Financial services, without a doubt, is a highly regulated sector today. This is because of the growing concern around cybersecurity. A decade ago, software supply-chain transparency was almost non-existent. Companies investigated third-party libraries or dependencies only for compliance purposes.
But lately, there has been a major shift. Thanks to the Reserve Bank of India (RBI) Master Directions on Information Technology Governance, Risk, Controls and Assurance Practices. Effective from April 2024, it established a strong governance and control regime for banks, NBFCs, and other regulated entities.
As the industry was wrapping its head around that, CERT-In updated Software Bill of Materials (SBOM) Guidelines – Version 2.0 (released in July 2025). It outlined the need for structured inventories of software components throughout the software lifecycle.
In this blog, find out how SBOM Aligned RBI Master Directions on IT Governance and Cybersecurity opens opportunities to enhance transparency, resilience and compliance maturity.
Why governance, risk and software-supply-chain discipline matter
If you are leading cybersecurity in a bank or a fintech company, you already know how software ecosystems are expanding rapidly. There’s third-party integrations, cloud services and open-source components. And you know this is complex because it introduces significant risks too.
When a vulnerability emerges within a software library or component, it can cascade across dependent systems. Without visibility into these relationships, institutions struggle to respond effectively.
In this context, an SBOM makes every application transparent, helping institutions identify inherited risks early. Plus, it helps in maintaining compliance with both CERT-In and RBI expectations.
RBI Master Directions on IT governance, risk, controls, and assurance
The Reserve Bank of India’s Master Directions, issued in November 2023 and kicked in from April 2024, sets out to tighten IT governance and assurance across regulated entities. It pulls together scattered rules into one unified framework for governance, risk, control, and audit. A long time coming, honestly.
1. Scope and applicability
The directions apply to scheduled commercial banks – except regional rural ones – along with small finance and payments banks, NBFCs in the Top, Upper, and Middle Layers, credit information companies, and the big All-India Financial Institutions like EXIM, NABARD, NaBFID, NHB, and SIDBI. That’s a wide net. It makes IT governance consistent across the financial system, pushing everyone to play by the same accountability rules.
2. Key requirements: governance, controls, and assurance
It’s not just paperwork. Entities must set up board-level IT oversight through an IT Strategy Committee, appoint a senior Head of IT, and enforce policies for vendor management, capacity planning, vulnerability testing, and disaster recovery. Business continuity isn’t optional anymore-it’s expected. Independent IS audits for critical systems seal the deal.
3. Implications for the software supply chain
The directions don’t spell out “SBOM,” yet it clearly hints at it. With its focus on vendor and outsourcing risk, visibility into software components becomes unavoidable. SBOM, in many ways, is the missing puzzle piece. It delivers the transparency and control the RBI is hinting at.
What SBOM brings to the table
Though the RBI hasn’t released a dedicated SBOM circular, its recent advisories and inspections increasingly stress SBOM-like practices, particularly for critical infrastructure, vendor oversight, and incident response preparedness.
Delve into our blog How to Meet RBI SBOM Compliance and Strengthen Your Software Supply Chain to know more.
SBOMs turn software management from a guessing game into a structured, measurable process. Instead of a black box, you get clarity-what runs, where it came from, and how safe it is.
1. What is an SBOM?
A Software Bill of Materials is basically a machine-readable list of everything inside a software product-components, libraries, modules. Each entry includes version, supplier, license type, and dependency chain. CERT-In recommends SPDX or CycloneDX for uniformity and easy interoperability.
2. Why financial institutions need SBOM
For banks and NBFCs, SBOMs shine a light on software supply-chain risks. They reveal hidden third-party and open-source parts that might carry vulnerabilities. They speed up incident response too – when something breaks, you instantly know what’s impacted. They also tighten vendor management, weaving transparency right into contracts and audits. On top of that, SBOMs prove regulatory readiness – evidence that the institution actually knows what software runs its systems.
Aligning SBOM practices with the RBI Master Directions
Treating SBOM as a checkbox exercise misses the point. It has to be stitched into governance, risk, and compliance frameworks from top to bottom. Every function – from the boardroom to the audit desk – has a role in making it part of daily operations.
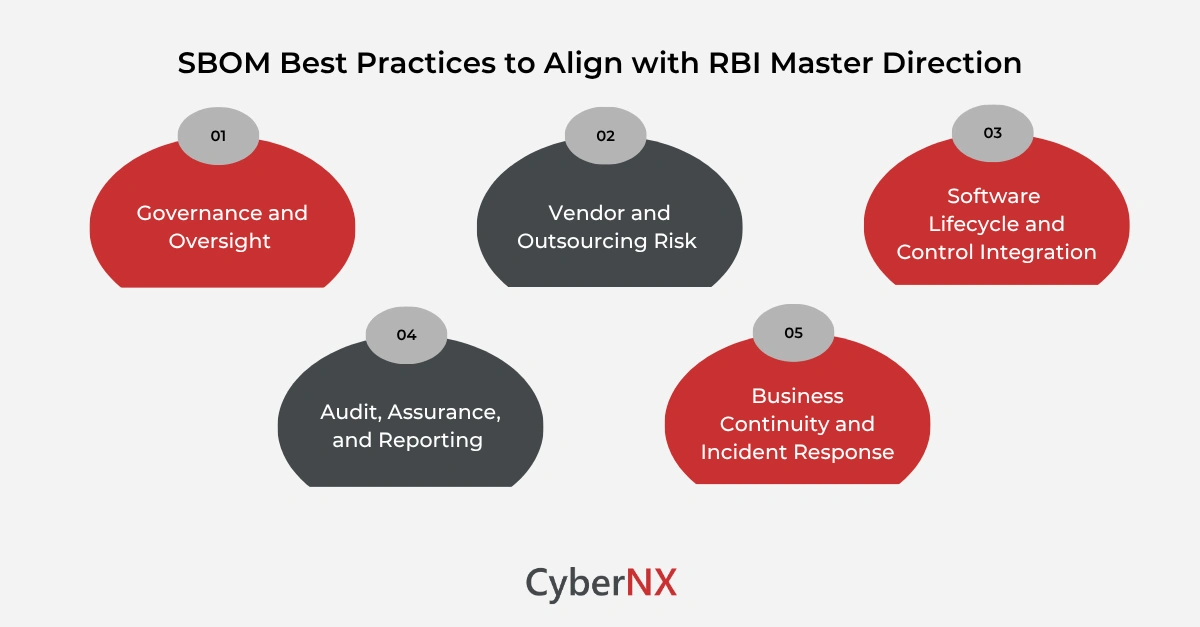
1. Governance and oversight
Boards and senior leaders should see SBOM as a live control tool for managing software supply-chain risk. It belongs in IT strategy reports and governance dashboards. Creating a dedicated Head of Software Supply-Chain Risk can keep oversight from slipping through the cracks.
2. Vendor and outsourcing risk
Contracts must do the heavy lifting. Vendors should be obligated to produce and update SBOMs as part of their deliverables. Continuous monitoring of SBOM compliance then highlights weak spots before they turn into exposures.
3. Software lifecycle and control integration
SBOM generation should start early – right from software design – and continue through deployment. It fits neatly with the vulnerability assessments and penetration tests already required. Keeping it updated ensures change management tracks what’s new or risky in every release.
4. Audit, assurance, and reporting
Auditors, both internal and IS, need to verify the accuracy and completeness of SBOMs. They should check how SBOM data is created, stored, and fed into risk reports. Dashboards showing SBOM coverage can be a strong proof point during RBI inspections or internal reviews.
5. Business continuity and incident response
When a critical vulnerability surfaces, an SBOM lets institutions instantly pinpoint affected applications and vendors. That’s gold during a crisis—targeted patching, faster containment, and less downtime. Embedding SBOM data into incident-response playbooks saves hours of chaos later.
Find additional practical practices our experts recommend for boardroom or an engineering review of SBOM in our blog SBOM Best Practices.
Common pitfalls and how to fix them
Many banks start strong but stumble later. Legacy systems often lack structured component data, and manual SBOM generation is slow and error prone. Automating it with certified tools keeps it current and accurate. Some vendors resist SBOM sharing – tight contracts solve that. The real key is to treat SBOM as a living document that evolves with system updates. Static SBOMs go stale fast.
Key takeaways for decision-makers
SBOM adoption aligns perfectly with the RBI’s goals for governance, control, and assurance. It shifts software visibility from an IT detail to a strategic governance lever. Early adopters will stand out – better compliance posture, reduced exposure, and smoother audits. Partnering with cybersecurity specialists like CyberNX can make rollout painless – embedding SBOMs into development, vendor, and audit workflows without reinventing the wheel.
Conclusion
For financial institutions under the RBI Master Directions, SBOM integration isn’t just smart – it’s necessary. It strengthens governance, sharpens vendor control, and provides verifiable compliance evidence.
At CyberNX, we help organisations assess gaps, deploy in-house SBOM tool automating generation, and embed visibility across the IT governance chain. Talk to our team and see how SBOM adoption can reinforce both compliance and security posture.
SBOM aligned RBI Master Directions on IT governance and cybersecurity FAQs
Does the RBI Master Directions explicitly mandate SBOM generation?
No, it doesn’t mention SBOM directly. However, SBOM aligns perfectly with its goals of vendor management, outsourcing controls, and software governance. It helps institutions gain visibility into dependencies, meet assurance expectations, and strengthen regulatory readiness.
Which SBOM formats are accepted under Indian cybersecurity frameworks?
CERT-In recommends SPDX and CycloneDX as standard formats. SPDX is ideal for license and compliance tracking, while CycloneDX focuses on security and vulnerability management. Both ensure consistent, machine-readable software inventories.
Can financial institutions phase in SBOM adoption?
Yes. Start with critical systems, generate high-level SBOMs, and progressively extend to full dependency mapping and vendor integrations.
How does SBOM improve incident response?
An SBOM enables quick identification of affected systems when vulnerabilities surface, reducing investigation time and enhancing recovery efforts.