If you are an IT security leader trying to decide between red teaming and penetration testing, the decision can be deceptively complex. Both sound similar and both test your defences. But here’s the thing to keep in mind: their intent, execution and outcomes are very different. Understanding the real differences is critical to choosing the right strategy for your organization’s risk posture, compliance needs and security maturity.
Red Teaming vs Penetration Testing
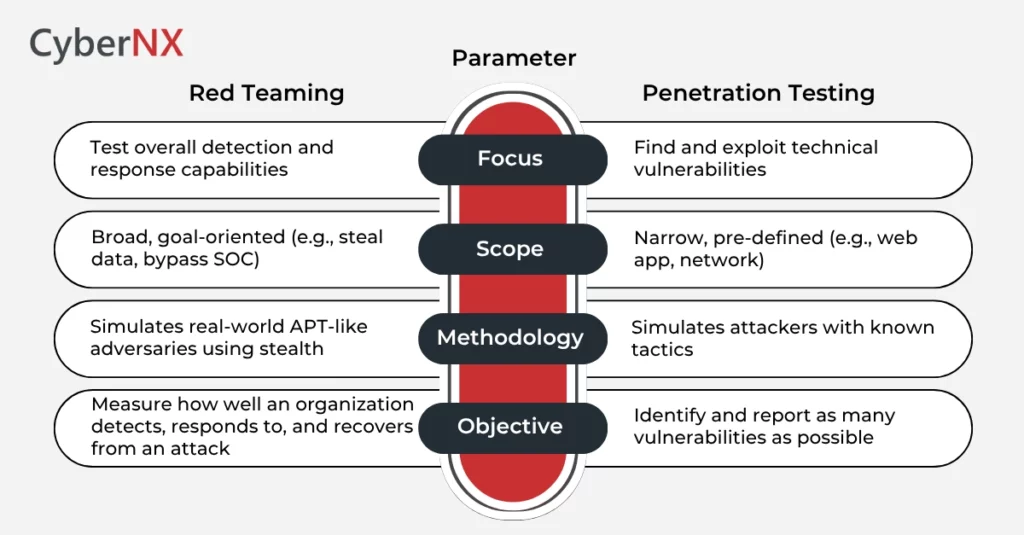
Here is a quick overview before delving into the specifics:
What is Red Teaming?
Red Teaming is a cybersecurity exercise or practice, influenced and adopted from wargaming in military. Organizations partner with red teaming experts or red teamers and authorize them to simulate cyberattacks against their systems, networks, applications and across the IT environment.
The goal is to assess how well your organization can detect and respond to a real world, stealthy, adversarial attacks. Red teaming does not have limits. The red teamers get into the shoes of a persistent threat actor and literally go berserk, exfiltrating data or gaining domain admin privileges.
The full-scope adversarial simulation tests technology, personnel and processes. To achieve this objective, tactics, techniques, and procedures (TTPs) of real attackers are used. Physical red teaming and social engineering techniques are also deployed. And one more thing; only IT security leaders, CEOs or leadership is informed about red teaming. Internal security team or blue team is not kept in the loop to understand the defence and response capabilities of the organization.
This is just the surface, find everything about this security practice in our blog Red Teaming Guide.
Real World Example of Red Teaming
Assume that a global financial services company requested a red team exercise to evaluate its real-world response readiness. The red team will launch a spear-phishing campaign, compromise a user’s endpoint, move laterally across the network and eventually gain access to sensitive customer records.
Depending on the threats faced by the firm, red teaming exercise may conduct tabletop exercises, pentesting, physical security and even look at insider threats and intelligence services.
All the activities will be carried out without triggering SIEM alerts or raising any internal security alarms.
The final report consisting of sensitive data as proof will highlight blind spots in monitoring, weak internal segmentation and delayed response protocols within the organization.
What is Penetration Testing?
Penetration testing or pen testing, when compared to red teaming has limited scope. Moreover, the controlled security test evaluates exploitable vulnerabilities in digital assets assigned or predefined by the organization.
Pen testers use automation to scan for vulnerabilities. Manual experts then use tools to assess, uncover and exploit vulnerabilities in a specific, targeted systems. This could be web application, internal network, API or something else, usually under well-defined rules of engagement.
The aim here is to identify weaknesses before real attackers do. The process is repeatable, methodical, and mapped against known frameworks like OWASP Top 10 or ATT&CK MITRE for specific layers.
Find a more detailed explanation with our blog Penetration Testing Guide.
Real World Example of Penetration Testing
Assume a SaaS provider company must undergo annual compliance and opts for penetration testing services to evaluate its customer portal. The pen testers while testing find a misconfigured access control vulnerability that allows unauthorized access to customer data. Within a week, the issue is patched, and the retest is done to validate the fix. This eventually helps the client meet its regulatory deadline.
Red Team vs Penetration Test: 5 Key Differences Explained
Here’s a deeper dive into the difference between red team and penetration test:
1. Evaluation Objective
Pentest is focused on identifying technical flaws in a specific component like apps, systems or networks. Red Team assesses the overall security posture of the organization and how prepared you are against a coordinated, stealthy and modern threat actor.
2. Collaboration Scope
Pentesting usually involves collaboration with internal IT or security teams. And of course, the senior leadership will know all about it. A detailed scope is always documented before the real work starts.
Red Teams conduct the operations covertly. This means without the knowledge of defenders to maintain realism. However, the senior leadership and security leaders are always kept in the loop. The red teaming exercise usually takes a long time as they check how long they can stay in the system without being caught.
3. TTPs and Methodologies
Pentesting team use common vulnerability scanning and exploitation tools to uncover flaws and report the vulnerabilities to the internal security teams. Red Team mimics real-world threat actors in the extreme ways possible (within the scope allowed). They use phishing, social engineering, privilege escalation, lateral movement and evasion tactics.
4. Security Maturity Fit
Pen testing is ideal for organizations beginning to build their security posture or meet compliance. Red teaming, on the other hand, is best suited for mature organizations looking to validate their defence-in-depth strategy.
5. Time Taken
While pentesting typically spans a few days to a week, red teaming usually takes several weeks or even months to execute end-to-end.
Red Team vs Penetration Test: How to Make the Choice?
Choosing between red teaming and penetration testing depends on your current security maturity, business priorities and budget.
Use Penetration Testing if:
- You need to check off compliance boxes (PCI-DSS, SOC 2, ISO 27001).
- You want a clear list of vulnerabilities with fixes.
- You’re early in your cybersecurity maturity journey.
Use Red Teaming if:
- You want to evaluate incident response effectiveness.
- You’re facing high-risk threats like APTs.
- You’ve already addressed most known vulnerabilities.
Red Teaming vs Penetration Testing
| USE CASE | RECOMMENDED APPROACH |
| Regulatory compliance | Penetration Testing |
| Evaluate SOC readiness | Red Teaming |
| Simulate real-world APT | Red Teaming |
| Identify specific app flaws | Penetration Testing |
| Test blue team response | Red Teaming |
| Periodic risk assessments | Penetration Testing |
Red Teaming vs Penetration Testing: Do They Complement Each Other?
Absolutely. In fact, they work best when used together. Penetration testing strengthens your systems by identifying weaknesses, while red teaming tests whether your detection and response capabilities can catch an advanced adversary. Using both in rotation creates a balanced offensive and defensive strategy that evolves with your threat landscape.
Conclusion
Red teaming and penetration testing are both essential. One gives you tactical vulnerability insights and the other tests your strategic resilience. As an IT security leader, the key lies in understanding your organization’s maturity and goals.
Start with penetration testing if you need to strengthen your technical perimeter. Move to red teaming when you are ready to challenge your people, processes and overall incident response readiness.
And in case you are looking for strongest defence, we provide red teaming services as well as penetration testing services. Our experts will help you use both, strategically and continuously, boosting your organizational defence. Contact us today.
Red Teaming vs Penetration Testing FAQs
Can penetration testing evolve into red teaming as an organization matures?
Yes. Many organizations begin with penetration testing to find and fix surface-level vulnerabilities. As they mature, they incorporate red teaming to simulate more advanced, persistent threats and test detection and response capabilities.
Is red teaming suitable for startups or small businesses?
Generally, no. red teaming is resource-intensive and best suited for organizations with established security teams, monitoring tools, and a mature incident response process. Startups should begin with basic penetration testing.
Do red teamers also provide a list of vulnerabilities like penetration testers?
Not usually. Red teaming focuses on demonstrating how an attacker can achieve objectives by chaining together flaws. The report is often narrative-driven and highlights strategic gaps, not just technical ones.
How often should red teaming and penetration testing be conducted?
Penetration testing is typically done annually or after major infrastructure changes. Red teaming may be conducted once or twice a year, especially after strengthening blue team capabilities or deploying new detection tools.