India’s financial sector is moving towards deeper supply-chain transparency. Banks, NBFCs, exchanges, brokers and fintechs now face growing expectations to maintain clear visibility of what their software contains. Plus, how cryptography is used across systems.
Regulatory bodies like RBI, SEBI and CERT-In have now closely aligned with global practices such as NTIA, CISA and NIST frameworks. Their respective guidelines stress on two key artifacts: Software Bill of Materials (SBOM) and Cryptographic Bill of Materials (CBOM).
The goal of this guide is to provide you with a practical SBOM and CBOM implementation checklist that meets regulatory expectations and strengthens your overall security. It will simplify things for compliance and security teams that often struggle to track components, keep crypto assets updated and prepare for RBI and SEBI audits.
What SBOM and CBOM mean today
Before you build inventories, it helps to understand why these artefacts matter and how regulators expect them to be used.
1. SBOM (Software Bill of Materials)
An SBOM is a full inventory of all software components in an application. This includes packages, libraries, modules and transitive dependencies. SBOMs help teams:
- Spot vulnerable or outdated components
- Track open-source licences
- Speed up response to supply-chain risks
2. CBOM (Cryptographic Bill of Materials)
A CBOM records every cryptographic element used across applications and infrastructure. This covers algorithms, keys, certificates, tokens and HSM assets. CBOMs help teams:
- Detect weak or deprecated algorithms
- Manage crypto lifecycles
- Prepare for post-quantum cryptography
Regulatory context: RBI, SEBI and CERT-In
CERT-In’s Technical Guidelines (Version 2.0, 2025) outline requirements for SBOM, CBOM and other artefacts like HBOM and QBOM.
RBI’s CSITE Advisory (11/2024) asks regulated entities to maintain accurate software and cryptographic inventories and move towards quantum-safe security.
SEBI’s CSCRF explicitly calls for software transparency and verification through SBOM submissions. We see one clear pattern. Regulators expect continuous and verifiable visibility.
The practical SBOM and CBOM implementation checklist (2025-ready)
Build clarity into your software and cloud component inventories with a checklist tailored for SEBI CSCRF expectations. Use it to validate controls, close gaps early and keep your compliance posture audit-ready year-round.
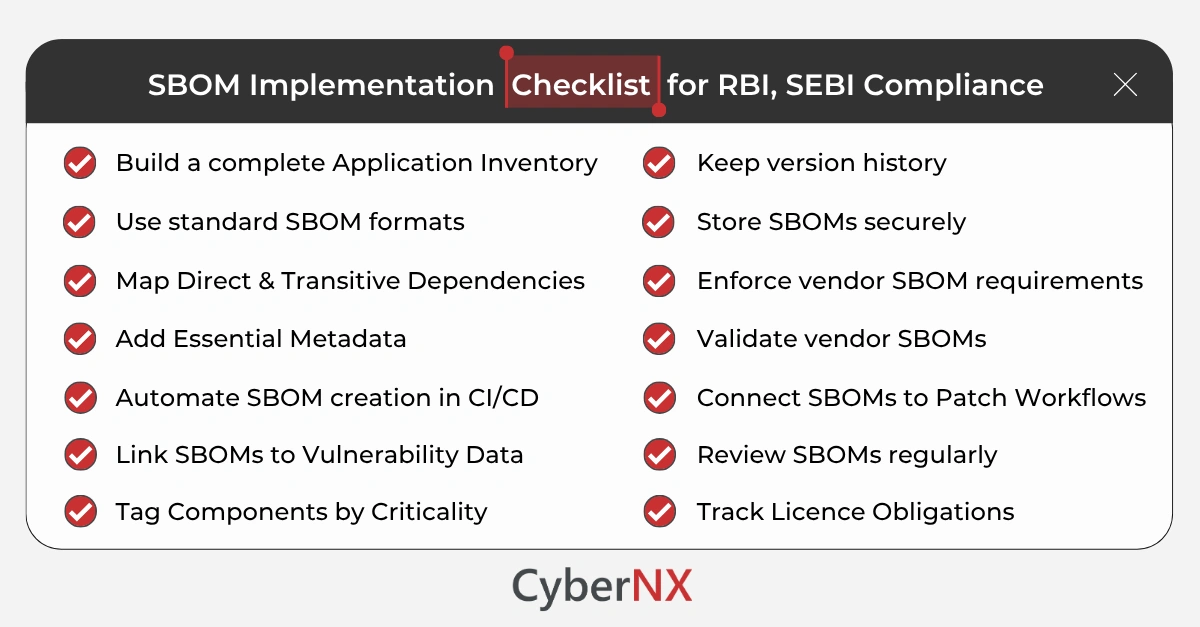
1. SBOM implementation: Strengthen software visibility
Before diving into the technical points, remember this. SBOMs only work when they cover every application in the environment. Therefore, starting small and expanding fast is the way forward.
- Build a complete application inventory: List all in-house apps, vendor systems and SaaS platforms used for regulated operations. This anchors your SBOM scope.
- Use standard SBOM formats: Generate SBOMs in SPDX or CycloneDX formats so they align with CERT-In and NTIA guidance.
- Capture direct and transitive dependencies: Go beyond obvious libraries. Include everything your components rely on. This step uncovers hidden risks.
- Add essential metadata: Document component name, version, supplier, source, checksum and licence type. These fields support audits.
- Automate SBOM creation in CI/CD: Integrate generation into builds and releases. Your SBOMs stay current without manual effort.
- Link SBOMs to vulnerability data: Connect to NVD, OSV or CISA KEV feeds. This helps you detect vulnerabilities as soon as they appear.
- Tag components by criticality: This lets you prioritise patching for components with high business impact.
- Keep version history: Store each SBOM version separately. Auditors often request historical reference.
- Store SBOMs securely: Use an access-controlled repository with integrity checks and backups.
- Enforce SBOM requirements for vendors: Ask vendors to share SBOMs for all third-party apps. Reject opaque binaries.
- Validate vendor SBOMs: Check completeness and accuracy before onboarding systems into production.
- Connect SBOMs to Patch Workflows: Tie SBOM entries to patch workflows. This closes the loop between discovery and remediation.
- Review SBOMs regularly: Regenerate at least quarterly. Also refresh them after major code or dependency changes.
- Track licence obligations: Use SBOM data to validate open-source licence compliance.
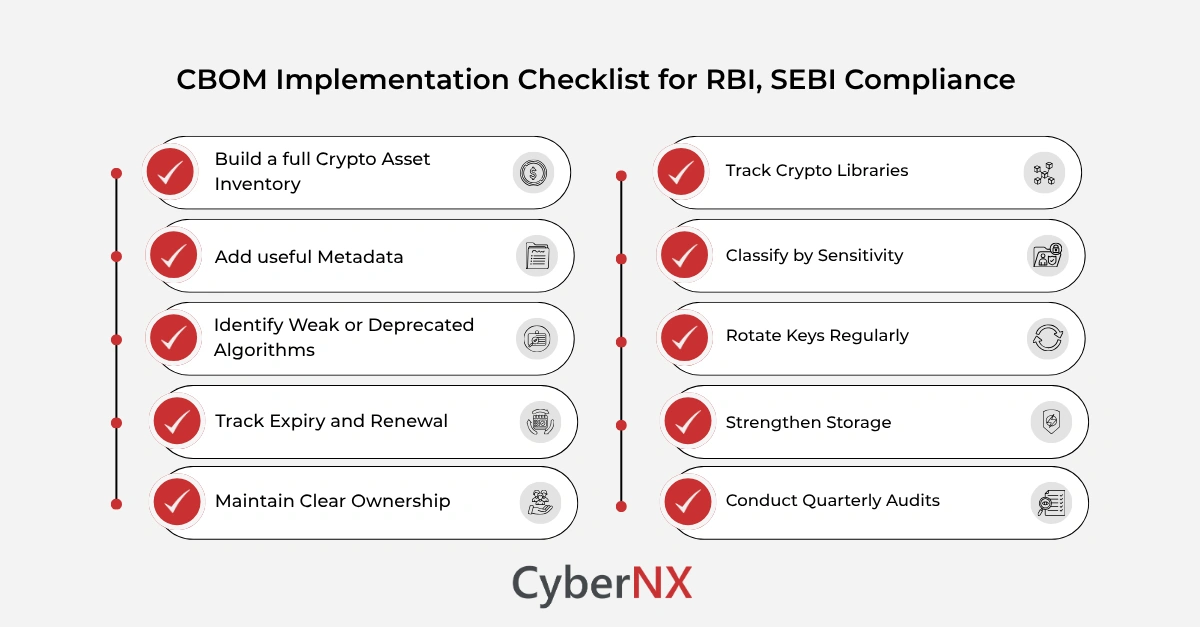
2. CBOM implementation: Strengthen cryptographic governance
Cryptographic visibility is the next major area of regulatory focus. A good CBOM helps teams stay ahead of algorithm-level risks.
- Build a full crypto asset inventory: Cover keys, certificates, algorithms, tokens and HSM assets.
- Add useful metadata: Record type, algorithm, purpose, key length and where each asset lives.
- Identify weak or deprecated algorithms: Flag SHA-1, RSA-1024, 3DES and other outdated standards. Plan replacements early.
- Track expiry and renewal: Set automated alerts for key and certificate expiry.
- Maintain clear ownership: Link each asset to its application or service. This improves traceability.
- Track crypto libraries: Record versions of libraries like OpenSSL, BouncyCastle or libsodium. Outdated libraries often carry hidden risks.
- Classify by sensitivity: Label assets as in-house, vendor-managed or cloud-managed.
- Rotate keys regularly: Record evidence of rotations. Auditors check for this.
- Strengthen storage: Use vaults or HSMs for storage. Document controls clearly.
- Conduct quarterly audits: Reconcile CBOM entries with system configs and certificate stores.
Cryptographic visibility is now as important as vulnerability visibility. Organisations that map their crypto early will transition to post-quantum standards with far less friction.
Conclusion
RBI and SEBI have made software transparency a core expectation. SBOMs and CBOMs are now part of everyday compliance for regulated financial organisations. When you manage these inventories well you improve visibility, reduce supply-chain risk and simplify audits.
We work closely with security and compliance teams to help them automate these processes. Our automation tool NXRadar SBOM management platform generates SBOMs and CBOMs automatically, link them to vulnerability feeds, track lifecycle changes, and present evidence during RBI/SEBI or internal IS audits effortlessly.
If you want support building an SBOM- and CBOM-ready environment, our team is here to help. Every step you take improves resilience and builds trust across your ecosystem.
SBOM and CBOM implementation checklist FAQs
What is the minimum SBOM requirement under CERT-In or NTIA?
A valid SBOM must include component name, version, supplier, dependency relationship, checksum, and license – in a machine-readable format like SPDX or CycloneDX.
Does RBI mandate CBOM for all applications?
RBI’s CSITE Advisory encourages all Regulated Entities (REs) to maintain cryptographic asset inventories and prepare for a quantum-safe environment.
Should vendors supply their SBOMs and CBOMs?
Yes. RBI explicitly advises REs to obtain assurances from third-party vendors on SBOM completeness and timeliness. Contracts should include clauses mandating BOM submission and updates.
How frequently should BOMs be reviewed or updated?
At minimum quarterly, or whenever software updates, patch deployments, or crypto-asset renewals occur.
Are SBOM formats standardized globally?
Yes – SPDX (by the Linux Foundation) and CycloneDX (by OWASP) are internationally recognized. CERT-In and NTIA both recommend these formats for interoperability.
How does CBOM support quantum readiness?
CBOM inventories help identify cryptographic assets using legacy algorithms so organisations can plan early migration to post-quantum cryptographic standards (PQC).
What tools can automate SBOM and CBOM compliance?
Tools like CyberNX’s NXRadar SBOM & CBOM Management Platform can automatically generate, track, and validate BOMs – linking them with vulnerability feeds, audit dashboards, and vendor assurance workflows.