In the ever-growing and innovating digital expanse, invisible cyberwars are being waged against organizations daily. Is your organization fortified or waiting to be breached? Cybersecurity experts continue to see boardrooms ask not “if” but when the next breach will occur, and if they are combat ready to detect, respond and learn from it. Are you one of those IT security leaders, CISOs and CTOs? Time to ponder is now.
Now that we have established the high-stakes premise, you should see security as a discipline, an intelligence loop, a conversation between adversary and defender. That’s where the red team vs blue team vs Purple Team discussions come into play, an integral dynamic of evolving cybersecurity posture.
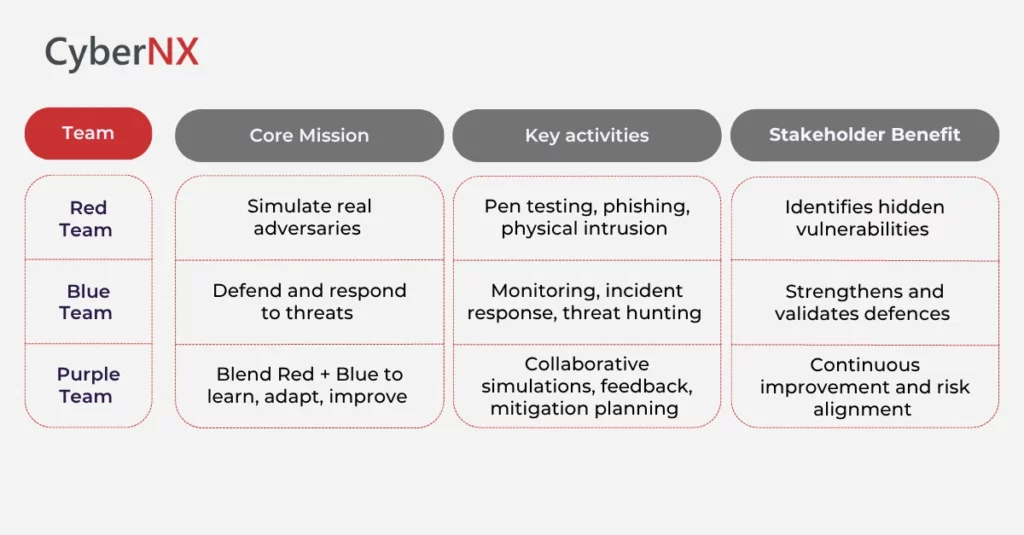
Understanding these Cybersecurity Teams
Understanding the triad of Red, Blue, and Purple Teams is foundational to any mature cyber program. Each team brings a distinct mindset, methodology and mission. And together, they create a full-spectrum defence.
Red Team
Red Team acts as the enemy, a simulated adversary or ethical hackers in the shoes of a real-world threat actor. The red teamers mirror real attack tactics, techniques and procedures, which include social engineering, physical red teaming, phishing and more. They probe your systems, reveal hidden gaps, exploit vulnerabilities and challenge assumptions – revealing the reality of the defence and security posture of your organization.
Related Content: Comprehensive Red Teaming Guide
Blue Team
Blue teams are the opposite of red teams. They are most of the times internal security teams. They are the defenders who monitor, detect, respond and contain threats in real time, across the IT environment. How they do it? By leveraging SIEM, EDR, incident response planning, threat hunting and security operations. Their daily mission is to keep attackers out and service intact.
Related Content: Blue Teaming: The Best Cybersecurity Exercise for Building a Resilient Security Posture
Purple Teaming
Purple is not a standalone unit and let it be clear that they are not a separate team. When the Red team and blue team join forces and discuss, it is known as purple teaming. This collaborative mode enables real-time feedback loops: offensive findings inform defence hardening, and detection outcomes help refine attacker techniques. Its goal: institutional learning, faster hardening and better risk visibility.
Related Content: Purple Team – Bridging the Gap between Red and Blue Teams
Red Team vs Blue Team vs Purple Team: At-a-Glance Comparison
This table distils the core differences into an executive snapshot, helping you see each team’s role and business impact at a glance. Use this as a guide to shape your cyber strategy.
Why This Triangle Matters to Your Organization
Modern threat actors evolve faster than traditional security teams can respond. This triad creates a cycle of simulation, defence, and improvement – transforming security from reactive to resilient.
Where Red reveals, Blue responds, and Purple refines – this structure becomes your continuous readiness engine. For CISOs and CTOs seeking tangible ROI from cybersecurity investments, this is the framework that proves and improves effectiveness.
1. Continuous Resilience
Red engagements are powerful-until you repeat them. Without Blue integration, lessons fade. Purple Teaming institutionalises improvement through iterative cycles of attack, learn and defend.
2. Alignment Beyond Silos
When Red and Blue operate in isolation, reports may be too technical or too vague. A Purple approach aligns the insights across IT, risk, compliance, and executive leadership, translating findings into strategic action and ROI.
3. Preparation for Tomorrow’s Threats
LLMs and generative AI are reshaping both attack and defence. Red Teams can now emulate AI powered spear phishing or exploit generation. Blue Teams may deploy AI for threat intelligence or root cause analysis, unearthing trends faster. Purple structures ensure these AI driven advancements feed into both offensive simulations and defensive tuning.
Making It Work: Best Practices for Executives
Strategic implementation isn’t about deploying three siloed teams. It’s about creating deliberate feedback loops, allocating resources wisely, and making collaboration a discipline, not an afterthought.
Consider starting with regular Purple Teaming exercises tied to your threat model. Use automated tools where possible. And most importantly, ensure your board understands the KPIs these team’s impact: risk reduction, MTTR, and detection efficacy.
- Reduces Gossip, Increases Governance: Don’t treat Purple Teaming as a perpetual “new team.” Instead, charter it as a project or role-often run by security architects or IR leaders-to mediate communications, document remediation, and validate fixes.
- Automate with Set Goals: Breach and Attack Simulation (BAS) platforms empower these cybersecurity teams. How? Scaling the testing process for Red teams, automating validation for blue team and presenting unified dashboards for purple teams. Integrating BAS strengthens alignment, reduces manpower gaps and improves detection-to-fix cycles.
Conclusion
Red, Blue, Purple – they are reflections of how your organisation views risk, readiness and learning. A Red only approach feels adversarial. Blue only feels reactive. Purple first feels strategic. When your cyber journey is in the collaborative mode, you unlock ROI on security people, processes and tools.
Strong security comes from clear testing, reliable defence and smooth collaboration. Our red team, blue team, and purple team services give you that balance. We work closely with your team to strengthen controls, tune detections and validate your readiness. Contact us today to explore how we can support your security goals.
Red Team vs Blue Team vs Purple Team FAQs
Can one person perform red, blue, and purple functions in a small organization?
Yes, in smaller setups, a single cybersecurity professional may switch between roles. However, juggling offensive, defensive, and collaborative tasks risks oversight and fatigue. Use automation tools like BAS platforms to fill gaps. Outsourcing Red or Purple functions periodically can maintain effectiveness without expanding headcount.
Is Purple Teaming a permanent team or a temporary initiative?
Purple Teaming is more a function than a fixed team. It often begins as a time-bound engagement but can evolve into a continuous practice. Typically led by a security architect or SOC lead, it bridges red and blue efforts to ensure lessons translate into actionable defence improvements.
How frequently should a Red Team engagement be conducted?
Most enterprises benefit from Red Teaming at least once or twice a year. However, the ideal frequency depends on your risk profile, regulatory environment, and exposure to evolving threats. Continuous validation through BAS or frequent simulations ensures your defences are always a step ahead.
How do I measure the ROI of Purple Teaming?
Track metrics like reduced detection and response times, closure of exploitable paths, and improvements in alert accuracy. A successful Purple Team effort also lowers repeat vulnerabilities and enhances cross-team collaboration. Ultimately, ROI is measured in resilience, readiness, and fewer costly breaches.