In the relentless battle against cyber threats, CISOs, CXOs, and IT Managers are constantly seeking ways to fortify their organization’s defences. One critical component of a robust cybersecurity strategy involves the Red team vs Blue team method.
But beyond the buzzwords, you should have a good grasp on the distinct roles and collaborative potential of red team and blue team in cybersecurity. Also, question arises – are you leveraging offensive security to expose weaknesses or relying solely on defensive measures?
This blog will demystify the essential differences between these two vital teams. It will equip you with the knowledge to optimize your cybersecurity posture and stay ahead of evolving threats.
What is the Red Team in Cybersecurity?
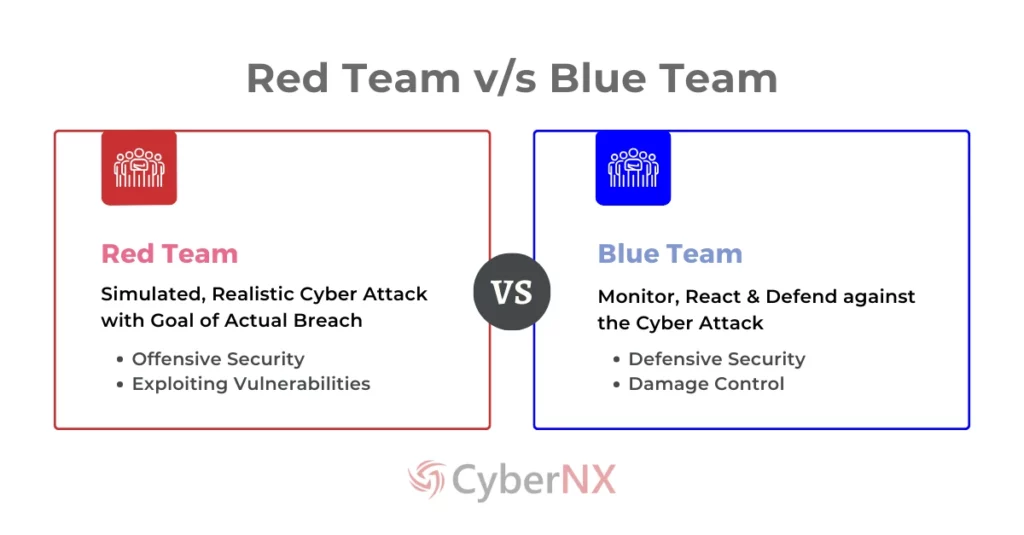
The red team is your organization’s ethical hacking squad. Think of them as the “attackers” who simulate real-world cyberattacks to identify vulnerabilities in your systems. They challenge an organization’s security posture by attempting to bypass its defences.
A red teamer is a security professional with deep expertise in penetration testing, social engineering, and exploit development. That’s why red team job titles range from ethical hacker and social engineering specialist to creative exploit developer and adversary emulation specialist. Red teamers also get certifications like SANS, EC-Council and Offensive Security Certifications.
Pros of Red Teaming
The main advantage of red teaming is that it tries to evade blue team, exposing organization’s security defences.
- Proactively identifies hidden vulnerabilities.
- Provides a realistic assessment of security effectiveness.
- Helps improve incident response capabilities.
Cons of Red Teaming
Red teaming exercise is time consuming, intense and need experts who could handle everything carefully. Not every organization has the will to opt for it.
- Can be disruptive if not managed properly.
- Requires significant expertise and resources.
We have covered the subject in substantial depth in our blog Red Teaming Guide. Read!
What is the Blue Team in Cybersecurity?
The blue team in cyber security represents the defenders. Their mission is to protect the organization’s assets by monitoring, detecting, and responding to cyber threats. It is the internal security team responsible for maintaining the organization’s defensive posture.
A blue teamer is a security professional skilled in network monitoring, incident response, and security information and event management (SIEM). A blue team job roles include Threat hunter, incident responder and sometimes SOC analyst and Compliance officer. Blue teamers do many certifications such as CISSP, CISA, GSEC, GCIH and SSCP.
Pros of Blue Teaming
Blue teaming aims to know red teaming techniques and defend against everything red teamers throw at them. This is done to ensure effective security for your organization.
- Ensures continuous monitoring and threat detection.
- Minimizes the impact of cyberattacks.
- Strengthens overall security infrastructure.
Cons of Blue Teaming
Here are some possible disadvantages of blue teaming exercise which makes organizations hesitant to use it:
- Can be reactive if not proactive.
- Requires constant updates to stay ahead of evolving threats.
- May struggle with complex or zero-day attacks.
This is an overview. For full break down on the topic, read our blog Blue Team Guide.
Key Differences Between Red Team vs Blue Team in Cybersecurity
Here’s a comparison to clarify the red team services vs blue team services cybersecurity dynamics:
| Feature | Red Team (Offensive Security) | Blue Team (Defensive Security) |
| Objective | Identify vulnerabilities and test security effectiveness. | Protect assets, detect threats, and respond to incidents. |
| Role | Simulate cyberattacks. | Monitor, defend, and remediate. |
| Approach | Proactive, offensive. | Reactive and proactive, defensive. |
| Techniques Used | Penetration testing, social engineering, exploit development. | Network monitoring, SIEM, incident response, vulnerability scanning. |
| Skills | Penetration testing, exploit development, social engineering, scripting. | Network monitoring, incident response, SIEM, log analysis, forensics. |
| Tools | Metasploit, Nmap, Burp Suite, Kali Linux, custom scripts. | Splunk, ELK Stack, Wireshark, CrowdStrike, firewalls, IDS/IPS. |
| Advantages | Uncovers hidden weaknesses, realistic testing. | Continuous monitoring, rapid incident response. |
| Disadvantages | Potentially disruptive, resource-intensive. | May struggle with advanced attacks, can be reactive. |
| Collaboration with Other Teams | Brief interaction, focused on results. | Continuous interaction, collaborative defense. |
| Key Metrics | Number of vulnerabilities found, success rate of attacks. | Time to detect and respond to incidents, reduction in security incidents. |
| End Goal | Improve overall security posture by identifying weaknesses. | Maintain a secure and resilient environment. |
In essence, cybersecurity attack & defence strategies of the red & blue team are complimentary. The red team breaks things to find the cracks, while the blue team patches them up.
Why Red vs Blue Team Method is Important for Organizations?
Red Team vs Blue Team security practice is vital for building cyber resilience. One attacks to expose weaknesses; the other defends to strengthen systems. Together, they create a dynamic feedback loop that enhances threat detection, response, and long-term security posture.
- Proactive Security: They help identify vulnerabilities before malicious actors do.
- Improved Incident Response: They enhance the ability to quickly and effectively respond to cyberattacks.
- Enhanced Security Awareness: They raise awareness about security risks and best practices.
- Regulatory Compliance: They help organizations meet compliance requirements related to security.
Organizations significantly strengthen security posture by leveraging both offensive and defensive strategies. The red team vs blue team strategy also reduces the risk of costly breaches and ensures business continuity.
How Red and Blue Teams Work Together?
The true power of red team blue team simulation emerges when they collaborate closely. This synergy is where the purple team cyber security concept shines. Think of it as a dynamic feedback loop, enhancing your organization’s security posture in real-time.
Collaborative Importance:
When red and blue teams share their insights and findings, it creates a powerful learning environment. The red team’s attack simulations reveal vulnerabilities, while the blue team’s defense strategies show what works and what doesn’t. This open exchange drives continuous improvement and strengthens your overall security.
Purple Teaming Concept:
Imagine a scenario where the red team launches an attack, and the blue team observes and responds in real-time. That’s the essence of purple teaming. This collaborative approach allows for instant feedback, knowledge transfer, and rapid adjustments to security controls, making your defenses more agile and effective.
Best Practices for Integration:
- Establish regular meetings where both teams can discuss findings and strategies.
- Use shared tools and platforms to facilitate communication and knowledge sharing.
- Cultivate a culture of open communication where both teams feel comfortable sharing their perspectives.
Benefits of a Red Team & Blue Team Partnership
A Red and Blue Team partnership fosters continuous improvement by combining offensive insights with defensive refinement. This synergy helps organizations uncover blind spots, reduce response times, and build stronger, more adaptive security frameworks.
1. Identifying Vulnerabilities
The red team’s simulated attacks go beyond automated scans, uncovering complex vulnerabilities that might otherwise remain hidden. By combining these findings with the blue team’s in-depth system knowledge, organizations gain a holistic understanding of their weaknesses, leading to more targeted and effective remediation.
2. Enhanced Threat Detection
The red team’s insights into attack tactics enable the blue team to fine-tune their monitoring and detection systems. Blue teams can develop more accurate and timely alerts, reduce false positives and improve their ability to identify genuine threats.
3. Faster Incident Response
When an incident occurs, a collaborative approach ensures a swift and coordinated response. The red team’s knowledge of attack vectors helps the blue team quickly contain the damage and restore systems. This streamlined approach minimizes downtime and reduces the overall impact of the incident.
4. Strengthened Cyber Defence
The continuous feedback loop between red and blue teams fosters a culture of continuous improvement. The red team’s findings drive the blue team to strengthen their defences, while the blue team’s experience informs the red team’s testing strategies. This iterative process results in a more robust and resilient security posture, capable of withstanding evolving cyber threats.
Scenarios When a Red Team/Blue Team Exercise Is Needed
Red Team/Blue Team exercises are crucial during major infrastructure changes, compliance audits, or after significant cyber incidents. They help validate defenses, assess real-world readiness, and uncover gaps before attackers can exploit them.
Red Teaming Scenarios
Typica red team scenarios are discussed below:
- Before a major system deployment.
- After a significant security incident.
- To test the effectiveness of new security controls.
- When regulatory compliance requires it.
Read our article covering 5 Real-World Red Team Scenarios.
Blue Teaming Scenarios
Here too, we discuss typically seen blue teaming scenarios:
- Continuous monitoring of critical systems.
- During and after a security incident.
- Regular vulnerability assessments.
- After the implementation of new security tools.
Conclusion
Organizations should integrate the offensive capabilities of the red team with the defensive prowess of the blue team. This will help build a resilient security posture. Once done effectively, it will be capable of withstanding sophisticated attacks.
If you want to understand how attackers might target your systems, our red team services can help. We also provide blue team services where our experts will help you with the tools and guidance needed to respond with confidence. Connect with us to see how both teams working together can strengthen your organisation.
Red Team vs Blue Team FAQs
What are the key indicators that my organization needs a red team engagement?
If you’re experiencing a rise in attempted breaches, preparing for a major system upgrade, or have concerns about the effectiveness of existing security controls, a red team engagement is highly beneficial. Also, if you have not had a red team assessment in a set amount of time, this could be a good reason to schedule one. Regular assessments are always a good idea.
How does a blue team enhance our incident response capabilities?
A strong blue team continuously monitors your network for suspicious activity, enabling rapid detection and containment of threats. They use SIEM systems, threat intelligence, and log analysis to identify anomalies and respond effectively, minimizing the impact of security incidents. They also document the incident, and create playbooks for future incidents.
What is the benefit of purple teaming over separate red and blue team exercises?
Purple teaming fosters real-time collaboration between red and blue teams, enabling immediate feedback and knowledge transfer. This dynamic approach allows for rapid adjustments to security controls and enhances the effectiveness of both teams. It drastically reduces the “time to improvement” window.
How can I measure the ROI of investing in red and blue team services?
ROI can be measured by reduced incident response times, fewer successful breaches, and improved compliance posture. Quantifiable metrics include the number of vulnerabilities identified and remediated, the time taken to detect and respond to incidents, and the reduction in security-related downtime. Also, the cost of a data breach prevented, far outweighs the cost of these services.
For a smaller organization, how can we implement red and blue team concepts without hiring dedicated teams?
Smaller organizations can leverage managed security service providers (MSSPs) for red and blue team functions. Also, cross-training existing IT staff to perform both offensive and defensive security tasks can be effective. Regular tabletop exercises and simulated attacks can also help build skills and awareness. You can also utilize free open source tools to start implementing these concepts.
Which is best, blue team or red team?
Both blue and red teams are equally important, and neither is ‘best’. An organization with only a red team will know its weaknesses but not be able to defend itself. An organization with only a blue team will be reacting to attacks that may have been prevented. The best security outcome is attained by utilizing both teams. This synergy is where the purple team cybersecurity concept shines.