Your website is the face of the company where customers get their first impressions about your brand. And therefore, the continuous development and fast release cycles with the help of agile, CI/CD and DevOps. However, security is often pushed into the background in the rush to implement such enhancements.
Threat actors are now turning their attention to web apps to exploit any potential gaps in your security posture. Vulnerabilities are no longer just bugs; they are potential breaches, lawsuits and brand reputation risks.
Because of this, many IT security leaders and DevOps team are seemingly wrestling with a critical question: “Where should we focus our application security testing investments? On Static or Dynamic application security testing?” – the top two appsec solutions. However, our experts believe there is a middle ground that businesses can follow.
What is SAST Used For?
Imagine Static Application Security Testing (SAST) is like examining a blueprint before a building is constructed. In the context of applications, it analyses the source code, bytecode, or binaries of your application to detect vulnerabilities before the software is run.
Also known as white-box testing, SAST provides early-stage visibility into security issues such as code-level flaws, input validation weaknesses, insecure API usage, hardcoded credentials and vulnerabilities like SQL injection and cross-site scripting.
SAST Tools
As for SAST tools, SonarQube must be the most popular one. It balances code quality with security scanning very effectively. Checkmarx is another tool used for deep DevSecOps integration. Then, there is Fortify Static Code Analyzer, which is mainly for enterprise-scale testing.
Veracode Static Analysis is a SaaS-friendly tool for development teams, and CodeQL by GitHub, is a powerful tool for security analysis, used by SAST experts for millions of open-source projects.
Why Choose SAST?
Development teams often use code from open-source libraries, making the software susceptible to unknown and unwanted risks. SAST basically means implementing security into the application. What this does is that it identifies holes in the Software Development Life Cycle (SDLC) very early. Thus, SAST makes the fixing process cost-effective.
Additionally, SAST is known to integrate well with developer workflows, which include IDEs and CI/CD pipelines. It supports the “shift left” security movement. Plus, it helps your business maintain compliance with standards like OWASP Top 10, PCI-DSS and ISO 27001.
Read our blog on Static Application Security Testing (SAST) to know more.
What is DAST Used For?
Dynamic Application Security Testing (DAST) is essentially a modern approach to SAST. But with many more features and benefits. It tests software applications as they run. This means the testing experts mimic the path which a potential cyber attacker would follow. That’s why it is also know as black-box testing because of the same principle used.
However, DAST cannot and does not scan source code like SAST does. Instead, it examines your app during runtime. And it identifies issues such as authentication flaws, broken session management, logic vulnerabilities and common exploits such as cross-site scripting (XSS), CSRF or SSRF.
DAST Tools
OWASP ZAP is definitely at the top of the list when it comes to DAST and SAST tools. It is a community-driven tool, best for small teams. Burp Suite is another trusted, preferred and often used tool by ethical hackers.
Acunetix, blending automated scanning and deep vulnerability insights is also recommended. Our experts also suggest HCL AppScan for enterprise testing and Veracode Dynamic Analysis for integration into CI/CD environments.
Why Choose DAST?
Many IT leaders choose DAST because it shows how the app performs under real-world conditions. Since it is language and tech agnostic, DAST is easy to deploy and provides insights into runtime security gaps without source code access.
Read our blog on Dynamic Application Security Testing (DAST) to know more.
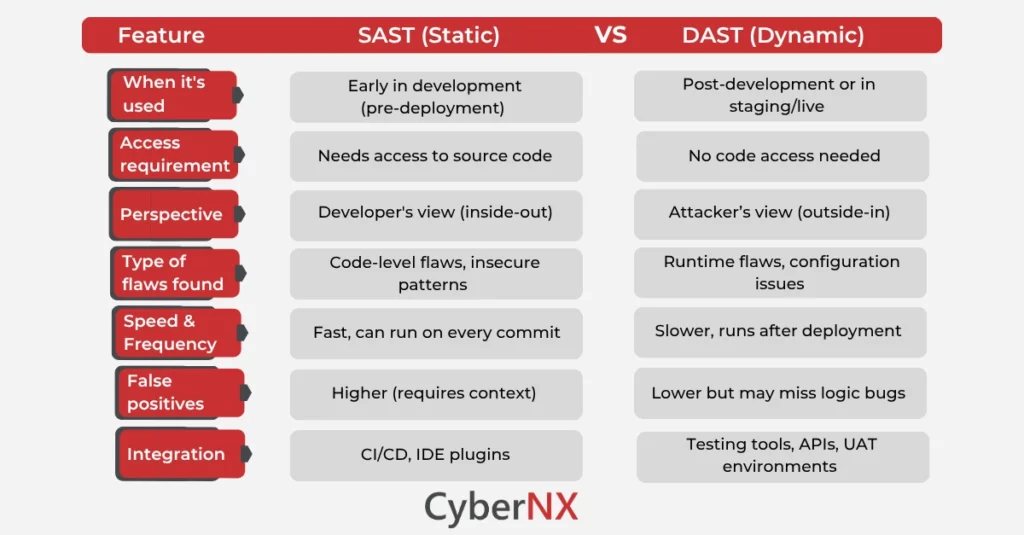
SAST vs DAST: The Key Differences That Matter
What is the difference between SAST and DAST security testing? DAST SAST difference Well, here’s a simple chart of both modern application security approaches across crucial parameters:
What Should Your Business Choose: SAST or DAST?
That completely depends on your development lifecycle, security maturity and perhaps the risk level your business is willing to take based on the position you are in. Here’s what we mean:
Choose SAST if your business is in the stage of considering application security options. In other words, you want something to begin with – like looking to shift security left and catch vulnerabilities before the software is deployed. SAST is effective when the developer team has time for security processes, and you operate in regulated industries like finance, healthcare and government.
On the other hand, choose DAST if your business already has some testing capabilities and what to take it to next level. It is a good choice if you are into testing third-party apps and have no access to source code.
Also, if your business is seriously considering any and every potential vulnerability that bad actors might exploit, choose DAST. Because it replicates the tactics of an attacker and also allows you to validate business logic, error handling and server-side vulnerabilities that might be missed in static analysis.
However, there is a better method, and many businesses are now following it. Adopting a combination of both.
According to the Synopsys’ 2024 State of Software Security report, 68% of enterprises integrate both techniques into their software development lifecycle. This is because SAST and DAST complement each other. While SAST ensures that the code is clean from the ground up, DAST verifies that code deployed behaves securely in practice.
Emerging Trends: From SAST vs DAST to SAST and DAST
The following emerging trends are forcing decision-makers to combine static and dynamic application security testing:
- DevSecOps adoption happening rapidly is pushing IT leaders to embed security into the CI/CD pipeline. SAST and DAST tools are now designed to automate testing from the first commit to production releases.
- Artificial intelligence and machine learning are able to reduce false positives and suggest developer-friendly fixes in real time.
- The shift to cloud-native applications, containers, and microservices also requires tools that can handle complex, distributed environments. Both SAST and DAST tools have evolved to work with Kubernetes, Docker, and serverless stacks, providing broader coverage for modern apps.
- Laws like India’s Digital Personal Data Protection Act (DPDPA), GDPR, and HIPAA require demonstrable secure development practices. SAST and DAST help organizations meet these expectations by providing tangible evidence of secure coding and testing practices.
Conclusion
Ultimately, SAST and DAST should be seen as complementary strategies, where SAST secures your foundation and DAST validates the structure. Used together, they offer end-to-end security visibility plus massively reduces the likelihood of critical vulnerabilities sneaking into production cycle.
If your organization is serious about building trust, improving software quality and reducing time-to-fix, combining both is a great option. Ready to integrate SAST and DAST into your development lifecycle? Explore our SAST and DAST services to see how we can help your business.
SAST vs DAST FAQs
Can SAST or DAST replace manual code reviews and penetration testing?
No, neither SAST nor DAST is a complete replacement for manual code reviews or expert-led penetration testing. While they automate vulnerability detection and improve coverage, manual reviews catch complex business logic flaws, misconfigurations, and novel attack vectors that tools may miss. A layered approach combining automated testing with human expertise yields the most comprehensive security.
How do SAST and DAST impact software delivery timelines?
When implemented properly, both SAST and DAST can actually accelerate software delivery. SAST reduces rework by catching issues early in development, while DAST helps ensure quality before release. However, poor integration or overly strict rules may slow pipelines. The key is to tune thresholds, automate intelligently, and provide actionable feedback that developers can quickly address.
Are open-source SAST and DAST tools reliable for enterprise use?
Yes, many open-source tools like OWASP ZAP (DAST) and CodeQL (SAST) are highly reliable and widely adopted—even by enterprises like Microsoft and GitHub. However, open-source tools often require more configuration, skilled personnel, and integration effort. Enterprises typically supplement them with commercial tools that offer enterprise support, scalability, and reporting.
What role do SAST and DAST play in achieving DevSecOps maturity?
SAST and DAST are foundational to DevSecOps. SAST supports early-stage security by integrating into code commits and developer IDEs, while DAST strengthens runtime assurance during deployment. Together, they promote continuous security testing, foster a secure coding culture, and help organizations move toward automated, scalable, and secure software delivery.