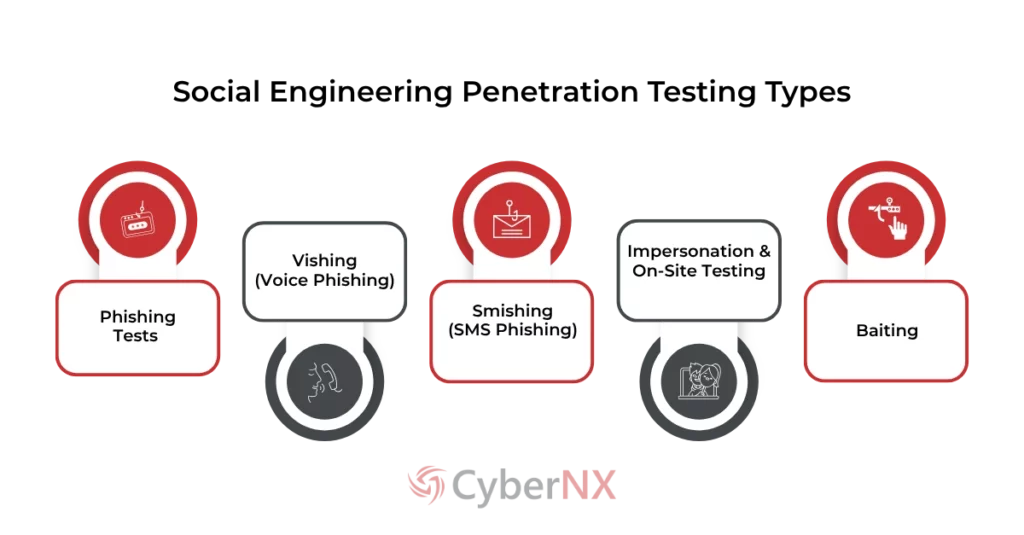
Types of Social Engineering Penetration Testing
Here’s a breakdown of the main forms of social engineering tests used to assess human defences:
Phishing Tests
Simulated email messages that manipulate users into clicking on links, downloading attachments or entering credentials. Common variants include fake login pages and invoice scams.
Vishing (Voice Phishing)
Attackers call employees pretending to be helpdesk staff, partners or executives, aiming to extract passwords or confidential data.
Smishing (SMS Phishing)
A test delivered via text message, often using urgency or impersonation to prompt action.
Impersonation & On-Site Testing
A physical assessment where testers attempt to gain unauthorized access to office spaces by posing as delivery staff, contractors or even employees.
Baiting
Baiting is often carried out by leaving USB drives or other media in public or semi-public areas. When plugged into a company device, they signal a lapse in security awareness.
Each type offers a different lens into how your team responds to manipulation and pressure.
Testing Methods
Social engineering testing typically follows two approaches:
Targeted (Spear) Testing
Focused attacks on specific individuals, roles or departments (e.g., finance, HR or IT admins). These mimic high-value attacks like business email compromise (BEC).
Broad Testing
Company-wide simulations to identify general trends, risky behaviours and departmental vulnerabilities. This is ideal to create baseline awareness throughout the organization.
Most organizations benefit from a hybrid approach: broad tests to set the baseline, followed by targeted campaigns for high-risk roles.
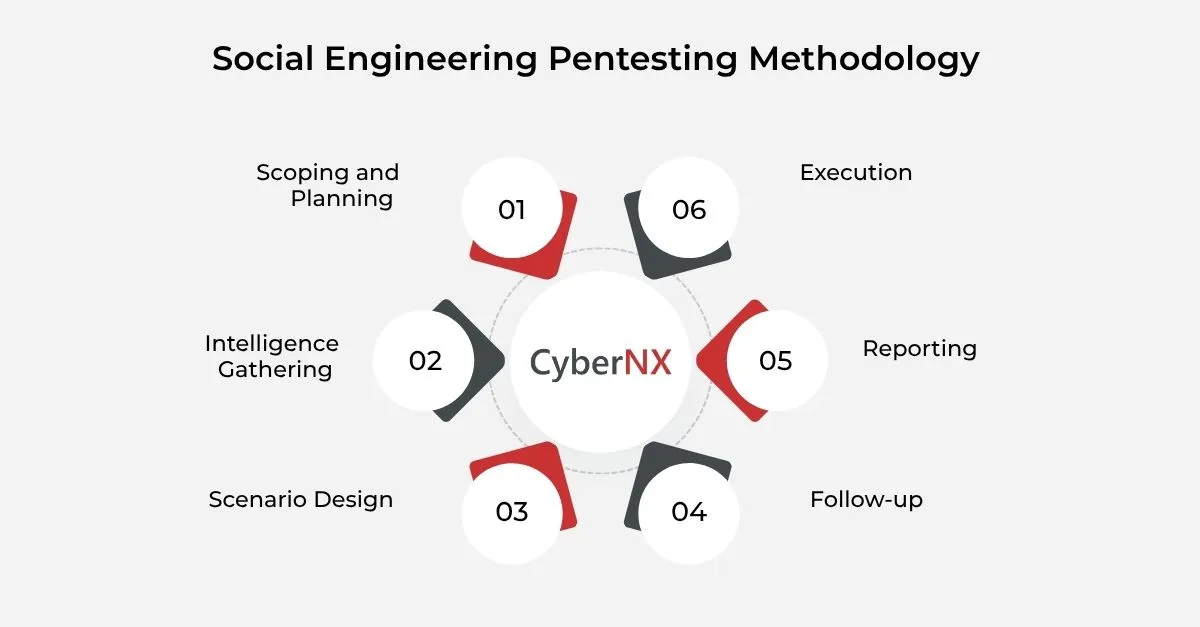
Methodology: How It Works?
Effective social engineering Pen testing is not random or rushed. It’s methodical. Here’s how it’s typically run:
Scoping and Planning
First, define objectives. Are you testing employee awareness, policy adherence or incident response? Determine the scope. Who can be tested, what vectors are allowed and what success looks like.
Intelligence Gathering
Testers perform reconnaissance to learn about your employees and operations. This includes LinkedIn profiles, company websites, third-party vendors and even leaked credentials from previous breaches
Scenario Design
Based on findings, testers create realistic attack scenarios. For example, crafting a phishing email that mimics your internal ticketing system or pretending to be your CFO in a vishing call.
Execution
Attacks are launched under controlled conditions. Testers carefully track employee responses. Did they open the email, click the link, respond to the caller or allow unauthorized entry?
Reporting
You receive a detailed report with:
- What was attempted and why
- Which employees or departments were susceptible
- How quickly users responded or reported incidents
- Actionable recommendations to improve security posture
Follow-Up
Based on results, follow-up tests or focused training may be conducted. The goal is continuous improvement—not blame, but awareness.
Conclusion
Technology will always evolve. But one constant remains: humans are both your greatest asset and most unpredictable vulnerability. Penetration testing social engineering provides a structured, safe way to see how your team performs when faced with manipulation, not in theory but in reality.
For CEOs, CTOs, and founders, this isn’t about testing your employees’ loyalty or intelligence. It’s about testing their preparedness in an increasingly deceptive digital world.
Want to explore how social engineering testing could fit into your security roadmap? Connect with our experts to know more.
Social Engineering Pentesting FAQs
What makes social engineering pen testing different from traditional pen testing?
Traditional tests target systems and code, while social engineering tests focus on human behaviour, simulating real-world manipulation tactics like phishing or impersonation to identify human vulnerabilities.
How often should we conduct social engineering penetration tests?
At least annually, or after major organizational changes. High-risk industries such as finance, healthcare or government may benefit from quarterly testing to maintain strong employee awareness, reinforce vigilance and test incident response procedures.
Can social engineering tests harm employee morale?
Not when done ethically. Professional firms design tests to educate, not embarrass, followed by constructive feedback and tailored training to build a stronger security culture. Transparency and a post-assessment debrief help foster trust and drive engagement in security programs.
Is social engineering penetration testing relevant if we already train employees?
Yes. Training shows intent, but testing shows impact. It verifies whether employees apply their training when faced with real-life deception and helps organizations measure the effectiveness of awareness programs over time.