Faced with ambiguous scope, stretched budgets and evolving threats, many CISOs and IT heads ask: how do we implement a SOC that truly adds value? In this blog, we explain how SOC implementation delivers returns, what challenges are typical, and how you can set up your SOC to support business growth and resilience.
Why SOC implementation matters
Among the many definitions, we believe this one best captures the role of a SOC: According to guidance from the Canadian Centre for Cyber Security, a SOC is responsible for monitoring, detecting, analysing, responding to, and recovering from cyber-incidents.
As you can see a well-executed SOC binds together people, process and technology to deliver continuous monitoring, detection and response. And that’s why it matters for business of all sizes.
Other key benefits:
- Improved visibility across your environment – assets, users, network, cloud.
- Faster detection and response times (metrics such as MTTD, MTTR).
- Better alignment of security with business objectives rather than being seen as a cost-centre.
- A mechanism for continual improvement and adaptation to new threats.
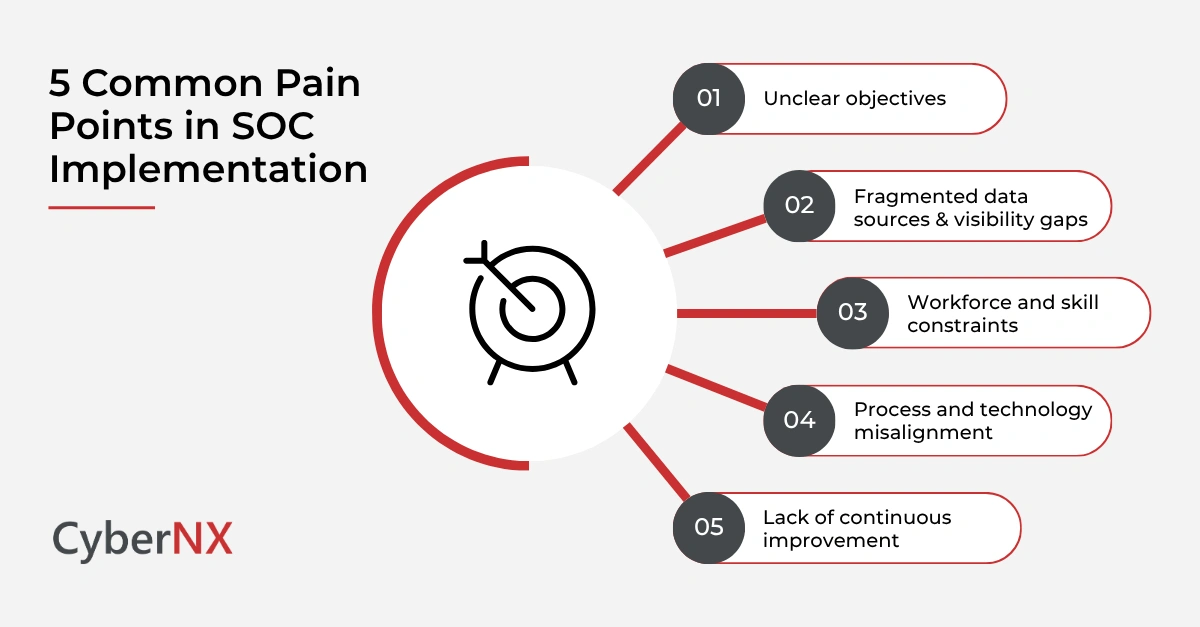
Common pain points in SOC implementation
Sometimes, SOC implementation efforts stall or deliver limited value. Recognising the common pain points helps you avoid them.
1. Unclear objectives
Without clear objectives tied to business goals, a SOC becomes a “security tool” rather than a strategic capability.
2. Fragmented data sources & visibility gaps
A SOC needs data from across on-premises, cloud, endpoints, mobile and OT/ICS. Missing key data sources leaves blind spots.
3. Workforce and skill constraints
A mature SOC demands analysts, engineers, threat hunters. Many organisations underestimate the resource and skill investments required.
4. Process and technology misalignment
Technology alone won’t deliver results. Without a well-defined SOC process and workflows, tools generate alerts that aren’t actionable.
5. Lack of continuous improvement
Threat landscapes shift rapidly. A “set and forget” SOC will quickly lag. Continuous refinement is essential.
A structured approach to SOC implementation
Based on our many years of experience, here is a structured approach to SOC implementation which benefits security programmes.
1. Define scope and strategy
Start with a clear definition of what your SOC should achieve. Align it with business goals such as protecting intellectual property, ensuring customer trust, or enabling regulatory compliance.
Key steps:
- Map your critical assets and threat surface.
- Determine which environments (on-premises, cloud, OT) must be covered.
- Choose measurable objectives (e.g., reduce detection time by X%).
2. Build the People-Process-Technology (PPT) foundation
PPT foundation is key for better and improved efficiency.
- People: Build the team structure: Tier 1 analysts, Tier 2 investigators, Tier 3 threat hunters/forensics. Define roles and responsibilities clearly.
- Process: Define monitoring, escalation, incident response, reporting workflows. Use standard frameworks (e.g., MITRE ATT&CK, NIST Cybersecurity Framework) to guide design.
- Technology: Select tools such as SIEM, UEBA, SOAR, threat intelligence platforms. But remember, tool selection must follow process and people readiness.
3. Deploy incrementally, then scale
Starting small and building iteratively helps reduce risk. Choose a pilot scope covering critical assets, stabilise workflows, then expand coverage. This incremental approach enables learning and refinement.
4. Measure, report and refine
No SOC is complete without metrics. Track meaningful KPIs: mean time to detect (MTTD), mean time to respond (MTTR), false positive rate, vulnerability remediation time. Present dashboards to stakeholders that highlight how SOC operations contribute to business resilience and compliance. Use findings to refine people, processes and tech.
Latest trends shaping SOC
So, what are the latest trends shaping SOC implementation? Find out below:
- AI and machine learning: These help identify anomalies, correlate data and reduce noise.
- Cloud-native SOC models: With more workloads in cloud, SOCs must evolve to monitor cloud-specific environments.
- Managed/SOC-as-a-Service (SOCaaS): Many organisations opt for external expertise to augment or operate SOC.
- Threat hunting and proactive operations: Beyond reacting, SOCs are moving toward hunting latent threats and attacker footholds.
How effective SOC implementation delivers value
When implemented well, your SOC becomes a strategic asset:
- It creates visibility so you can prioritise risk-based decisions.
- It reduces downtime, data loss and regulatory fallout.
- It helps your organisation gain competitive trust by demonstrating mature security operations.
- It enables continuous improvement as threats evolve, so you stay ahead.
Conclusion
Implementing a SOC is not just a technical project – it is a strategic transformation of how your organisation detects, responds to and recovers from security threats. We help you tailor your SOC implementation, so it aligns with your business goals and scales with your growth and keeps pace with changing risks. If you’re ready to implement or optimise your SOC, contact us for a consultation. Our SOC services will help you with a security roadmap that fits your specific business.
SOC implementation FAQs
What size team do I need for a SOC implementation?
The team size depends on your business size, asset profile and monitoring scope. A lean SOC for an SME might operate with a handful of analysts and one manager, while larger enterprises may require full 24/7 coverage, threat hunters, and specialised engineers.
Should we build an in-house SOC or use a managed SOC service?
Both are valid paths. In-house gives you direct control and may fit large organisations with mature security functions. Managed SOC or SOC-as-a-Service can be more cost-effective and faster to launch, especially for organisations with limited internal resources.
How long does SOC implementation typically take?
It depends on scope. A pilot phase (covering key systems) might take 3-6 months, while full rollout (people, process, tech, and continuous improvement) could span 12-24 months.
What are the most important metrics to track for SOC performance?
Focus on: mean time to detect (MTTD), mean time to respond (MTTR), false positive/false negative rates, vulnerability remediation time, and percentage of monitored assets. These give insight into operational effectiveness and risk reduction.