SBOMs have become critical for security and crucial for compliance. In a world where software combinations exponentially increase every day, leaders need clear, dependable inventory. Software Bill of Materials is the inventory. But SBOM Standards are the building codes that make that inventory trustworthy, machine-readable and actionable for security teams. Therefore, understanding its nuances, complexities and benefits are important to explore its full potential.
Importance of Software Bill of Materials
An SBOM lists libraries, versions and third-party modules used in a software product. This visibility shortens incident response, exposes licensing risks and helps procurement make risk-aware decisions.
When regulators ask for evidence of supply-chain hygiene, an SBOM is the primary document that shows you have oversight. Industry guidance explains how SBOMs reduce time-to-remediate and improve supply-chain clarity.
Keeping SBOMs up to date is the operational challenge. But it is also the payoff when a vulnerability appears. Organisations that treat SBOMs as part of their release artefacts can reduce mean time to remediation and respond to vendor advisories with confidence.
Find expert perspectives and key takeaways about this topic in our blog SBOM Guide.
What are SBOM Standards and Why it is Important?
A standard defines the required fields of an SBOM (component identifiers, versions, supplier, hashes and dependency relationships). Plus, it shows how those fields are expressed.
Standards enable automated consumption. For instance, an SBOM produced by one tool can be read, analysed and correlated with vulnerability feeds by another. Without shared standards, organisations spend time translating bespoke SBOMs rather than acting on them.
SBOM Standards remove that ambiguity and free security teams to automate detection and remediation.
SBOM Formats: A Deep Dive
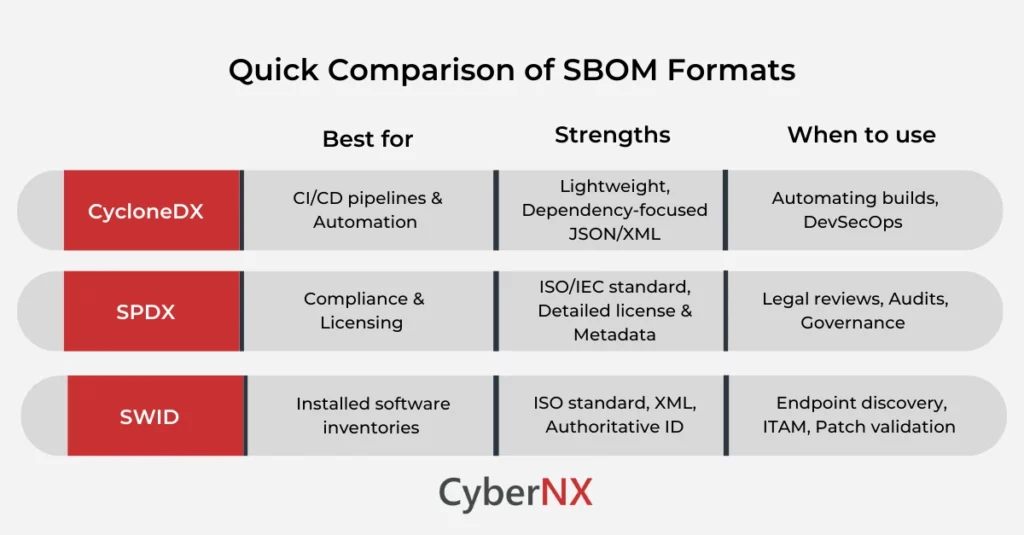
Three formats are integral to modern SBOM programs: CycloneDX, SPDX and SWID. Each was designed with a slightly different use-case and toolchain in mind, so choosing or supporting all three gives you the freedom to meet engineering, security and regulatory needs without translation bottlenecks.
1. CycloneDX
CycloneDX was built for rapid automation in CI/CD pipelines and for security workflows that need compact, machine-friendly BOMs. It has JSON and XML serializations and a focused schema for components. Plus, it has dependencies and explicit fields for vulnerability and component metadata that security tools expect.
CycloneDX is intentionally pragmatic: minimal required fields, strong support for transitive dependency graphs and rich extension points (vEX/VEX, hashes, purl identifiers). These features make it easy to integrate with scanners, registries and pipeline automation. These traits make CycloneDX ideal when your goal is automated scanning, lightweight storage of BOMs in artifact repositories and fast programmatic queries.
Practical notes:
- Typical files: bom.json (CycloneDX JSON) or XML equivalent; spec includes a JSON schema for validation.
- Strengths: compact, CI/CD-friendly, excellent tooling for vulnerability matching and conversion to VEX.
- When to pick it: embed SBOM generation into pipelines, perform automated vulnerability triage and operate a BOM repository for DevSecOps teams.
2. SPDX
SPDX is the heavyweight, standards-backed format focused on legal provenance, license declarations and rich metadata about packages and their relationships.
It is an internationally recognised open standard (ISO/IEC-backed) with a detailed model for license identifiers, copyright statements and granular provenance (who produced what, when, and under which license).
SPDX has multiple serializations (tag/value, RDF, JSON) and a mature ecosystem of converters and compliance tools. If your SBOM objective includes auditability for IP/licensing reviews and cross-project compliance, SPDX is frequently the best fit.
Practical notes:
- Typical files: .spdx.json, .spdx (tag/value) or RDF serializations for integration with semantic tooling.
- Strengths: rich licensing vocabulary (SPDX License List), provable provenance, strong adoption in open-source and enterprise compliance workflows.
- When to pick it: legal/compliance-heavy programs, supplier audits, projects where license clarity and provenance are governance priorities.
3. SWID (ISO/IEC 19770-2)
SWID tags are XML-based identification records defined by ISO/IEC 19770-2 and maintained in tooling and standards bodies (NIST has guidance and validation tooling).
Unlike CycloneDX and SPDX, which represent a bill of components for builds and packages, SWID is focused on identifying installed software instances on devices. This includes product identity, versioning, patch relationships and publisher metadata.
SWID tags are typically bundled with installers or packaged on devices and are invaluable for software asset management (SAM), endpoint inventory and operational discovery. There is also a concise representation (CoSWID) for constrained environments.
Practical notes:
- Typical files: XML SWID tags delivered with software or discovered on endpoints; CoSWID for compact device use.
- Strengths: authoritative installed-software identification for asset management, good for endpoint discovery and lifecycle tracking.
- When to pick it: you need device-level software inventories, patch verification on endpoints, or integration with ITAM/SAM systems.
Interoperability, Conversion and Real-World Choices
In practice, organisations don’t pick a single format and stop there – they use a combination:
- CycloneDX for build-time automation and vulnerability workflows.
- SPDX for compliance and provenance reporting.
- SWID for installed-software inventories and operational asset management.
Most modern toolchains can emit CycloneDX or SPDX and include converters (or libraries) to translate between them. Conversion helps meet partners’ and regulators’ requirements without changing your internal pipelines. That said, conversion is not always lossless: SPDX’s deep licensing/provenance fields may not map perfectly to CycloneDX, and SWID’s installed-instance focus does not correspond one-to-one with build-time component graphs. Treat conversions as pragmatic bridges but retain canonical SBOMs in the format that best serves your primary workflow.
What do SEBI, RBI & CERT-In Recommend for SBOM Standards and Formats?
India’s regulatory landscape has moved quickly. SEBI’s Cybersecurity and Cyber Resilience Framework expects regulated entities to operationalise software supply-chain controls and demonstrate software transparency during audits and incidents. That circular makes SBOM practices a compliance priority for many capital-market participants.
Related Blog: Understanding SBOM Requirement of SEBI CSCRF
CERT-In’s Technical Guidelines provide the technical playbook: SBOMs should be machine-readable, include identifiers such as Package URL (purl) and CPE, and integrate with advisory formats like VEX and CSAF. CERT-In recommends generating SBOMs in CI/CD and updating them with each patch or release so they remain live and actionable rather than static documents.
Related Blog: CERT-In’s SBOM Guidelines Explained
RBI has emphasised cyber-resilience and third-party risk governance; industry reporting and practitioner analysis indicate the central bank expects SBOM-driven inventories as part of technology risk programs. Mapping RBI’s governance focus to the technical guidance from CERT-In and SEBI creates a practical, auditable path for financial organisations.
Related Blog: How to Meet RBI SBOM Compliance
Bringing SBOM Standards into Your Organisation
Operational adoption is straightforward to describe and hard to execute without discipline. Start by embedding SBOM generation in CI/CD so every build produces a signed SBOM artifact. Validate SBOMs automatically, store them in a central repository and link entries to your vulnerability and vendor-risk systems.
Make SBOM delivery and timely updates contractual obligations for critical vendors so your procurement and security functions are aligned. Over time, this turns a compliance artifact into an operational control.
Common Pitfalls and How to Avoid Them
SBOM programs fail when inventories are partial, stale or unsigned. Common failures include missing transitive dependencies, inconsistent formats across teams and a lack of linkage to advisory or exploitability data. Avoid these by treating SBOMs as live artefacts. Generate them in CI, validate and sign them, normalise formats in a central store. Ensure they feed your vulnerability and vendor governance processes.
Practical tool support and clear owner responsibilities make SBOM programs sustainable and auditable over time. Sign SBOMs to protect integrity, and link SBOM entries to VEX/CSAF advisories so you can quickly assess exploitability and required actions.
Conclusion
SBOM Standards are the scaffolding that convert opaque component lists into repeatable, machine-actionable security capability. For CISOs, CTOs and founders: adopt pragmatic formats, automate SBOM generation and validation, and align processes to regulator expectations so transparency becomes resilience. SEBI and CERT-In have already provided operational guidance – use these signals to make SBOMs a living part of your security and procurement lifecycle.
Start today and make software transparency a competitive advantage. Contact our experts today to know how our in-house built SBOM management tool can secure your software supply chain.
SBOM Standards FAQs
What problem do SBOM Standards solve for business leaders?
SBOM Standards remove ambiguity by ensuring every software inventory follows a consistent, machine-readable structure. This makes it easier for CISOs and executives to track risks, meet regulatory expectations, and respond faster to vulnerabilities.
How do CycloneDX, SPDX, and SWID differ in real-world use?
CycloneDX is designed for CI/CD automation, SPDX is rich in licensing and provenance data for compliance, and SWID identifies installed software on devices. Many organisations adopt a hybrid approach to cover all use cases.
Why are regulators like SEBI, RBI, and CERT-In emphasizing SBOM Standards?
These regulators see SBOMs as a way to improve cyber resilience across financial and critical sectors. By mandating or recommending SBOM practices, they ensure organisations can prove software transparency and respond effectively to supply-chain threats.
How should enterprises start implementing SBOM Standards?
Begin implementing SBOM standards with small pilots in CI/CD pipelines to generate CycloneDX SBOMs, add SPDX for compliance artefacts, and integrate SWID into endpoint management. Over time, link SBOM data to vulnerability feeds and vendor risk management for full coverage.