Security teams today face an overwhelming volume of alerts and rising response complexity. SOAR tools take the burden off by offering a structured approach to reduce operational fatigue. Plus, they improve threat containment efficiency, without the need for increasing the headcount.
There are overwhelming number of SOAR platforms available in the cybersecurity market today. But how do you choose the one? To list down the best SOAR tools, we have done thorough research, reviewed customer point of views and talked to countless experts.
What are SOAR Tools?
SOAR stands for Security, Orchestration, Automation and Response. SOAR tools offer a centralized platform where disparate tools within your organization are connected, repeatable & time-consuming workflows are automated and incident handling and response formalized.
The main goal? To reduce Mean Time to Detect and Respond (MTTD/MTTR). These metrics are the key objectives of every SOC team. Plus, it improves analyst productivity and ensures consistency in threat response across the enterprise.
Are SOAR and SOAR tools the same? SOAR is mostly referred to as the practice that helps security teams detect and respond to threats faster and meet compliance. SOAR tools are the software/platforms that makes these practices happen.
Dive deep into the topic with our blog SOAR Guide.
The key benefits of SOAR tools include:
- Faster Incident Response
- Improved Operational Efficiency
- Standardized Workflows
- Increased Threat Visibility
- Less Alert Fatigue
Top 5 SOAR Tools for Enterprise Environments
Here, we have listed five leading SOAR platforms which are designed to streamline incident response, boost analyst productivity and drive operational scale.
1. IBM Security QRadar SOAR
QRadar SOAR platform is suitable for regulated industries. This SOAR tool’s case management and dynamic response playbooks are tailored to compliance-heavy environments. Integrated with IBM’s QRadar SIEM and supporting third-party sources, the tool offers full lifecycle incident management plus audit-ready documentation.
2. Palo Alto Cortex XSOAR
Cortex XSOAR combines orchestration, automation and threat intelligence into a single, extensible platform. It offers more than1000 integrations and unique array of playbooks. The SOAR tool also enables SOC team to automate triage, enrich alerts and coordinate response across teams, resulting in reduced MTTR reduction.
3. Splunk SOAR
Flexible and well-known for seamless integration, this SOAR tool (formerly Phantom) offer rapid task automation and visual playbook design. Splunk SOAR supports real time collaboration and customized workflows across the entire security lifecycle. It is effective in those high-volume environments which are using Splunk SIEM for log analytics and correlation.
4. Swimlane Turbine
Swimlane Turbine offers low-code security automation with broad integration support. Designed for extensibility, it supports use cases beyond the SOC, including DevSecOps and fraud prevention. Its cloud-native architecture ensures scalability, while its API-first approach simplifies integration across modern IT environments.
5. Siemplify by Google Cloud
One of the highlights of Siemplify(now part of Google Cloud) is that it offers low-code automation. It helps SOC analysts to manage playbooks without fussing over programming. Prebuilt playbooks, real time metrics and threat intelligence integration make it a practical option for cloud-native and hybrid organizations.
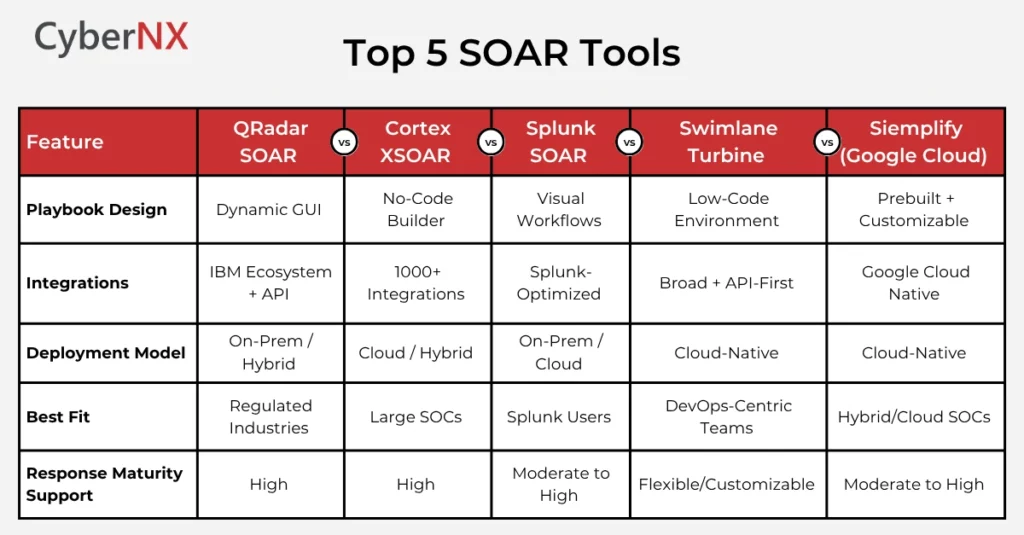
Comparison Chart: 5 Leading SOAR Platforms
A side-by-side breakdown of core capabilities to help you assess SOAR tools according to your operational needs. Look at this chart to compare deployment models, integration depth and suitability for your SOC strategy.
Free and Open-Source SOAR Tool Options
If your organization is exploring customizable, affordable top SOAR tool options, open-source platforms can offer that flexibility. Shuffle is a browser-based SOAR that supports workflow design via Python and RESTful integrations. It is suitable for academic, Research & Development and highly customized environments.
StackStorm is another such tool that offers event-driven automation across security and IT, with a strong community. But it has a steeper learning curve. If you have highly qualified team of security experts, these platforms are handy. They require hands-on configuration but provide full control over the automation pipeline.
How to Choose the Best SOAR Tool
Choosing the right SOAR security tools is essential for organizations aiming to streamline their incident response and strengthen SOC efficiency. The best SOAR security tools unify detection, analysis and response across the IT ecosystem. Here are five key factors to consider when selecting one:
1. Integration Capabilities
Ensure the SOAR platform integrates seamlessly with your SIEM, EDR, and threat intelligence solutions. Integration enables centralized visibility and faster, coordinated threat response.
2. Automation Flexibility
Choose SOAR security tools that offer customizable playbooks and adaptable workflows. This flexibility allows your team to automate repetitive tasks while maintaining control over complex investigations.
3. Ease of Use
A user-friendly interface helps analysts operate efficiently and respond to threats swiftly, even under pressure.
4. Scalability
Your SOAR platform should scale effortlessly with your growing infrastructure, user base, and security needs.
5. Vendor Support & Community
Select a vendor known for strong technical support, continuous innovation, and an active community that shares best practices – ensuring your SOAR tool remains reliable and future-ready.
Conclusion
Choose a SOAR tool that aligns with your security maturity, response velocity and integration ecosystem. No matter what your security objectives are, top SOAR platforms deliver measurable improvements in resilience, speed and security team efficiency.
Our SOAR consultancy services enhance the value of your existing SOAR platform. And if you are building your security from ground up, our expertise and technology will help you strengthen the security posture of your organization. Contact us today!
SOAR Tools FAQs
Does implementing SOAR platform require a fully mature SOC?
Not always. While SOAR platforms are often associated with mature security operations centers, many tools today offer phased or modular adoption paths. Low-code interfaces and prebuilt playbooks enable smaller or mid-tier teams to automate key workflows – like phishing triage or alert correlation – without needing deep development resources. That said, organizations with mature detection capabilities and well-defined processes will extract greater ROI, as SOAR amplifies existing strengths rather than replaces them.
How do SOAR platforms reduce false positives and analyst fatigue?
SOAR tools enhance alert fidelity through automated enrichment and contextual correlation. By integrating with threat intelligence feeds, asset inventories, and user behaviour data, SOAR platforms can assess the credibility of alerts before escalation. Playbooks filter noise, suppress duplicate alerts, and prioritize based on asset criticality. The result is a streamlined queue where analysts engage only with high-value incidents – freeing them from manual triage and reducing alert fatigue over time.
Can SOAR security tools integrate beyond security – into IT, DevOps, or cloud ecosystems?
Yes. Modern SOAR platforms are built to operate across silos. They can trigger workflows in ITSM platforms like ServiceNow, update cloud security groups, or halt deployments in CI/CD pipelines when risks are detected. This cross-functional integration enables security to become proactive rather than reactive – embedding security controls directly into business and operational processes. Organizations pursuing DevSecOps or Zero Trust benefit significantly from this capability.
What is the typical ROI timeline and success criteria for SOAR adoption?
Return on investment typically becomes visible within 3 to 6 months, depending on the complexity of workflows automated and the scale of integration. Success is measured through tangible metrics:
- Mean Time to Respond (MTTR) reduction
- Volume of incidents auto-resolved
- Reduction in repetitive manual tasks
- Improved audit and compliance reporting
Additionally, qualitative indicators – such as analyst satisfaction, reduced onboarding time for new hires, and the ability to scale incident response without additional headcount – contribute to the long-term value SOAR delivers.