Banks face constant pressure to stay alert. This is because threats keep shifting and regulations tighten each year. Security teams in-charge try their best but still struggle to watch every system in real time. That is why creating a SOC for continuous monitoring as per RBI has become central to cyber resilience.
A strong SOC transforms daily operations. It gives teams clarity, builds trust and improves response. Most importantly, it helps meet RBI expectations in a structured and predictable way.
This blog explains what a compliant SOC looks like, where institutions face challenges and how to build one step by step.
The RBI regulatory backdrop
The Reserve Bank of India expects every regulated entity to build strong cyber oversight. The RBI Master Directions highlights board involvement, continuous surveillance and real-time monitoring. It also stresses audit-log analysis and timely incident reporting.
Continuous monitoring plays a key role here. RBI guidance for cooperative banks notes that a SOC must maintain ongoing surveillance and stay updated with threat intelligence. The message is clear: banks must detect incidents early and respond fast.
This is easier said than done. Many teams still rely on manual checks and others collect logs but do not analyse them effectively. A structured SOC bridges this gap.
What a SOC for continuous monitoring must deliver
A SOC aligned to RBI expectations must function as the centre of daily visibility. It must bring people, tools and processes together. You can find the blueprint for building this level of centralized visibility in our in-depth SOC guide.
1. Real time analysis
Your team should collect logs across servers, applications, databases and network devices. These logs must then be analysed continuously. When patterns shift, the SOC should notice quickly.
2. Threat detection and alerting
Patterns matter and behaviour matters more. The SOC must spot anomalies, detect early signals of compromise and trigger alerts. This includes insider activity, privilege misuse or unusual login patterns.
3. Incident response
Once an alert fires, the SOC coordinates with the response team. Clear playbooks help everyone move with confidence. Containment and recovery follow structured steps.
4. Ongoing improvement
Threats evolve and so should your SOC. Detection rules require regular updates and dashboards need refinement. Capabilities must grow each quarter. This sense of continuous improvement sits at the heart of any compliant programme.
Deploying the right mix of tools is critical to meeting the RBI’s strict requirements for proactive threat detection and 24/7 visibility. Head to our blog on SOC tools to find which can benefit you the most.
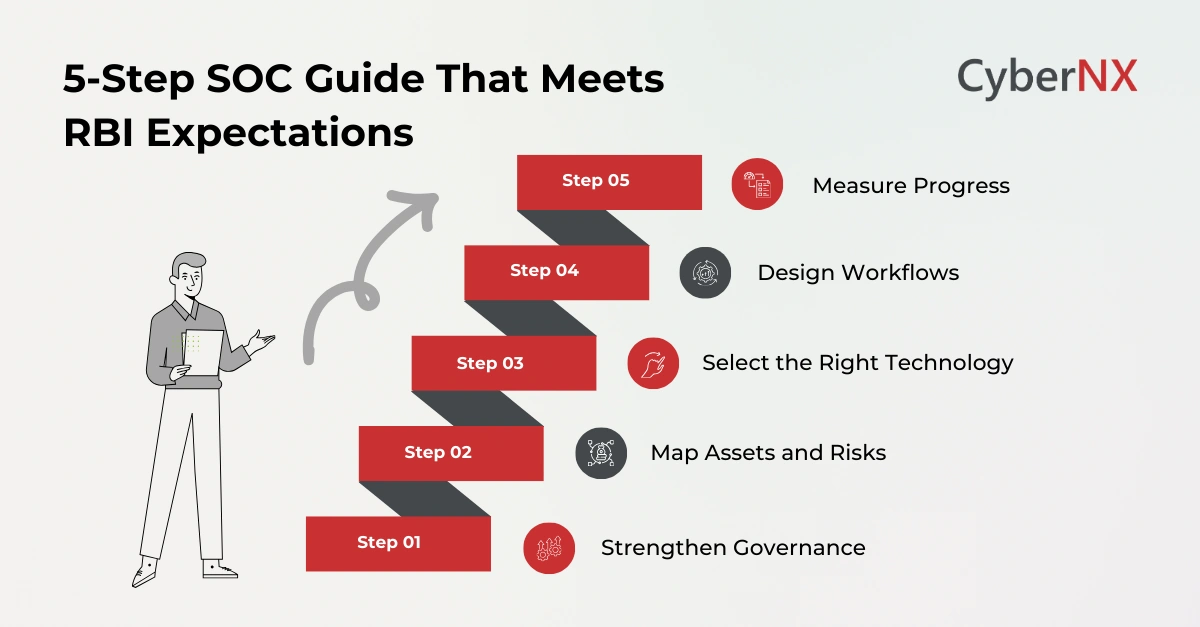
How to build a SOC that meets RBI expectations
Over the years, we have worked with banks of all sizes. We have seen what works and what blocks progress. Here is a simple, practical roadmap.
Step 1: Strengthen governance
Define roles early. Appoint a SOC manager, align with the CISO and set escalation routes. Boards must play an active part. RBI asks for strong oversight. Your governance structure shows that you treat security as a business priority.
Step 2: Map assets and risks
You cannot monitor what you cannot see. Create a clear inventory of:
- Critical applications
- Network devices
- Endpoints
- Databases
- User access patterns
Once the list is ready, define which assets need continuous monitoring. Start small if needed. Grow as you mature.
Step 3: Select the right technology
A SOC needs a solid foundation. Key components include:
- SIEM platform for event aggregation and analytics
- Endpoint detection tools
- Threat intelligence feeds
- Log management and retention
- Dashboards for operations and reporting
RBI highlights the need for surveillance in real time or near real time. The right stack helps you meet this requirement without overburdening your team.
Step 4: Design workflows
Workflows keep teams aligned. Define:
- What triggers an alert
- How analysts escalate
- When incident response begins
- When to report incidents to regulators
- How events are closed and reviewed
Structured workflows reduce confusion during high-pressure situations.
Step 5: Measure progress
SOC maturity does not improve by accident. You need metrics.
Track:
- Mean time to detect
- Mean time to respond
- False positives
- Threat coverage
- Analyst workload
Review these metrics each quarter. Use the results to strengthen detection rules, improve tooling or refine training. Small improvements add up quickly.
Practical benefits for banks
Banks see clear improvements once their SOC matures. Some of the most impactful ones are:
- Better visibility across systems
- Early detection of attacks
- Lower risk of financial and reputational loss
- Faster response and containment
- Stronger regulatory alignment
- Better sleep for teams handling security daily
We often see a shift in culture as well. Teams feel more confident. Business leaders gain clarity, and security becomes part of daily decision-making instead of an afterthought.
Challenges institutions face
Many banks work hard to build a strong SOC. Yet the journey is rarely smooth. We often see a few familiar hurdles. The good news is that each one has a practical way forward.
1. Large volume of alerts
Logs pour in from every system. Teams try to triage everything and end up drained.
A simple shift helps. Focus first on the most critical assets. Tune your rules and use behaviour-based checks to cut down noise.
2. Limited skilled analysts
Skilled SOC analysts are hard to find and even harder to retain. A blended model works well. Pair your in-house team with external specialists. You maintain control while closing skill gaps.
3. Budget pressure
Many smaller banks worry about the cost of a full-scale SOC. You can build gradually and start with essential monitoring. Add new capabilities as you mature and as risks demand it.
4. Rapidly changing threats
Threats keep shifting. Detection rules get outdated quickly. Regular reviews make a big difference. Update rules often, refresh threat intelligence and run short threat-hunting sessions to spot early warning signs.
Trends shaping the future of SOC in banking
Banks are expanding fast, and technology is evolving even faster. Your SOC must prepare for the next phase of digital banking.
- Cloud monitoring: More services now run on hybrid or cloud setups. SOC coverage must extend across them.
- Behavioural analytics: Machine learning-based detection adds deeper insights. These systems spot subtle deviations.
- Monitoring third-party risk: Banks now depend on fintech partners, payment providers and external vendors. SOC visibility must extend into this ecosystem.
- Sector collaboration: Banks benefit from shared threat intelligence. It reduces blind spots and sharpens response.
- OT and cyber-physical monitoring: Branches, ATMs and payment kiosks now use connected systems. The SOC must include these environments as well.
Conclusion
A SOC for continuous monitoring as per RBI helps banks act early, stay compliant and build trust. It creates a layer of protection that grows stronger. We work with teams of all sizes to build SOCs that are practical, scalable and aligned with RBI expectations. If you want to strengthen monitoring across your environment, our RBI Master Direction compliance capabilities will help you throughout the compliance journey. Reach out to us today and we will guide you step by step.
SOC for continuous monitoring as per RBI FAQs
What is the difference between a SOC and a C-SOC in RBI context?
The terms are often used interchangeably. In RBI guidance, “C-SOC” refers to a Cyber Security Operations Centre intended for continuous monitoring, as part of the SOC function. Both focus on detection, analysis, response and improvement.
Does continuous monitoring mean 24/7 staffing of the SOC?
Ideally yes – continuous monitoring means you have monitoring across all hours. For some institutions, this may be achieved via shifts or outsourced support. The key is real-time surveillance of defined critical assets.
What log types should be ingested into the SOC?
Logs from network devices (firewalls, proxies), servers, applications, endpoints, database systems, user access controls, privileged account activities. The RBI baseline controls include “Maintenance, Monitoring and Analysis of Audit Logs”.
How often should SOC processes be reviewed and improved?
SOC processes should be reviewed regularly. At minimum annually for governance review; every quarter for operational KPIs; ongoing for threat rule tuning. Continuous improvement is embedded in the RBI framework.