Cyber threats are no more knocking on the door. Instead, it feels they are barging in, taking many businesses by surprise. To be awake, to be alert and to ace this constant digital battlefield, speed, clarity and precision are the tools your security team needs. A Security Operations Center (SOC) equips you with these, upgrading your defence and taking your security program to the next level.
“So, what happens inside the SOC process?”, would be the obvious question. This blog will take you through the robust process behind every secured system. The process that runs behind the scenes but gives control to security teams to reign over chaos.
What is a SOC?
A Security Operations Center is like a central hub or a mission control room of an organization’s cybersecurity operations. Here, human expertise and technology unify with the aim of monitoring, investigating and responding to security events in real time. There are screens and dashboards of course, but it is the process that act as the digital immune system fighting of cyber diseases, all the time.
A typical SOC team comprise of analysts, engineers and threat hunters; the security warriors who work in shifts, ensuring 24X7 vigilance. Their mission: to detect anomalies, investigate threats, coordinate responses and continuously improve your organizational defence.
What makes this system run effectively is the structured and iterative SOC process.
Related Content: Security Operations Center (SOC): The Brain Behind Modern Cyber Defence
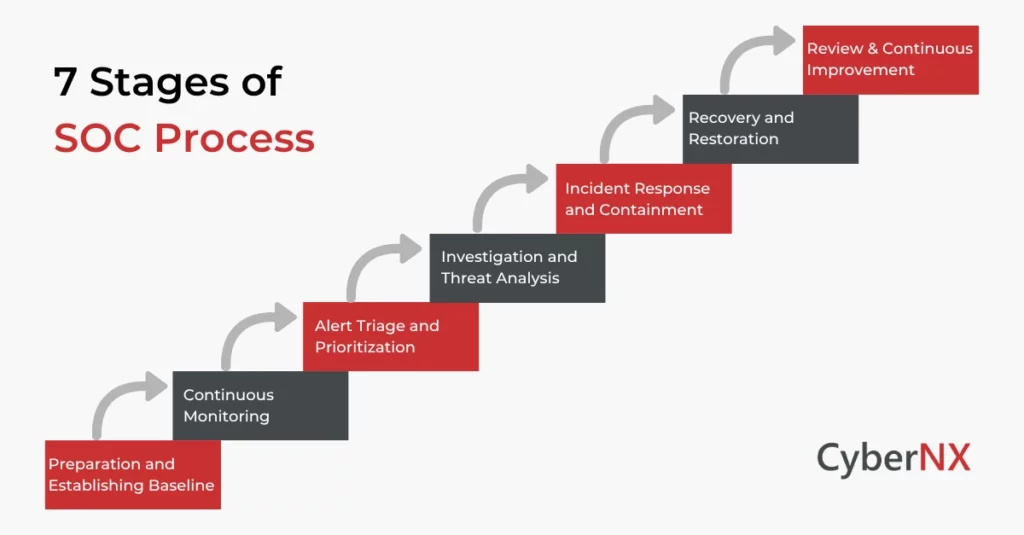
SOC Process Explained in Detail
At the centre of a successful SOC lies a focused and repeatable process. A cycle of detection, investigation, remediation and upgradation. Here’s how it works:
1. Preparation and Establishing Baseline
Before the process starts sounding alerts for the security teams, groundwork is laid by establishing normal user and entity behaviour. What it entails includes collection of logs, identification of critical assets, setting detection rules and configuring tools such as SIEM, EDR and SOAR. Meaningful detection is possible only through baseline.
2. Continuous Monitoring
The second step is continuous monitoring. SOC teams ingest data from multiple sources such as network traffic, endpoint logs, user activity and external, global threat intelligence. The data is fed into a centralized platform where SOC analyst study for signs of any possible malicious behaviour. Proactive monitoring is always on to detect the unexpected.
3. Alert Triage and Prioritization
As soon as some abnormal activity is noticed, alerts are generated. However, not all of them deserve equal attention from the SOC team. Thus, the experts or AI tools review each signal, discard the noise and escalate the real, meaningful threats. The triage phase lets the SOC team differentiate just an anomaly from a possible attack.
4. Investigation and Threat Analysis
Once a threat is flagged, analysts do a deeper investigation through common SOC tools or using AI. Analysts then correlate logs, trace the attacker’s movements, analyse payloads and determine the scope of the security incident. This is a meticulous phase, often aided by forensic tools and threat intelligence platforms.
5. Incident Response and Containment
Time is of the essence in cybersecurity. Once a threat is confirmed, the SOC coordinates a response. What does that mean? It isolates or contains infected systems, revokes credentials, blocks IPs, or executes automated playbooks through SOAR tools. The goal is quick containment, minimal disruption and business continuity.
6. Recovery and Restoration
The recovery and restoration phase of the SOC procedure begins here. Once the threat is neutralized, affected systems are cleaned, patched and restored using different techniques. This is also the stage where business operations resume. But the recovery phase also involves communicating with stakeholders, fulfilling compliance obligations and documenting lessons learned.
7. Review and Continuous Improvement
No incident should end without a review. Therefore, SOC teams do a post-mortem to understand what worked, what didn’t and how defences can be improved. Detection rules are refined and updated, processes re-adjusted and team knowledge expanded.
This rigorous SOC process allows the SOC team to become stronger with every encounter.
Best Practices for an Effective SOC Process
Successful organizations build efficient Security Operations Center (SOC) by cultivating the right mindset and implementing best practices. A SOC functions best when it’s proactive, data-driven and continuously evolving to stay ahead of threats. Here are some best practices that can help your SOC run like a well-oiled machine:
1. Establish Clear Roles and Responsibilities
Ambiguity is the enemy of security. Define what analysts, engineers, and incident responders are responsible for, ensuring everyone knows their lane during routine monitoring and crisis situations alike.
2. Prioritize Threat Intelligence
Real-time, contextual threat intelligence empowers analysts to detect, investigate, and respond faster. Integrating global threat feeds with your SIEM or XDR platform ensures you’re not just reacting – you’re anticipating.
3. Automate Where it Counts
SOC teams face alert fatigue daily. Using SOAR (Security Orchestration, Automation, and Response) tools can automate repetitive tasks, from triaging low-level alerts to initiating response workflows – freeing up analysts for deeper investigations.
4. Foster a Culture of Continuous Improvement
Conduct regular post-incident reviews and purple team exercises to uncover blind spots. Every detection gap should become a lesson learned and an opportunity to strengthen your defences.
5. Align with Frameworks and Regulations
Adopt established frameworks like MITRE ATT&CK, NIST CSF, or ISO 27001 to bring structure and compliance alignment to your SOC operations.
Top 5 SOC Tools and Technologies
A modern SOC thrives on the right blend of technology, automation and intelligence. SOC tools form the backbone of an effective SOC, empowering analysts to detect, analyse, and respond to threats with precision.
1. Security Information and Event Management (SIEM)
SIEM solutions centralize logs from across the organization, correlate security events, and provide real-time visibility into network activities. They are essential for detecting suspicious behaviour, investigating incidents, and ensuring compliance.
2. Extended Detection and Response (XDR)
XDR unifies data across endpoints, networks, cloud environments, and email systems to create a single view of an organization’s threat landscape. It helps analysts identify complex attack patterns and coordinate faster, more effective responses.
3. Security Orchestration, Automation, and Response (SOAR)
SOAR platforms automate repetitive security tasks like alert triage, enrichment, and ticketing. By orchestrating workflows and integrating with other SOC tools, they significantly reduce response times and analyst fatigue.
4. Threat Intelligence Platforms (TIPs)
Threat intelligence platforms aggregate and contextualize data from multiple sources, helping SOC teams stay ahead of emerging threats. They provide actionable insights that guide detection, prevention, and response efforts.
5. Endpoint Detection and Response (EDR)
EDR tools provide deep visibility into endpoint activities, enabling real-time detection of malicious behaviour. They play a crucial role in identifying, isolating, and remediating compromised systems before damage spreads.
Conclusion
The SOC process, involving the sequence of actions discussed, makes cybersecurity resilient. In a world where threats never sleep, this process ensures your defences never blink. Understanding this process is crucial as security shifts from reactive to resilient. Our managed SOC as a service follows a robust SOC process, protecting organizations 24X7X 365. Contact us to know more.
SOC Process FAQs
What tools are commonly used in each stage of the SOC procedure?
SIEM platforms are used for monitoring and correlation. EDR tools aid in endpoint protection. SOAR tools automate response actions. Threat intelligence platforms enrich detection, while case management systems track incidents end to end. Vulnerability Management tools are also used to detect existing flaws and fix them. Read our blog post on SOC tools to know more.
How long does each stage of the SOC process typically take?
Triage can take minutes, while investigations may last hours to days depending on complexity. Incident response is immediate, but recovery and post-mortem reviews can stretch into weeks. The duration depends on threat severity and team maturity.
Can SOC processes be automated?
Yes, especially in triage and response phases. With SOAR tools, playbooks can automatically block IPs, disable users, or trigger containment scripts. However, investigation and context analysis still require human judgment.
Is the SOC process the same for all organizations?
The core stages remain similar, but the depth, speed, and tools used vary by industry, risk profile, and maturity. A fintech SOC may emphasize compliance, while a healthcare SOC focuses on patient data protection.