Assess Your Cyber Defence Capabilities with
Red Teaming Services
With our full adversarial assessments, you can test how well your company can handle cyberattacks.
Talk to our Experts Today





















INTRODUCTION
Highly Efficient Red Teaming Services from CyberNX
Simulating real-world cyber dangers as part of red teaming is a proactive way to find and fix security holes. To find weak spots in your important assets, our professionals use methods like role-based social engineering, application and network penetration testing, and client-side attacks.
We address your key challenges:
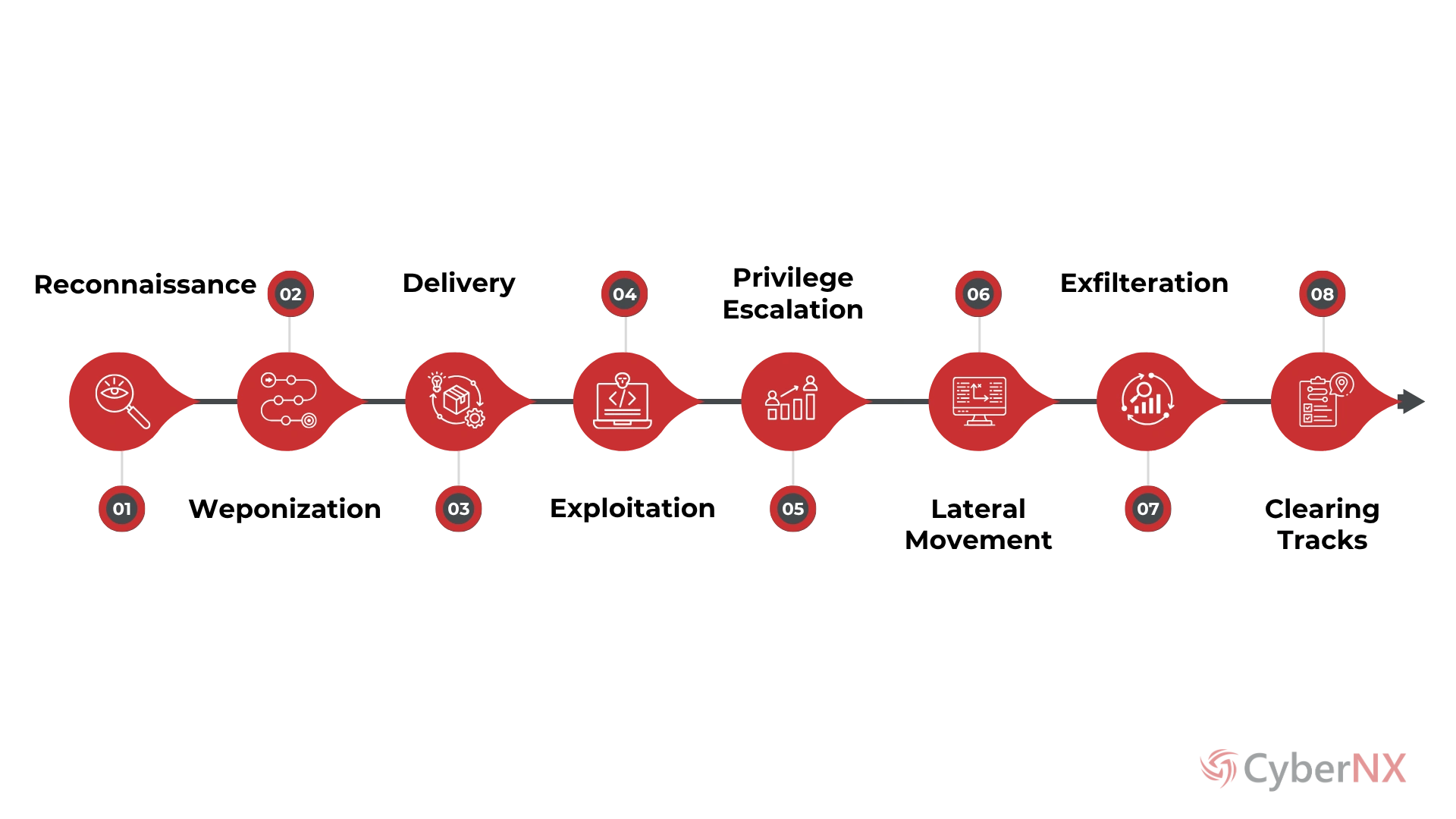
PROCESS
How It Works?
Looking for Red Teaming Services? Connect with our Team of Security Specialists!
APPROACH
What Makes CyberNX Different from Other Red Teaming Service Providers?
Cutting-Edge Tools
Using the newest red teaming tools to do assessments that are specific to the customer’s surroundings.
Offensive Security Tactic
Updated knowledge about latest data breaches are used to test complete cybersecurity controls.
CERT-IN Empanelled
Recognised by CERT-IN, our team follows best practices and standards to perform red teaming.
Intelligence-led Testing
Global intelligence helps us deploy stealth techniques used by cyber attackers in engagements.
Multiple Attack Methods
Social engineering, pentesting and other diverse methods are used to meet the red teaming objective.
Regulatory Compliance
A detailed report offers complete overview of the exercise. Plus, you meet CERT-IN, SEBI & RBI standards.
Customer first Approach is our guiding principle.
BENEFITS
Real-World Hacker-style Red Team Testing Services
Test Security Team Effectiveness
Check out how well your security team handles cyberattacks and make a list of their strengths and weaknesses.
Data and Infrastructure Compromise Assessment
Figure out how hard it would be for attackers to get into sensitive data or IT infrastructure. This will help you decide which security steps to take first.
Vulnerability Identification and Mitigation
Find and fix complicated security holes before they can be used, which lowers the chance of successful breaches.
Risk Analysis based on Facts
Get a risk analysis based on facts along with suggestions for how to make things better. This will help you understand your organization's risk exposure and decide how to best reduce it.
Executive Summary
Get a high-level executive summary from the Red Team Assessment that is written for executives and top management and includes the most important findings and suggestions.
Detailed Assessment Report
Get a thorough report that lists all the vulnerabilities that were found and what steps were taken during the assessment. This will help you understand the security posture and where it is weak.
Strategic Recommendations
Get long-term improvement suggestions that will help you build a strong security plan that will protect you from both current and future threats.
For Customized Plans tailored to Your Needs,
Get in Touch Today!
FAQ
Frequently Asked Questions
Red Teaming is a proactive approach to assessing cybersecurity defences. It involves ethical hackers simulating real-world cyber-attacks to identify vulnerabilities and weaknesses in an organization’s infrastructure, applications, and security processes.
Red Teaming provides a comprehensive view of an organization’s security posture by simulating realistic attack scenarios. This helps identify and address security gaps before they can be exploited, reducing the risk of data breaches and other cyber threats.
Yes, CyberNX is a CERT-IN Empanelled Red Teaming Vendor. We adhere to all requirements and best practices for testing and reporting as mandated by CERT-IN.
Red Teaming offers a realistic assessment of cybersecurity defences. By simulating real-world attacks, it identifies vulnerabilities that traditional testing might miss. This helps organizations strengthen their security posture, improve incident response, and mitigate the risk of cyber-attacks.
RESOURCES
