India is a global software exporter and a digital-first nation today. What it means is that software now underpins nearly every critical business in India. From banking platforms, payment systems to government portals and cloud services – all rely on complex software stacks assembled from thousands of components. In this context, SBOM management has become a practical requirement for operational resilience,
supply-chain transparency and for catching up with regulation reality.
We have previously covered in depth about what is SBOM. In this blog, we will look back at the history of SBOM, how a few high-profile incidents, followed by policy action, set the stage for SBOM management. In addition, we try to decode why SBOM matters for Indian organisations and how it is integral to growth, customer trust and innovation.
SBOM history: how a supply-chain crisis created SBOM urgency
The modern SBOM narrative began in earnest after supply-chain compromises exposed how opaque software dependencies could be weaponised. The SolarWinds compromise in 2020 is widely regarded as the inflection point. Attackers modified a trusted vendor’s build and distributed a malicious update, exposing thousands of organisations to risk. The scale and stealth of that attack made clear that knowing what is inside an application is not optional.
That wake-up call led governments and standards bodies to act. In the United States, Executive Order 14028 (May 2021) directed agencies to publish minimum SBOM elements and catalysed work across NIST and NTIA to define formats and use cases. That formalisation transformed SBOMs from an idea into an operational requirement for many purchasers and regulators worldwide.
From transparency to policy: global momentum, Indian response
Once SBOMs were on the regulatory map, other jurisdictions and regulators began aligning. India moved quickly to adapt guidance suited to its context.
CERT-In, under MeitY, published technical guidelines in 2025 that expanded BOM thinking beyond software composition to include contextual models such as QBOM and CBOM for quantum and cryptographic dependencies. CERT-In’s SBOM guidelines encouraged making SBOM creation a routine part of procurement and development, signalling a shift from optional transparency to expected practice.
Financial regulators also raised the stakes. SEBI’s Cybersecurity and Cyber Resilience Framework set expectations for financial firms to manage third-party software risk explicitly. SEBI’s mandates effectively pushed SBOMs into the governance frameworks of capital markets participants.
In short, what began as a security tool for engineers is now a compliance and governance instrument for boards and regulators.
Why SBOM management matters uniquely for India
India’s technology footprint and policy landscape make SBOM management especially consequential.
- India is a software powerhouse. Exports and services continue to scale: recent government and industry figures put India’s IT exports well over the $200 billion mark, with strong growth in FY25. That volume means Indian code ships everywhere, and so do its supply-chain risks.
- India is a digital-first nation. Public services, payments, identity and commerce increasingly rely on complex software stacks that include domestic and imported components. A transparent inventory reduces the mean time to remediate vulnerabilities and protects citizen data.
- Regulatory convergence is accelerating. CERT-In technical guidelines and sectoral frameworks such as SEBI’s CSCRF move SBOMs into procurement, audit and incident response workflows. Organisations that view SBOM management purely as a check-box will fall behind.
The mindset shift: from compliance to security, innovation & trust
Early SBOM conversations focused on standards and formats. Indian boards should now ask a different set of questions: how does SBOM management reduce business risk, accelerate secure innovation and improve customer confidence?
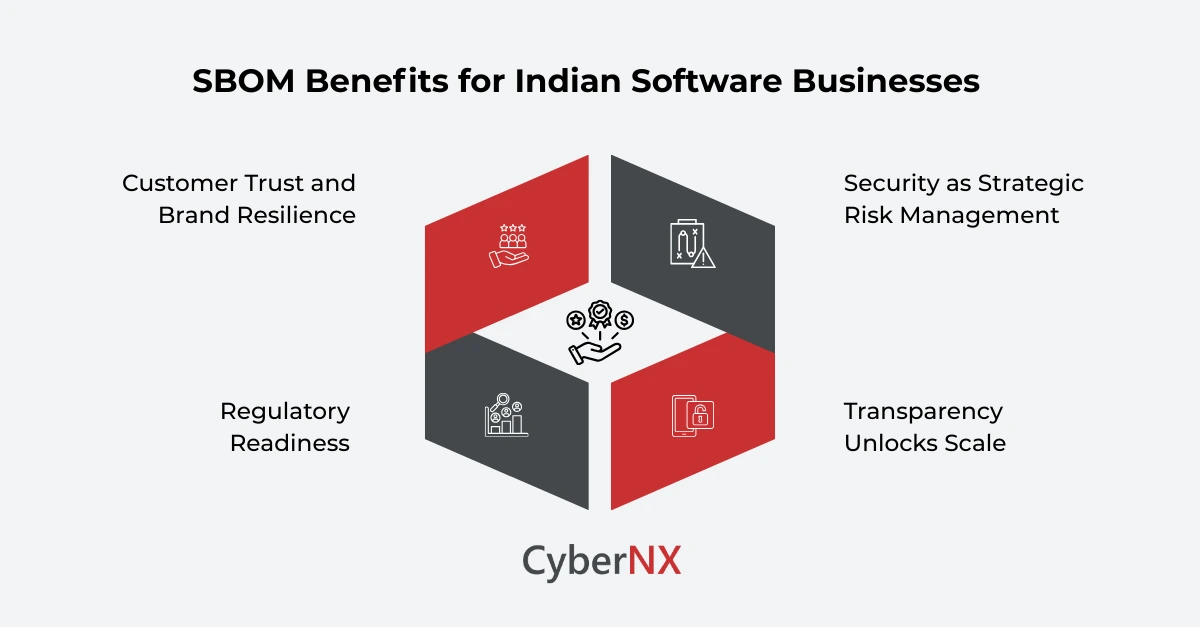
1. Security as strategic risk management
SBOMs shorten the path from vulnerability disclosure to remediation. That speed is invaluable for firms supporting critical infrastructure or processing sensitive data. NTIA and NIST work emphasised this operational benefit early on, and Indian guidance mirrors that emphasis.
2. Transparency unlocks scale
Large teams, multi-vendor supply chains and rapid delivery cycles create friction. A robust SBOM Management programme removes blocking questions (“which systems use this library?”) and enables secure automation – patch prioritisation, impact analysis and vendor accountability.
3. Regulatory readiness becomes market advantage
As regulators codify expectations, companies that bake SBOM Management into engineering and procurement convert a compliance burden into a sales differentiator. For exporters and cloud providers, being able to present verified SBOMs to customers shortens procurement cycles and builds trust.
4. Customer trust and brand resilience
In enterprise procurement, transparency signals reliability. For consumer-facing platforms that manage payments or identity, demonstrable SBOM Management lowers reputational risk after incidents.
Realities and friction points Indian organisations face
Adoption is not friction-free. Common challenges include legacy systems lacking provenance, inconsistent bill-of-material formats across vendors, and skills shortages in automation and software composition analysis.
India has active programmes to address capability gaps: national skilling initiatives and increased MeitY funding for cybersecurity are part of the solution. The public sector’s push for standardised SBOMs is helping create market demand for tooling and services.
How organisations can position SBOM management for business outcomes
We recommend three pragmatic priorities for leaders:
- Treat SBOM management as a product lifecycle capability not a security project. Embed it in procurement contracts, CI/CD pipelines and incident playbooks.
- Invest in automation. Automated SBOM generation, signing and vulnerability correlation turn SBOMs from static records into action. Manual processes do not scale for exporters or large enterprises.
- Use SBOMs to accelerate vendor risk management. Request machine-readable SBOMs in procurement, require attestation for critical components and include SBOM review in supplier onboarding. Ask right questions such as SBOM generation aligned to SEBI’s 9 and CERT-In’s 21 fields.
Conclusion
SBOM management is now an essential element of India’s software ecosystem. What started as a technical remedy to supply-chain opacity has become a lever for national resilience, regulatory alignment and business growth.
Indian organisations that move beyond compliance, focusing on automation, governance and vendor transparency will not only reduce cyber risk but also accelerate secure innovation and build stronger customer trust.
At CyberNX, our SBOM management tool NXRadar operationalise SBOM management, turning policy into practice and compliance into competitive advantage. If you want to translate guidelines into an operational SBOM management programme – from automation to governance and supplier assurance – contact us for a customised assessment and roadmap.
SBOM management FAQs
How does SBOM Management differ from basic inventory tracking?
SBOM Management ties component inventories to provenance, version, licences and vulnerability context so teams can act quickly when a CVE is published.
Will regulators in India mandate SBOMs for all sectors?
Regulators are prioritising critical sectors first. Frameworks like SEBI’s CSCRF and CERT-In guidance signal a phased approach where financial and public services are early focus areas.
Can SBOMs help with open-source license compliance?
Yes. A machine-readable SBOM surfaces license data and helps legal and procurement teams manage obligations more efficiently.
What is the typical ROI for SBOM Management investments?
ROI shows up as faster incident response, reduced remediation cost, shorter procurement cycles and improved customer confidence. Quantifying it depends on breach risk profile and software scale.