Most Security Operations Centres evolve unevenly. Tooling advances faster than process. Expectations rise faster than skills. Leadership asks for outcomes the SOC is not yet designed to deliver. This is where a SOC maturity model becomes essential. It provides a shared reference point. It helps leaders and practitioners agree on what “good” looks like at each stage of growth. More importantly, it prevents teams from chasing advanced capabilities before the foundations are ready.
In this blog, we explain the well-known models in practical terms. We compare the five maturity stages side by side and explore widely used frameworks that organisations rely on to shape their SOC strategy.
What a SOC maturity model is and why it matters
A SOC maturity model describes how security operations capabilities develop over time. It reflects how people, processes and technology mature together.
Early-stage SOCs focus on visibility and reaction. Mature SOCs deliver consistency, context and confidence. The model is not a scorecard. It is a planning tool.
For leadership teams, the SOC maturity model removes ambiguity. It sets realistic expectations and helps prioritise investment without overwhelming analysts or budgets.
The five stages of the SOC maturity model
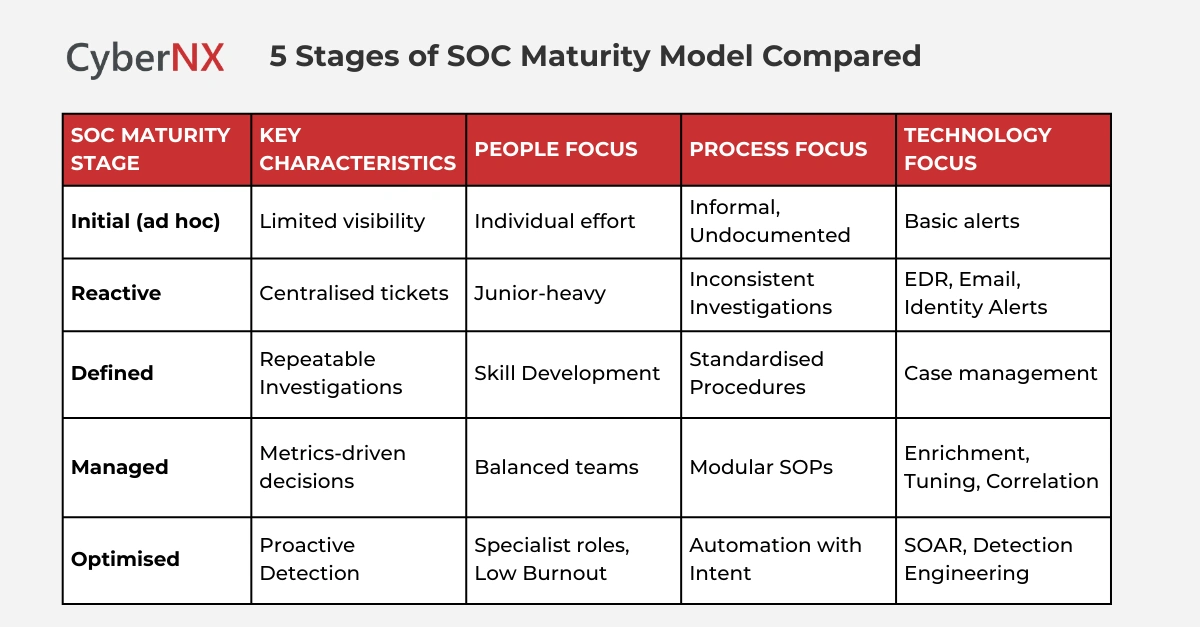
Most industry models converge around five stages. While naming varies, the behaviours are consistent. To answer this once clearly: what are the 5 stages of maturity model? Initial, Reactive, Defined, Managed and Optimised.
Before diving deeper, the table below compares these stages at a glance.
Comparison table: The five stages of the SOC maturity model
This comparison highlights an important point. Maturity is not about more tools. It is about better control and clarity at each step.
Now, let’s see the stage-by-stage view with practical context
1. Initial or ad hoc SOC
This stage often exists before anyone calls it a SOC. Alerts appear. Incidents are handled informally. Knowledge sits with individuals.
The goal here is simple awareness. Trying to optimise too early usually creates confusion.
2. Reactive SOC
At this stage, alerts flow into a central queue. Tickets are opened and closed. Analysts stay busy. However, investigations vary widely. False positives dominate time. Escalation decisions feel subjective. Many teams stall here. The SOC maturity model helps leaders recognise that this is a normal phase, not a permanent failure.
3. Defined SOC
The defined stage brings structure. Investigation steps are documented. Root causes are categorised and metrics start revealing patterns instead of noise. This is where trust begins to form. Leadership sees consistency and analysts see clarity.
4. Managed SOC
Managed SOCs use data to improve outcomes. Metrics guide tuning and training. Escalation rules are clear. Alerts arrive enriched with context. The SOC feels in control rather than reactive. The SOC maturity model becomes a living reference rather than a theoretical chart.
5. Optimised SOC
Optimised SOCs operate with intent. Automation supports analysts instead of replacing judgement. Detections evolve continuously. Intelligence feeds prevention. Importantly, optimised SOCs are calm. Not frantic. They know what matters and why.
Common SOC maturity frameworks organisations use
While the five-stage model provides structure, many organisations align it with established frameworks. Each framework emphasises different outcomes, from process maturity to detection coverage.
The table below compares common frameworks used to enrich a SOC maturity model.
Comparison table: Common SOC maturity frameworks
| FRAMEWORK | PRIMARY FOCUS | HOW IT SUPPORTS SOC MATURITY | BEST SUITED FOR |
| CMMI (Capability Maturity Model Integration) | Organisational process optimisation | Strengthens governance, consistency and repeatability | Process-heavy, regulated environments |
| Gartner’s SOC Model | Threat prediction and prevention | Emphasises automation, analytics and proactive defence | Executive planning and future-state vision |
| HPE SOMM (Security Operations Maturity Model) | Orchestration and risk-based decisions | Evaluates response coordination and prioritisation | SOCs investing in SOAR and orchestration |
| NIST Cybersecurity Framework (CSF) | Risk management lifecycle | Aligns SOC activities with Identify, Protect, Detect, Respond and Recover | Compliance-driven organisations |
| MITRE ATT&CK | Adversary behaviour mapping | Links detections to real-world attack tactics and gaps | Detection engineering and coverage analysis |
Each framework complements the SOC maturity model differently. The key is choosing what aligns with your current stage and business risk.
How frameworks map to SOC maturity stages
Early-stage SOCs benefit most from NIST CSF and basic CMMI concepts. These bring structure and clarity. Mid-stage SOCs gain value from MITRE ATT&CK by improving detection quality and coverage. Advanced SOCs leverage Gartner’s model and HPE SOMM to optimise automation and orchestration. Trying to adopt all frameworks at once often backfires. Maturity improves faster when frameworks are applied intentionally.
How to use the SOC maturity model as a planning tool
Start by identifying behaviours, not tools. Ask where investigations break down. Where time is wasted. Where confidence drops. Then decide what improvement fits your current stage. Training. Documentation. Enrichment. Not everything at once. This approach keeps momentum steady and teams motivated
Conclusion
A SOC maturity model is a guide, not a judgement.
By understanding the five stages and how common frameworks support them, security leaders can plan growth with confidence. Progress becomes visible. Investment decisions become clearer. Analyst trust improves.
At CyberNX, we help organisations assess SOC maturity honestly and build roadmaps that fit their environment. If you want clarity on where your SOC stands and what to focus on next, our SOC services will support you.
SOC maturity model FAQs
Can a SOC operate effectively without following a maturity model?
Yes, but growth becomes reactive and inconsistent without a structured reference.
How long does it take to move between SOC maturity stages?
Most organisations take 12 to 24 months per stage, depending on scope and investment.
Does SOC maturity guarantee better security outcomes?
Maturity improves consistency and confidence, which strongly supports better outcomes.
Should maturity targets differ for small organisations?
Absolutely. The right maturity level depends on business risk and scale.