Regulated entities (REs) in the Indian securities ecosystem must align with SEBI’s CSCRF and establish a software-supply-chain visibility programme.
A core element of that is the SBOM component inventory: a detailed list of software elements used in critical and business-support systems.
Many organisations feel overwhelmed by both the compliance mandate and the practicalities of exposing all software components. Yet building a robust SBOM component framework can both satisfy audit requirements and provide genuine resilience.
Defining SBOM component
An “SBOM component” refers to a distinct piece of software, library, module or dependency that is part of an application or system. The SBOM (Software Bill of Materials) lists all such components, including transitive dependencies (those pulled in by other components).
Under SEBI’s CSCRF, the idea is to ensure that REs can trace what software they are running, who supplied it, what licences apply, what vulnerabilities may exist and how it links to business-critical processes.
The compliance and resilience link
For cyber audit resilience, knowing your SBOM components means you can:
- Quickly identify which parts of your software stack are exposed when a vulnerability is disclosed.
- Demonstrate to auditors and regulators that you have visibility and control over software-supply-chain risk.
- Support quicker response, containment and recovery when incidents happen.
As one commentary notes: “An SBOM is the foundation for supply chain security management” under CSCRF.
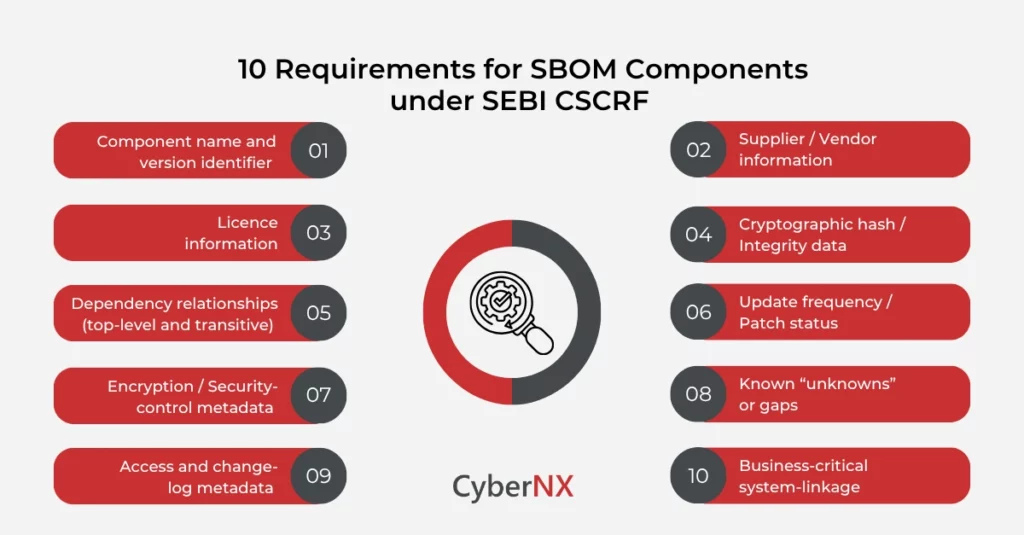
Key requirements for SBOM components under SEBI CSCRF
Here are the major elements (components) that must be captured and managed as per SEBI CSCRF:
1. Component name and version identifier
Every SBOM component must list the exact name, version number (or build identifier) so you know what you are dealing with.
2. Supplier / Vendor information
Who developed or supplied the component (including open-source maintainer vs commercial vendor). This helps trace responsibility and risk.
3. Licence information
What licence governs that component (e.g., open-source licence type) and any usage restrictions. This is highlighted under CSCRF SBOM documentation.
4. Cryptographic hash / integrity data
Hash values (e.g., SHA-256) that uniquely identify the component version, to detect tampering or mismatches.
5. Dependency relationships (top-level and transitive)
It’s not enough to list your direct components. You must map sub-components / libraries that your software depends on (transitive). This gives full visibility.
6. Update frequency / patch status
When was the component last updated? When is next review due? That gives your audit-readiness and shows you are managing change and risk.
7. Encryption / security-control metadata
For components that include cryptography or security controls, the SBOM should include details like encryption method used, access control mechanisms, error-handling.
8. Known “unknowns” or gaps
If you have legacy or proprietary software where components cannot be fully identified, you must document these gaps (known unknowns) and have a mitigation plan.
9. Access and change-log metadata
Who has access to the SBOM? How has it changed over time? Change history is important for audit traceability and for continuous resilience.
10. Business-critical system-linkage
Map each component to the business system or function it supports so you prioritise your remediation and audit-focus. Many REs treat “critical systems” separately under CSCRF.
Implementation steps for building a compliant SBOM component inventory
Our SBOM experts have meticulously studied component inventory. Based on their insight, we list down these implementation steps:
Step 1: Identify your critical systems
Under CSCRF you must classify systems as critical or non-critical. You should start SBOM component mapping with “critical systems.”
Step 2: Inventory software assets and components
Use automated tooling (software composition analysis, SCA) to scan applications and services, identify all components (direct and transitive). Manual processes will struggle at scale.
Step 3: Populate SBOM component metadata
For each component record the data items from the list above: name, version, supplier, licence, hash, dependencies, update status, business relevance.
Step 4: Integrate into SDLC and procurement
Embed component generation into your software delivery pipeline (DevSecOps) and procurement contracts (new software must include SBOM). Under CSCRF new software acquisitions require SBOMs.
Step 5: Maintain and update continuously
Every time your software changes (patching, upgrade, new library), update the component list. Auditors will ask for evidence of currency.
Step 6: Link to vulnerability management and audit-readiness
Once you have SBOM component data, integrate with your vulnerability database so you can quickly identify which components are affected when a new CVE emerges. This supports audit resilience.
Step 7: Documentation and external audit support
Ensure your component inventory and process is well documented. Prepare for cyber audit under CSCRF – demonstrate traceability, governance, change-log, risk-treatment of unknowns.
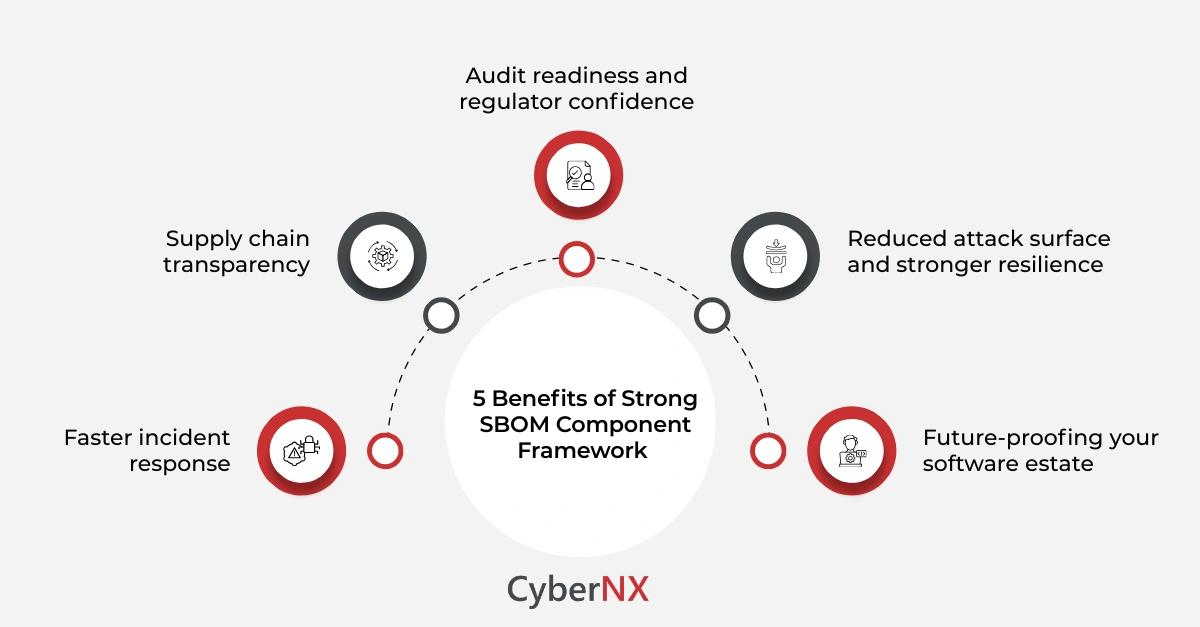
Benefits of a strong SBOM component framework
How does SBOM component framework help your business? Find out:
- Faster incident response: When a component vulnerability is disclosed, you know immediately which applications and systems include it.
- Supply chain transparency: You gain insight into third-party and open-source components and can assess vendor risk more effectively.
- Audit readiness and regulator confidence: Under CSCRF an SBOM component inventory shows that you have thought through component-level risk.
- Reduced attack surface and stronger resilience: By managing components, your organisation is less likely to be blindsided by a hidden vulnerability in a library you didn’t even know existed.
- Future-proofing your software estate: As software supply chains become more complex, having component-level visibility positions you for emerging threats and regulatory changes.
Common pitfalls and how to avoid them
Many organisations face stiff challenges while implementing SBOM generation and end up making mistakes. Here are the major ones we have noted:
- Manual inventories that become stale: Use automation to keep SBOM component data current.
- Ignoring transitive dependencies: Many organisations track only direct libraries – it is the transitive ones that often carry hidden risk.
- Lack of business context: Listing components without linking to business systems reduces usefulness for audit and prioritisation.
- Proprietary/legacy systems untreated: If SBOMs cannot be generated for old systems, ensure you document known unknowns and risk treatment.
- Poor alignment between procurement and SBOM process: If new software is acquired without SBOM component requirements, you introduce blind spots.
What CyberNX does for your business
At CyberNX we recognise that building an SBOM component inventory under CSCRF is not trivial. We adopt a partnership-focused approach: we work alongside your team, not impose a distant “enterprise solution”. Our approach:
- Assess your current state of component coverage and identify gaps.
- Help select and deploy tooling to automate component discovery and SBOM generation.
- Embed component tracking into your SDLC, procurement and change-management processes.
- Create the governance, documentation and audit artefacts to satisfy CSCRF cyber audit resilience requirements. Every step you take strengthens your resilience and positions you ahead of the regulator’s expectations.
Conclusion
The SBOM component inventory is a foundational element in meeting the SEBI CSCRF, providing the visibility, traceability and control required for cyber audit resilience.
While compliance is the initial driver, the real value lies in the strategic capability it gives your organisation to handle supply-chain risk, respond faster, and maintain business continuity.
At CyberNX, we’ve been in the cybersecurity trenches for the past many years. We know that small changes – component-level visibility, consistent updates, linked business-context – can make a big difference.
If you’re a SEBI-regulated entity and want to build an SBOM component practice that meets audit readiness and resilience, talk to us today. In addition, our SBOM management tool provides end-to-end automation and ensures that you get complete visibility into software components.
SBOM component FAQs
Which types of software must have an SBOM component inventory under CSCRF?
All critical and core systems within SEBI-regulated entities must have SBOM component inventories. New software acquisitions for critical business functions must include SBOMs at procurement.
How often should SBOM component inventories be updated?
Every time software is changed (patched, upgraded) the SBOM component list must reflect the change. At a minimum, review frequencies must be defined and implemented.
What do I do if a legacy or proprietary system cannot generate full SBOM component data?
In such cases document the “known unknowns” (components you cannot fully identify), include risk-treatment plans, and obtain board/management approval for the exception.
How does the SBOM component inventory support cyber audits under CSCRF?
It demonstrates to auditors that you have visibility into your software supply-chain, can map components to business systems, track vulnerabilities and maintain change logs. This supports the ‘Withstand’, ‘Contain’, and ‘Recover’ goals of CSCRF.