SIEM tools have become advanced. It is not just a log management tool. Organizations are no more looking at it solely for compliance requirements. But then cyber incidents are no longer rare, but routine. This has forced security leaders to rethink how they detect, respond and adapt. Security Information and Event Management (SIEM)solutions today act as the core intelligence layer for any modern Security Operations Center (SOC).
But with dozens of good SIEM solutions available, which tool delivers real time threat detection, faster investigation and meets compliance? This blog reveals SIEM tools list of 2026, their advantages, use cases for small businesses and more.
What is SIEM Tool?
Effective and efficient SIEM security tools collect and correlate security data from the entire IT environment such as networks, databases, servers, cloud, IoT devices. This data includes logs, events, alerts and behaviours.
What SIEM tool does best is to present a unified view of the threat landscape to security teams. In addition, it analyses patterns, flags anomalies and enables automated or manual response, according to the predefined rules set.
Modern SIEMs comprising threat intelligence, behaviour analytics and machine learning are quite helpful to detect known and unknow threats, the latter being a game changer for security.
Read our blog SIEM Guide that reveals what, how, what’s next and more.
Why SIEM tool is Necessary for SOC?
Security Operations Center (SOC) consisting of people, process and technology, typically manage the entire security program of an organization. Read our blog SOC Guide which details everything.
SIEM tool has to be the most important one, a must-have tool for a SOC team. This is because SIEM consolidates all the (security data) telemetry, providing a high-fidelity picture of modern threats, reducing false positives and enabling faster incident triage.
It helps SOC in so many ways. The major ones are discussed:
- Makes proactive threat hunting possible
- Ensures real time detection and high priority alerts reach analysts
- Centralized visibility across hybrid environments
- Helps in meeting regulatory compliance requirements with real time reporting
- Empowers teams with digital forensic, enabling them to make appropriate response
Why Do We Need a SIEM Tool?
Previously, compliance was the major reason organizations adopted SIEM tools. But today System Information and Event Management offers strategic reasons and multiple benefits to organizations which are discussed:
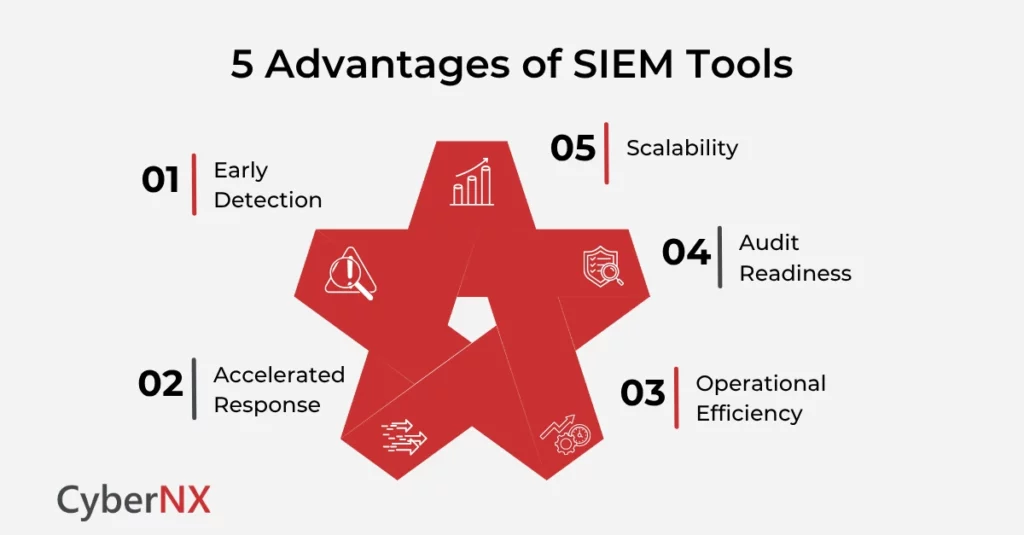
- Early Detection: Early threat detection means preventing your organization from any sort of damage. SIEMs play a big role in that by analysing behavioural trends, spotting lateral movement or privilege abuse early and thus protecting all digital assets.
- Accelerated Response: Now suppose an incident do occur, pre-built playbooks and correlation rules in SIEM platforms help security teams react or respond in minutes instead of hours.
- Operational Efficiency: One of the key factors that drag security teams back is chasing false positives across multiple consoles. SIEM transform this process and streamlines triage into a single workflow, boosting operational efficiency.
- Audit Readiness: SIEM platforms are built in such a way that it simplifies log retention and audit trails, improving documentation. This helps in meeting ISO, HIPAA, PCI-DSS and GDPR standards.
- Scalability: SIEM is continuously evolving. Its scalability helps combat modern and sophisticated threats. One of the prime examples is cloud-native SIEMs which support petabyte-scale ingestion without compromising performance.
Top 5 SIEM Tools in 2026
Now that you know how SIEM tools help SOC and protects organizations, you would want to integrate one of them into your security program. Find best SIEM tools list of 2026, curated by our experts:
1. Elastic Stack (ELK)
Elastic Stack is widely used due to its open-source properties. Therefore, it makes at the top of SIEM tools list. This tool is a good choice for gaining complete control over the SIEM architecture. Scalable and backed by a strong ecosystem, Kibana for visualizations and Beats/Logstash for ingestion, ELK is helpful for cybersecurity firms with engineering capabilities.
It is a good choice for teams looking for customization and budget-conscious tool. Plus, real-time search, anomaly detection and machine learning support are its strengths.
2. Exabeam
On our SIEM tools list, Exabeam finds the second place. This is because it is regarded as a modern SIEM tool with a major focus on behaviour-driven threat detection. It transforms correlation rules with smart timelines and machine learning models. Plus, native SOAR integration powers detection of insider threats, lateral movement and credential abuse.
User and Entity Behaviour Analytics (UEBA), automated investigations and timeline-based detection are its strengths.
3. Rapid7 InsightIDR
Known as InsightIDR, the platform combines EDR and UEBA capabilities. Built for lean security teams, the platform offers detailed contextual insight, reducing complexity. Additionally, the cloud-native architecture, intrusion detection system and pre-built workflows make it an ideal choice for expanding security teams.
Fast deployment and managed detection define this SIEM tool. Built-in threat intelligence, intuitive dashboards and affordable cost for mid-market are its key strengths.
4. Microsoft Azure Sentinel
Azure Sentinel is cloud-native and integrated with Microsoft 365, Defender and Azure workloads. The SIEM tool’s AI and automation capabilities are very strong, and it massively benefits from Microsoft’s global threat intelligence.
This SIEM tool is a clear advantage for enterprises with Microsoft-heavy environments. Additionally, scalability and AI-driven correlation are its strengths.
5. IBM QRadar
QRadar is one of the leaders in the SIEM market. Known for handling massive data volumes and sophisticated threat correlation, it is effective in complex enterprise environments. Therefore, it is widely used in regulated sectors like BFSI and healthcare.
Deep packet inspection, threat intelligence and mature compliance support are this SIEM tool’s major strengths. This tool completes our top SIEM tools list.
What are Open Source SIEM Tools?
Open source SIEM tools are free and available for use in the public domain. They offer flexibility, transparency and cost savings. ELK is one of the most preferred, effective and useful tools, widely used by security professionals. Besides, tools like Wazuh, Security Onion and Apache Metron are also popular.
Organizations with technical expertise and depth can easily use open source SIEMs like ELK that offer unmatched control and extensibility.
There are SIEM tools for small business too which are useful. This includes platforms like LogPoint, Graylog Security, AlienVault OSSIM (now AT&T Cybersecurity), SentryBay SIEM. These solutions provide log collection, correlation, alerting and compliance.
How to Choose the Right SIEM Tool?
Choose a SIEM tool that aligns with your organization’s security objectives. Plus, it will depend on the security maturity, complexity of your infrastructure and compliance obligations you have.
Here’s a table of factors and things to consider before making the decision:
| Factors | Things to Consider |
| Objectives | Define whether your focus is on compliance, threat detection, centralized visibility, or operational efficiency. Choose a tool aligned with your core goals. |
| Scalability & Data Volume | Ensure the SIEM can handle increasing log volumes from cloud, endpoint, and hybrid environments without performance issues. Opt for elastic, cloud-native options. |
| Team Expertise | Match the tool’s complexity to your team’s skill level. Choose a low-maintenance, intuitive SIEM for small teams or customizable platforms for mature SOCs. |
| Integration Support | Check compatibility with your existing stack like firewalls, cloud services, identity platforms, EDRs. API availability and native connectors are key. |
| Detection & Automation | Look for advanced threat detection, UEBA, machine learning and automated response capabilities to reduce alert fatigue and improve reaction time. |
| Total Cost of Ownership | Go beyond license costs. Include data ingestion, storage, support, training and future scaling in your budget analysis. |
| Proof of Concept (PoC) | Test the SIEM in your real environment. Assess usability, alert quality, dashboard clarity and vendor support before making a final decision. |
Conclusion
SIEM tools have matured and there is so much more innovation waiting to happen. Today’s top SIEM tools are more than data aggregators of the past. They are intelligent and responsive systems that enable security teams to achieve multiple objectives at once.
Our SIEM consulting services with rich expertise and advanced technology, provides fast detection capabilities and easy compliance. Contact us today!
SIEM Tools FAQs
Can SIEM tools detect zero-day attacks?
While SIEMs may not detect unknown exploits directly, advanced ones use behaviour analytics and anomaly detection to identify suspicious activity, often the earliest indicator of a zero-day in action.
Are cloud-native SIEMs better than on-premise ones?
Cloud SIEMs offer elastic scalability, faster deployment, and simplified updates, making them ideal for dynamic or growing environments. However, on-premise SIEMs are often preferred in highly regulated sectors where data residency, control, or compliance demands strict on-site data handling.
How often should correlation rules in SIEM tools be updated?
Ideally, correlation rules should be reviewed monthly to ensure they reflect the current threat landscape. Updates should also follow major changes—like new threat intelligence, evolving attack patterns, or internal infrastructure shifts. Regular tuning improves detection accuracy and reduces false positives over time.
What’s the difference between SIEM and XDR?
SIEM is a centralized log analytics tool, while XDR (Extended Detection and Response) unifies telemetry from endpoints, networks, and identities with automated response. SIEM provides visibility; XDR adds action.