Organizations often miss detecting sophisticated cyberattacks. That’s not because they lack tools. There are advanced tools and now AI to help security teams. But the professionals are unable to get insights about how attackers actually think.
This is where the real power of Red Teaming lies. The cybersecurity technique shows if your organization is vulnerable. Plus, how an adversary would exploit your systems, people, processes and established assumptions. And unless you understand the methodology behind Red Teaming, you won’t be able to extract its full strategic value.
In this blog, we explore the Red Teaming testing methodology that makes the exercise so critical for modern defence.
What is Red Teaming Testing Methodology?
Red Teaming testing methodology is a structured and goal-based cybersecurity exercise, designed to simulate a real-world attack. It combines technical exploitation along with social engineering, physical intrusion and behavioural psychology to challenge your organization’s security defence.
Red Teaming, in effect, replicates an actual adversary’s cyberattack campaign, from long-term reconnaissance to silent data exfiltration, without tipping off your defenders. If you have already locked in a red teaming service provider, you can expect the methodology discussed here to be followed. Each step is deliberate, designed to expose blind spots, challenge assumptions and provide insights into your cyber defence and resilience.
Go into the details of red teaming process, types, benefits and more with our blog Red Teaming Guide.
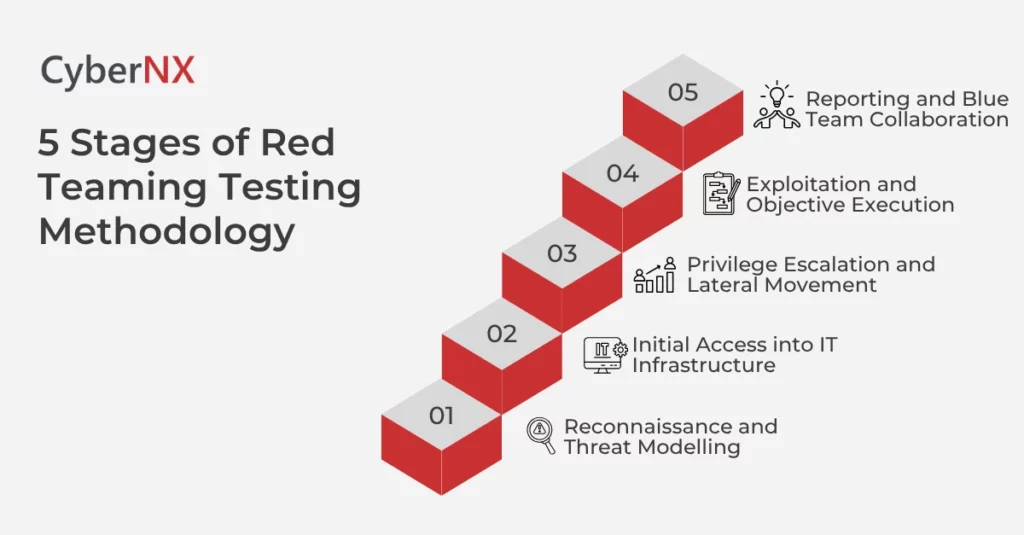
The Five Core Stages of the Red Teaming Testing Methodology
While variations may exist depending on business context, business objectives and threat models, most red teaming testing methodologies follow the structured flow discussed here:
1. Reconnaissance and Threat Modelling
This is where the groundwork begins. Red Teams gather intelligence. Both passive and active reconnaissance is involved to find information about your organization’s assets, personnel, technologies and supply chains. The aim is to simulate how an external attacker would profile your environment. It includes public-facing and internal assets.
This initial stage defines the narrative: who the attacker is, what they want and how they might try to get it.
Examples of reconnaissance include:
- Scraping public employee data (OSINT)
- Mapping out infrastructure using DNS, IP ranges, or SSL certs
- Studying third-party relationships
A threat model is then created to guide the red teaming operation. It is a digital blueprint of plausible attack paths.
2. Initial Access into IT Infrastructure
Once the IT infrastructure terrain is mapped, Red Teams attempt to breach the perimeter. This stage tests the loopholes in your first line of defence.
Common techniques:
- Spear phishing to gain initial foothold
- Exploiting known vulnerabilities in public-facing assets
- Bypassing MFA through social engineering or session hijacking
Here, subtlety is key. Success of red teaming is measured by silent entries that go undetected by SIEM tools and SOC.
3. Privilege Escalation and Lateral Movement
After access is obtained, Red Teams elevate privileges, often impersonating legitimate users, and pivot through the environment.
This phase assesses:
- How well you segment your internal network
- How securely you manage credentials
- How your SOC distinguishes noise from signal
Sometimes, red teamers will impersonate a system admin, exploit weak configurations and extract cached credentials, copying how a skilled adversary will enact this.
4. Exploitation and Objective Execution
Red Teams are always assigned specific objectives by security leaders. This can be stealing intellectual property, exfiltrating sensitive data or compromising privileged accounts. Exploitation stage involves techniques to do exactly that.
This goal-oriented approach sets Red Teaming apart from traditional penetration testing. It evaluates your organization’s capacity to:
- Detect suspicious activity
- Respond effectively
- Contain and recover
At this point, it is important to note that physical intrusions are also a part of red teaming methodology. A team member may try to get inside the office building and steal information from unlocked PCs or sensitive documents.
5. Reporting and Blue Team Collaboration
The final phase is where your organization gets the most value from. The whole exercise which sometimes takes months concludes. Findings are consolidated, attack chains reconstructed, and insights delivered with clarity and context.
A well-executed debrief will include:
- Timeline of the attack
- Detection gaps and response time
- Missed alerts and misconfigured tools
- Strategic recommendations
Importantly, Red Teams work with your Blue Team (most often in-house security teams or SOC) to simulate incident response, improve playbooks and boost the overall defence posture.
Conclusion
Red Teaming is a powerful cybersecurity technique to detect security issues because of its wide scope. Plus, it gives a crystal-clear picture of an organization’s existing security standing in the face of modern threats.
If you are a CISO, CTO or CEO, knowing the methodology empowers you to:
- Ask the right questions post-engagement
- Align security spend with actual attack paths
- Embed threat-informed defence into long-term planning
Our red teaming services with certified professionals and advanced technology and techniques, can help you protect what matters most – the critical digital assets in the organization. Contact us today.
Red Teaming Testing Methodology FAQs
How long does a typical Red Team engagement last?
Most Red Team operations span 4 to 12 weeks, depending on the complexity of objectives, target size, and need for stealth. Longer durations mimic real APT timelines.
Can Red Teaming testing methodology not include physical intrusion?
Yes, but including physical access provides a more holistic assessment. Many successful breaches begin with overlooked physical vulnerabilities.
How do Red Teams avoid triggering alarms during an engagement?
They use advanced evasion techniques – custom payloads, timing attacks, non-standard ports, and behavioural mimicry – to stay under the radar of your EDR and SIEM.
What’s the difference between a Red Team and a Pen Test in terms of methodology?
Penetration tests focus on known vulnerabilities with limited scope. Red Teaming is goal-driven, often without prior knowledge, and emulates real adversaries using custom strategies, persistence, and deception.