Security teams today use both SOAR and SIEM tools for effective detection and response operations. Although these acronyms are often mentioned together, they serve different purposes.
SIEM tools gather, analyse and correlate event data from multiple sources for better threat detection. On the other hand, SOAR tools are focused on automation and orchestration of response process, making threat mitigation faster.
Therefore, a better understanding of the SOAR vs SIEM dynamics is essential to use them aptly in your specific IT environment. Find out what they are, how they differ and why using both can dramatically improve the security posture of your organization.
What is SOAR?
SOAR stands for Security Orchestration, Automation and Response. SOAR tools are highly capable of automating and coordinating security operations. It includes most of tasks from incident triage to response actions, and across multiple tools and systems.
Minimizing the need for manual investigation and remediating every alert triggered, SOAR tools use prebuilt playbooks to automate responses and orchestrate workflows. This eventually cuts down response times and ensures consistency in handling incidents.
Related Content: Security Orchestration Automation and Response (SOAR): The Present & Future of Cybersecurity Efficiency
Benefits of SOAR
Here is how organizations benefit from SOAR platforms:
- Faster Response: Pre-built playbooks automate steps like IP blocking, user isolation and ticket creation, enabling quick response.
- Better Efficiency: Reduces alert fatigue massively by eliminating repetitive, time-consuming manual tasks, freeing up SOC teams to do high-value tasks.
- Process Standardization: Ensures standardization across the ecosystem. It means you get the same quality of response every time.
- Contextual Alerts: Enriches alerts with threat intelligence that matters for smarter triage.
What is SIEM?
SIEM stands for Security Information and Event Management. SIEM tools collect and analyse log and event data from across the IT environment. The primary goal of SIEM platform is to detect any abnormal behaviour, anomalies or out of sort events, and generate alerts by correlating them from different sources.
Related Content: Your Definitive Guide to Security Information and Event Management (SIEM)
Benefits of SIEM
Here is how organizations benefit from SIEM tools:
- Centralized Monitoring: Logs from firewalls, servers, endpoints, and cloud systems are aggregated for a unified view. This helps security teams save time.
- Real-Time Alerting: Detects unusual behaviour through pre-defined correlation rules and behavioural analytics, and alerts teams in real time.
- Historical Analysis: Enables security teams to conduct forensic investigations and root-cause analysis.
- Compliance Support: SIEM tools generate audit trails and reports that help meet regulatory mandates.
What is the Difference Between SOAR and SIEM?
The SOAR and SIEM comparison can confuse even the most seasoned IT professionals. This is because both tools are commonly used in the SOC environment, but their functions are fundamentally, as you will see, complementary.
1. Function and Focus
SIEM is primarily focused on threat detection. It collects extensive amount of security data and uses pre-defined, set correlation rules or analytics to discover any suspicious activity in the system. SOAR is focused on the response. It aggregates alerts, often from the SIEM tools, and executes automated workflows to manage and remediate incidents.
2. Alert Management
SIEM tools generate high volume of alerts to halt any kind of suspicious activity. However, many of the alerts can turn out to be false positives. Therefore, these alerts with enrichment and context prove to be useful and actionable. SOAR tools filter, enrich and automate responses based on the alerts by integrating threat intelligence, auto-triaging incidents and performing predefined actions.
3. Automation Capability
SIEM platforms are limited when it comes to automation. Therefore, SIEM tools mostly stop around alert generation and correlation. SOAR is known for automation. From blocking IPs to escalating tickets, SOAR handles everything with minimal human intervention. In the SOAR and SIEM comparison, SOAR is always preferred for reducing manual tasks and enabling 24X7 security coverage.
4. Workflow Orchestration
SIEM typically does not orchestrate actions across systems. It only alerts you that something is wrong. SOAR, on the other hand, coordinates actions between your SIEM, EDR, firewalls, identity platforms and more.
5. Team Impact
SIEM helps analysts investigate by finding threats. SOAR helps analysts by reducing the number of decisions and manual steps they must take. The difference in analyst productivity when comparing SOAR and SIEM can be dramatic, especially in high-volume environments.
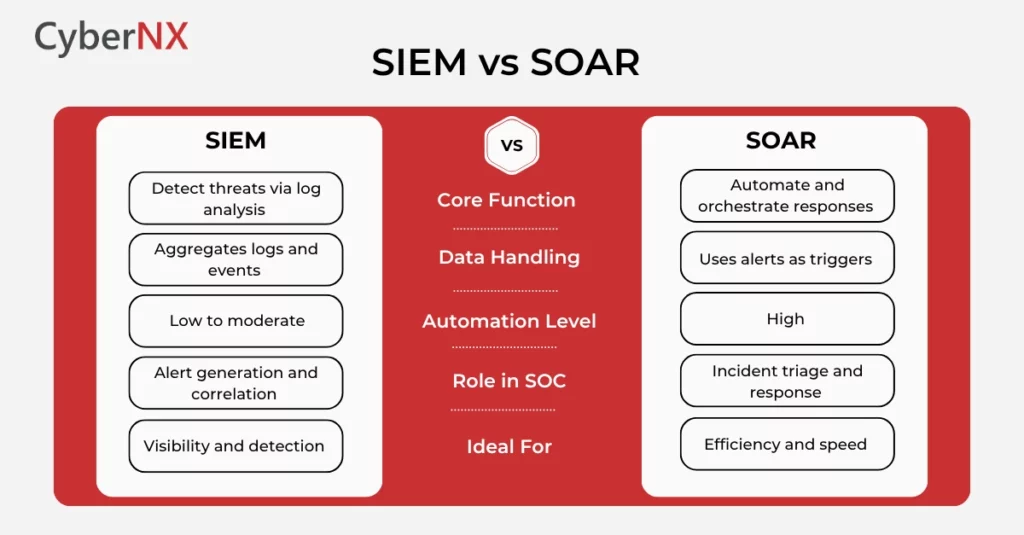
SOAR vs SIEM: Comparison Chart
Here is an easy way to understand the difference between SOAR and SIEM:
This chart simplifies the SOAR vs SIEM comparison into digestible criteria for tech leaders and CISOs alike.
Combining SOAR and SIEM: Better Together
What if you do not have to choose between the two?
Mature SOCs, in fact, combine SIEM and SOAR for end-to-end visibility and action. SIEM tools power detection process; SOAR boosts the response process.
In the SOAR and SIEM equation, it can be said that the sum is greater than its parts. As you can see, together, these tools help you detect, analyse and respond to threats faster and efficiently.
Conclusion
The SOAR vs SIEM debate should be seen from the lens of understanding their roles in the SOC. In the modern threat landscape, combining both the tools give organizations a resilient, proactive defence strategy.
Our SOAR consulting services will help you boost your security efficiency and accelerate incident response. We also provide SIEM consulting services, helping organizations of all sizes manage threat detection and meet compliance. Contact us today.
SOAR vs SIEM FAQs
Is SOAR a replacement for SIEM?
No, SOAR is not a replacement for SIEM – it complements it. While SIEM focuses on collecting and analysing security data to detect threats, SOAR automates the response to those threats. Together, they cover both detection and remediation workflows. Organizations aiming for faster mean time to respond (MTTR) benefit from integrating both tools.
When should a business consider adding SOAR to its SIEM setup?
Businesses should consider adding SOAR when their security teams are overwhelmed by alert volumes, struggling with slow incident response times, or looking to standardize workflows. SOAR becomes critical when scaling a SOC without expanding headcount. It enables security teams to enforce consistent processes and respond 24/7 – even during off-hours.
How does SOAR help reduce analyst burnout in SOCs?
SOAR automates repetitive tasks like triage, ticketing, and initial containment, allowing analysts to focus on high-value investigations. This not only speeds up response but also reduces fatigue from alert overload – one of the top causes of SOC analyst burnout. By handling the “noise,” SOAR helps analysts prioritize real threats. It also boosts morale by removing mundane work and increasing job satisfaction.
Can be small to mid-sized businesses benefit from SOAR and SIEM?
Absolutely. Many modern SOARs and SIEM solutions offer cloud-native, scalable options tailored for SMBs. These tools help smaller security teams operate with enterprise-grade efficiency by automating tasks and centralizing visibility across digital environments. Even without a large SOC, SMBs can use prebuilt playbooks and rules to defend against cyberattacks effectively. Subscription-based pricing models make adoption cost-efficient.