Red Teaming vs VAPT is a conversation most cybersecurity leaders have encountered. CISOs, CXOs and IT heads hear these terms frequently during audits, vendor discussions and internal security reviews. Yet confusion remains. Many organisations use the terms interchangeably, while others struggle to decide which exercise they actually need.
From our experience, both Vulnerability Assessment and Penetration Testing and Red Teaming form core pillars of a mature cybersecurity programme. We have pitched and delivered these services across organisations of different sizes and industries. What we have learned is simple. These exercises are not competitors. They solve different problems.
Understanding the difference helps stakeholders set the right expectations, allocate budgets wisely and gain meaningful security outcomes. This guide breaks down how these approaches differ, where they overlap and how to use them together.
Why your security strategy needs the power of both
Every security programme begins with visibility. You need to know what weaknesses exist and how attackers could exploit them. VAPT provides this baseline.
Red Teaming, on the other goes further. It tests whether your people, processes and controls can detect and respond to real attacks.
Security leaders must recognise that no single exercise offers complete assurance. VAPT identifies weaknesses. Red Teaming measures resilience. Together, they help organisations move from reactive security to informed risk management.
This distinction sits at the heart of the Red Teaming vs VAPT discussion.
What VAPT really focuses on
Vulnerability Assessment and Penetration Testing focus on discovering and validating security weaknesses. The goal is to identify what can go wrong and how severe the impact could be.
VAPT typically follows a defined scope. Assets, applications and environments are agreed upfront. Testing combines automated scanning with manual validation. The outcome is a prioritised list of vulnerabilities, exploitation paths and remediation guidance.
VAPT answers questions like:
- What vulnerabilities exist in our systems?
- Can these weaknesses be exploited?
- How serious is the risk if they are abused?
For many organisations, VAPT is the foundation of security hygiene. It supports compliance, audit readiness and continuous improvement.
What red teaming really focuses on
Red Teaming simulates real world attacks. The objective is not to find every vulnerability. Instead, it aims to test whether attackers can achieve a goal without being detected or stopped.
Red Team exercises are intelligence driven. They often operate with limited prior knowledge and minimal constraints. Attack paths evolve dynamically based on defender responses. This makes the exercise unpredictable and closer to real threat behaviour.
Red Teaming answers different questions:
- Can attackers breach our defences unnoticed?
- How effective are our detection and response capabilities?
- How well do teams collaborate under pressure?
This is why Red Teaming vs VAPT should not be framed as a choice. They serve distinct purposes within a security strategy.
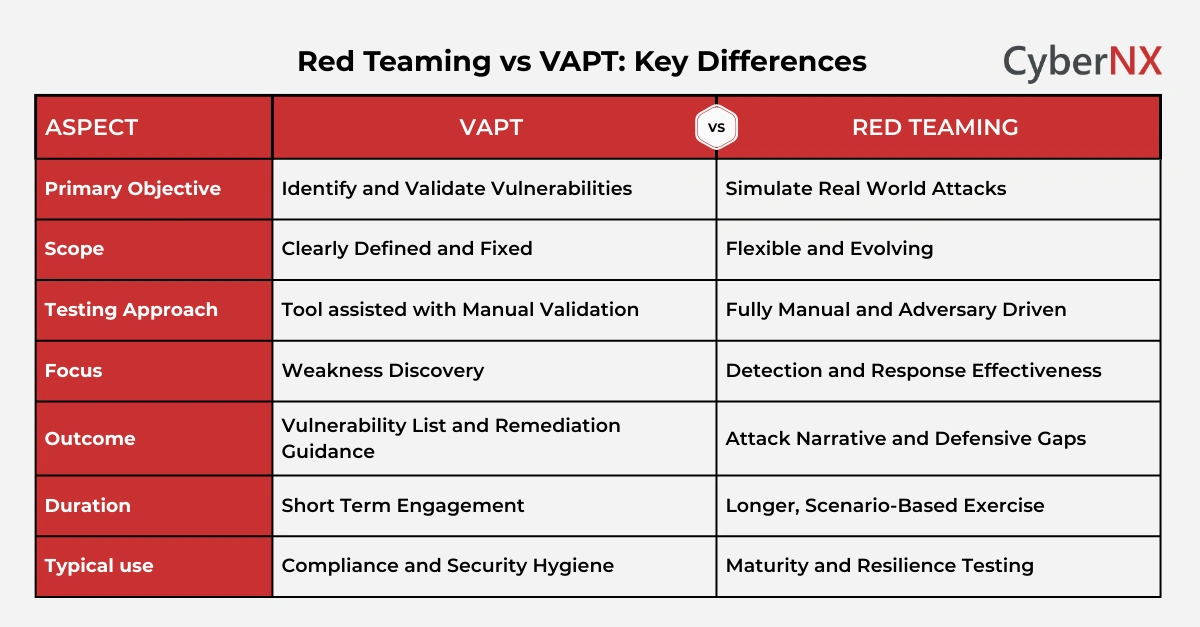
Key differences between red teaming and VAPT
The table below summarises the core differences between Red Teaming vs VAPT in a concise and practical way.
This comparison helps stakeholders understand why Red Teaming vs VAPT decisions must align with security goals, not assumptions.
When VAPT makes the most sense
VAPT is ideal when organisations need clarity on exposure. It works best during early security stages or when environments change frequently.
Common use cases include:
- New application launches
- Infrastructure upgrades
- Compliance audits
- Regular security health checks
VAPT delivers measurable output. It highlights where fixes are required and helps teams prioritise remediation. For many organisations, this is the first step towards reducing attack surface.
However, VAPT alone cannot assess how security controls perform under real attack conditions. This is where Red Teaming adds value.
When red teaming makes the most sense
Red Teaming becomes relevant when basic controls are already in place. Organisations use it to validate assumptions and challenge confidence.
Typical scenarios include:
- Mature security programmes
- Incident response readiness testing
- Board level assurance exercises
- Post breach reviews
Red Teaming does not aim to expose every weakness. It focuses on impact. It shows how attackers could reach critical assets and whether defenders notice in time.
This distinction reinforces why Red Teaming vs VAPT should be seen as complementary rather than competitive.
Why stakeholders must understand the difference
We have seen organisations invest heavily in one exercise while expecting outcomes from the other. This mismatch leads to frustration.
Decision makers must understand:
- VAPT improves technical posture
- Red Teaming tests operational resilience
Both insights matter. Without VAPT, blind spots remain. Without Red Teaming, false confidence grows. Educating stakeholders on Red Teaming vs VAPT helps align expectations with reality.
How VAPT and red teaming work together
Strong security programmes layer controls. VAPT and Red Teaming fit naturally into this layered approach.
A typical progression looks like this:
- Use VAPT to reduce vulnerabilities
- Strengthen controls based on findings
- Conduct Red Teaming to test detection and response
- Refine processes and repeat
This cycle builds resilience over time. Each exercise informs the next. This is why we consistently position both services as long term investments rather than one off activities.
How CyberNX approaches red teaming and VAPT
As a CERT-In empanelled cybersecurity firm, we help organisations decide what they need and when. We have provided both VAPT and red teaming services across industries, from BFSI, fast growing technology firms to regulated enterprises and foreign entities.
Our approach starts with understanding risk appetite and maturity. We explain the trade-offs clearly. If VAPT is sufficient, we say so. If Red Teaming adds value, we define objectives carefully.
We believe small, focused exercises often deliver better outcomes than broad, unfocused ones. Clear scoping and honest conversations make all the difference.
Conclusion
Red Teaming vs VAPT is not about choosing one over the other. Both are essential pillars of an effective cybersecurity programme. VAPT provides visibility. Red Teaming validates resilience.
Understanding their differences helps stakeholders make informed decisions, manage risk effectively and build confidence in their defences. When used together, these exercises move organisations closer to real security, not just perceived safety.
If you want help deciding how our VAPT services and Red Teaming fit into your security roadmap, speak with our experts today. We work alongside your team to design exercises that deliver clarity, not confusion.
Red teaming vs VAPT FAQs
Can small organisations benefit from red teaming?
Yes, but timing matters. Smaller teams often benefit more from focused VAPT before moving to Red Teaming.
Does red teaming replace compliance driven testing?
No. Compliance usually requires VAPT. Red Teaming supports resilience, not audit evidence.
How often should red teaming be performed?
Most organisations conduct it annually or after major security changes.
Is red teaming more expensive than VAPT?
Typically yes, due to its manual, scenario-based nature and longer duration.